Part 2: Capstone Project – InformationalThis part of the assignment is not for grading this week. This part of the assignment is to contribute to the Capstone project and also to show the instructor
Title Page
Course number and name
Project name
Names, project roles, and IT specialization for each team member
Date
Table of Contents (TOC)
Use an auto generated TOC.
This should be on a separate page.
Update the fields of the TOC so that it is up-to-date before submitting your project.
Individual Submissions:
Executive Summary (Week 5 - Individual Activity: 1-2 pages) Final Insights of Capstone Project (Week 5 - Individual Activity: 1 to 2 pages) Section One: Planning and System Requirements (Week 1: 5 to 7 pages)Project Overview
Verbania, Inc. is a corporation that’s on the wheels of reinvention. The company’s main business will be a social networking website and a mobile application that relates to the same. The company intends to have its headquarters in the Silicon Valley region in California. At the moment the corporation lacks the social networking website, the social networking mobile application, computers and network infrastructure. The corporation realizes that in order for it to stay on top of its competitors, it needs to come up with a social networking platform for web and mobile application that will facilitate the collection, storage, back up and mining of user data in order to better understand users. It also needs to integrate collected data with customer relationship management (CRM) in order to improve business and customer support processes. It also needs to analyze user patterns, behavior, and generated traffic so as to present to advertisers. The user data will be stored in a database. Since the users will store and retrieve data across the network, security needs to be number one priority so as to prevent the social networking website from being hacked. The entire system needs to be built with security in mind, starting from the network infrastructure which has to have firewalls that checks incoming and outgoing packets to the social networking website that uses an encrypting technique to encrypt user passwords. The database should also be built with security in mind. The database should be able to allow only authorized users access of the data and also grant and revoke privileges to users.
Scope of the project
The scope of the project is to come up with:
Social networking website
One of the deliverable of the project will be a social networking website. The website should be able to facilitate various functionalities such as account setup and log-in functionality, user profile creation, addition and removal of friends from a user’s profile and posting to a discussion area. The social networking website will be beneficial for the users and the corporation on the following ways:
User’s perspective
From the user’s perspective, the user should be able to create an account and a profile, the user should be able to create a discussion forum and also post in that forum, the user should be able to perform a search of people. The website should also provide a gaming component for the user, a calendar and reminder component, instant messaging and Voice over Internet Protocol (VOIP)-type calling functionality between friends. The website should also be able to secure account and email feature and be available 24/7.
Corporation’s perspective
From the corporation perspective, the website should be able to store, back up, and mine user data so as to be able to understand the users. The website should also have an algorithm that can integrate collected data with Customer Relationship Management (CRM) so as to improve business and customer support processes. Lastly, the website should also have an algorithm that can analyze user patterns, behavior and generated traffic so as it can present it to advertisers.
Social networking mobile application
Another deliverable of the project will be a social networking mobile application. The corporation will come up with a social networking mobile application for Android, IOS and Windows platform. The mobile application will operate the same as the social networking website. This is to cater for people who usually download apps and use them using their phones.
Database system
Another deliverable of the project is a database. User data will be stored and retrieved from a database. Since the social networking website is intended to have a large volume of users, there will be a dedicated database server that will facilitate smooth operation of the corporation.
Computer and network infrastructure
Another deliverable of the project is the purchase of computers and installation of network infrastructure. Every department will have 30 computers and will share two printers that will be connected through the network. The network will be implemented using the tree topology or also known as expanded star topology. According to Winkelman R (2013), a tree topology combines characteristics of linear bus and star topologies. Winkelman R (2013) explains that it consists of groups of star-configured workstations connected to a linear bus backbone cable. Winkelman R (2013) adds that tree topology allows for the expansion of an existing network. We will use this topology because it facilitates expansion of a network. We will also purchase routers, switches, fibre optic cable, cross over and straight through cables, patch panels, RJ45 among other network equipment. The following screenshot depicts a diagrammatic representation of the network.
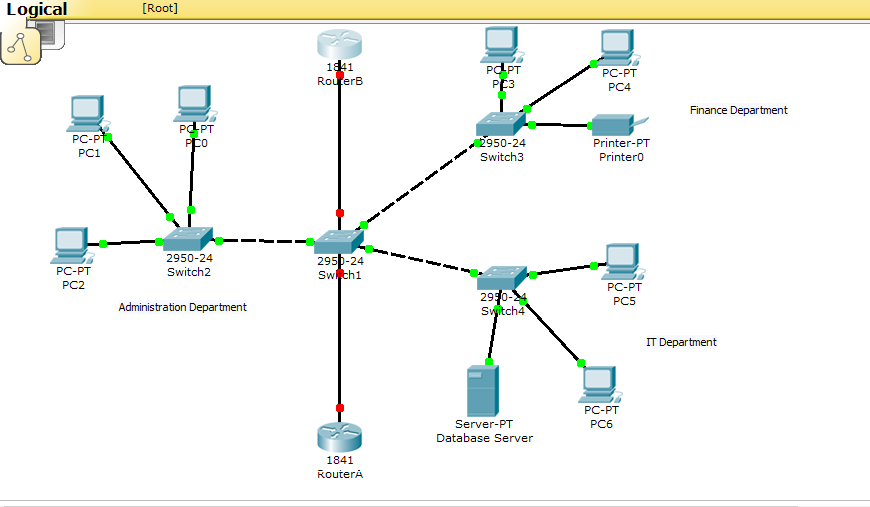
Security measures
Another deliverable of the project will be to ensure the entire system is built using security in mind. The network will have firewalls from both ends of the routers so as to check incoming and outgoing data. All workstations will have an antivirus installed and up to date. The database will facilitate encryption of passwords. Only the network administrators will be able to access the routers and switches and using a Secure Shell (SSH). Only the database administrators will be able to use the Data Definition Language (DDL), that is, only the database administrators have the right and privileges of creating, modifying and deleting tables and also database. All other users can only create and manipulate the data they create. End users can only access the system through the website and mobile application and they have limited rights and privileges. The network will be tested for security so as to check that cross site scripting (XSS) attack and SQL injection attack does not occur. Let us define XSS and SQL injection attacks.
According to Kallin J and Valbuena I (2016) cross-site scripting is a code injection attack that allows an attacker to execute malicious JavaScript in another user’s browser.
According to Porup J (2018) Structured Query Language (SQL) injection is a type of attack that can give an adversary complete control over your web application database by inserting arbitrary SQL into a database query.
Constraints and assumptions
The financial constraint that the company holds is that the entire project should not exceed the budget set aside of $800, 000.
The schedule constraint that the corporation holds is that the entire project should not exceed one year with purchase of computers and network installation beginning so as to make way for other phases because the other phases are dependent on this.
The corporation also holds that it will have its own database server and will not let third part companies access its data.
Scope control
The project manager will ensure that the project is going hand in hand with the documented deliverables and if changes arise, the Project Manager will communicate with the board of directors and see whether to include the changes and also amend the project documents.
Feedback:
Section Five: System Implementation and Maintenance (Week 5 - Individual Activity: 3 to 4 pages)
Feedback:
References
Porup, J. (2018). SQL injection explained: How these attacks work and how to prevent them. Retrieved from https://www.csoonline.com/article/3257429/application-security/what-is-sql-injection-this-oldie-but-goodie-can-make-your-web-applications-hurt.html
Winkelman, R (2013). Topology. Retrieved from https://fcit.usf.edu/network/chap5/chap5.htm
Valbuena, I. and Kallin, J. (2016). Excess XSS: A comprehensive tutorial on cross-site scripting. Retrieved from https://excess-xss.com/
10



