New Content for Week 3: System DesignFor this week’s contribution to the overall capstone project, collaborate and discuss with the team’s Security Specialist about the security and privacy of the
Capstone Project Activity
Table of Contents
Executive Summary (Week 5 - Individual Activity: 1-2 pages) 3
Final Insights of Capstone Project (Week 5 - Individual Activity: 1 to 2 pages) 3
Section One: Planning and System Requirements (Week 1: 5 to 7 pages) 4
Section Two: System Analysis (Week 2: 6 to 8 pages) 9
Section Three: System Design (Week 3: 5 to 7 pages) 17
Section Four: System Development (Week 4 - Final Submission: 8 to 10 pages) 17
Assumptions: 17
Feedback: 17
Section Five: System Implementation and Maintenance (Week 5 - Individual Activity: 3 to 4 pages) 18
Assumptions: 18
Feedback: 18
Individual Submissions:
Executive Summary (Week 5 - Individual Activity: 1-2 pages) Final Insights of Capstone Project (Week 5 - Individual Activity: 1 to 2 pages) Section One: Planning and System Requirements (Week 1: 5 to 7 pages)Project Overview
Verbania, Inc. is a corporation that’s on the wheels of reinvention. The company’s main business will be a social networking website and a mobile application that relates to the same. The company intends to have its headquarters in the Silicon Valley region in California. At the moment the corporation lacks the social networking website, the social networking mobile application, computers and network infrastructure. The corporation realizes that in order for it to stay on top of its competitors, it needs to come up with a social networking platform for web and mobile application that will facilitate the collection, storage, back up and mining of user data in order to better understand users. It also needs to integrate collected data with customer relationship management (CRM) in order to improve business and customer support processes. It also needs to analyze user patterns, behavior, and generated traffic so as to present to advertisers. The user data will be stored in a database. Since the users will store and retrieve data across the network, security needs to be number one priority so as to prevent the social networking website from being hacked. The entire system needs to be built with security in mind, starting from the network infrastructure which has to have firewalls that checks incoming and outgoing packets to the social networking website that uses an encrypting technique to encrypt user passwords. The database should also be built with security in mind. The database should be able to allow only authorized users access of the data and also grant and revoke privileges to users.
Scope of the project
The scope of the project is to come up with:
Social networking website
One of the deliverable of the project will be a social networking website. The website should be able to facilitate various functionalities such as account setup and log-in functionality, user profile creation, addition and removal of friends from a user’s profile and posting to a discussion area. The social networking website will be beneficial for the users and the corporation on the following ways:
User’s perspective
From the user’s perspective, the user should be able to create an account and a profile, the user should be able to create a discussion forum and also post in that forum, the user should be able to perform a search of people. The website should also provide a gaming component for the user, a calendar and reminder component, instant messaging and Voice over Internet Protocol (VOIP)-type calling functionality between friends. The website should also be able to secure account and email feature and be available 24/7.
Corporation’s perspective
From the corporation perspective, the website should be able to store, back up, and mine user data so as to be able to understand the users. The website should also have an algorithm that can integrate collected data with Customer Relationship Management (CRM) so as to improve business and customer support processes. Lastly, the website should also have an algorithm that can analyze user patterns, behavior and generated traffic so as it can present it to advertisers.
Social networking mobile application
Another deliverable of the project will be a social networking mobile application. The corporation will come up with a social networking mobile application for Android, IOS and Windows platform. The mobile application will operate the same as the social networking website. This is to cater for people who usually download apps and use them using their phones.
Database system
Another deliverable of the project is a database. User data will be stored and retrieved from a database. Since the social networking website is intended to have a large volume of users, there will be a dedicated database server that will facilitate smooth operation of the corporation.
Computer and network infrastructure
Another deliverable of the project is the purchase of computers and installation of network infrastructure. Every department will have 30 computers and will share two printers that will be connected through the network. The network will be implemented using the tree topology or also known as expanded star topology. According to Winkelman R (2013), a tree topology combines characteristics of linear bus and star topologies. Winkelman R (2013) explains that it consists of groups of star-configured workstations connected to a linear bus backbone cable. Winkelman R (2013) adds that tree topology allows for the expansion of an existing network. We will use this topology because it facilitates expansion of a network. We will also purchase routers, switches, fiber optic cable, cross over and straight through cables, patch panels, RJ45 among other network equipment. The following screenshot depicts a diagrammatic representation of the network.
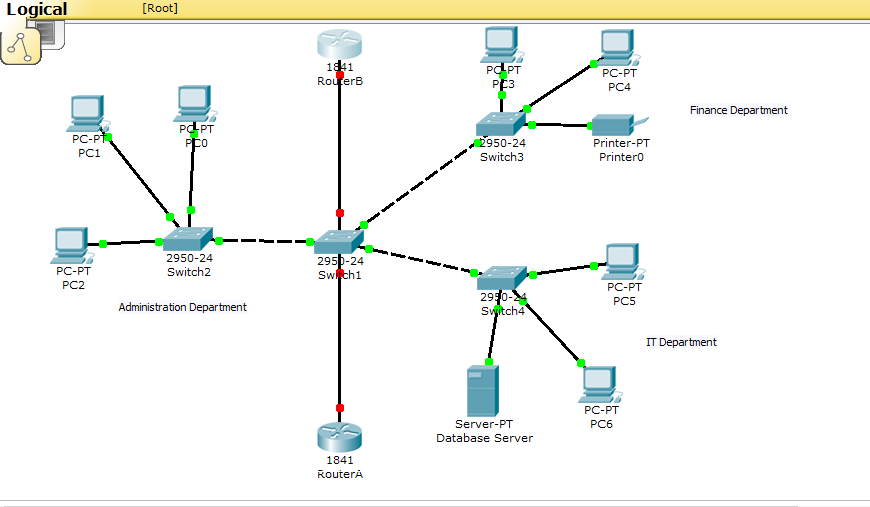
Security measures
Another deliverable of the project will be to ensure the entire system is built using security in mind. The network will have firewalls from both ends of the routers so as to check incoming and outgoing data. All workstations will have an antivirus installed and up to date. The database will facilitate encryption of passwords. Only the network administrators will be able to access the routers and switches and using a Secure Shell (SSH). Only the database administrators will be able to use the Data Definition Language (DDL), that is, only the database administrators have the right and privileges of creating, modifying and deleting tables and also database. All other users can only create and manipulate the data they create. End users can only access the system through the website and mobile application and they have limited rights and privileges. The network will be tested for security so as to check that cross site scripting (XSS) attack and SQL injection attack does not occur. Let us define XSS and SQL injection attacks.
According to Kallin J and Valbuena I (2016) cross-site scripting is a code injection attack that allows an attacker to execute malicious JavaScript in another user’s browser.
According to Porup J (2018) Structured Query Language (SQL) injection is a type of attack that can give an adversary complete control over your web application database by inserting arbitrary SQL into a database query.
Constraints and assumptions
The financial constraint that the company holds is that the entire project should not exceed the budget set aside of $800, 000.
The schedule constraint that the corporation holds is that the entire project should not exceed one year with purchase of computers and network installation beginning so as to make way for other phases because the other phases are dependent on this.
The corporation also holds that it will have its own database server and will not let third part companies access its data.
Scope control
The project manager will ensure that the project is going hand in hand with the documented deliverables and if changes arise, the Project Manager will communicate with the board of directors and see whether to include the changes and also amend the project documents.
Section Two: System Analysis (Week 2: 6 to 8 pages)
Which type of network topology would you recommend for the corporate backbone and the wired and wireless connections? Why do you think this would be the best choice?
A few decades ago nobody knew that the internet would change the business operations of the entire world. Thanks to the eruption of the internet bubble that led to various reforms in the business world. The reforms that the business world is continuously adopting is just because of the rapid growth of the value of equity markets. The innovation in technology is continuous that has been leading to the industries’ capital growth at the highest level. Verbania, Inc. is one of those industries which stopped its operation in the early 20s. Now, the company has decided to relaunch itself and has been thinking about different reinvention options. Nowadays, the importance of social media is obvious since it engages millions of people into your message in seconds. Verbania, Inc. should create a well-structured, well-defined, and well-integrated social media platform that could establish a solid customer-business relationship. The integration of technologies such as Customer Relationship Management (CRM) will be a useful tool for social relationship platform.
I would recommend Verbania, Inc. to integrate Bus Topology for network topology since it is one of the most effective network topologies. A Bus Topology helps to connect computers and other network devices with each other with a single cable. Since it has two ends points it helps transmitting data in one direction only, therefore, it is also known as the Linear Bus Topology. Verbania, Inc. will be able to connect all of its devices to the network. One of the advantages of Bus Topology includes that it is easy to expand and cost-effective. On the other hand, the one of the most critical drawback this network topology has is a failure of its cable fails the whole network system. I will recommend Verbania, Inc. to use Hybrid Topology for wireless connections. A Hybrid Topology helps in rectifying network errors and is easy to use (Rahman & Esmailpour, 2015). One of the advantages of this topology is its effectiveness and flexibility. The disadvantages of Hybrid Topology are the complex design of the network, costly installation, and more time requirements.
Which type of cabling would you recommend? Why do you think this would be the best choice?
Cabling plays a critical role in networking since it is the live-blood in networking. There are various data that cabling carries throughout the network such as transmission both audio and video, alarm signals, serial communications, and voice data. These sort of data networking requires Verbania Inc. to use several cabling systems. I will recommend a well-designed, well-structured, and reliable cabling system for Verbania Inc. networking. The cost of cabling in any network infrastructure is not more than 10% but its role is important equal to 100% for any networking system (Cohen, 2003). If the installation of the cabling system today is proper and as per the company’s recommendations, one can experience its lifespan for the next sixteen years (Clark, 2002). This is also worth noting that two third of the networking problems are caused just because of poor cabling, one of these networking problems is a slow process of information accessibility. There is various communication cabling system used in organizations some of them are fiber optic, screened twisted pair, and twisted-pair but a wise organization always make a distinction between horizontal cables and backbone cables. The function of backbone cables is connecting devices i.e., routers, switches, and servers. On the other hand, the horizontal cables help in connecting wall outlets and communication closets.
Here, I will recommend twisted-pair cables for Verbania, Inc. since it will bring the company back to life again. There are various reasons to select this cable such as it is less expensive, easy to install, and requires cheap tools during the installation process. Another reason includes its outer covering which consists of materials those are non-conducting and help increase the duration of the cabling system. The installation of Fiber Optic Cable is another recommendation that I will propose to Verbania, Inc. This cabling system came in the market in early 1990 and changed the revolutionalized the entire cabling world. If we compare this cable to copper cable we can experience 10 times faster data transmission than that of the copper cable (Cohen, 2003). There are various advantages associated with fiber optic such as it is more protected as compared to copper cable, similarly it is not vulnerable to outdoor cross-talk intrusion (Lau, 2011). It carries data in the form of light pulses because it uses a component of plastic to transfer data signals. This is important to know that the nature of fiber optic cable is not electrical.
How will the network infrastructure accommodate remote access?
Network infrastructure with remote access helps employees of an organization to remain connected with flexibility no matter what is their location. The VPNs establish an encrypted tunnel across the internet allowing secure remote access to corporate resources (Cohen, 2003). The customers or non-employes can avail limited network access for their queries with security and ease. Technically speaking only authorized personnel can access secure connectivity with the help of VPNs. It not only improves efficiency but also reduces communication costs by extending corporate networks. Verbania, Inc. will be able to connect to the network from any host with the help of remote access. However, it is recommended that Verbania, Inc. should take effective measures for the security of remote access VPN so that possible future threats could be avoided. The following are some of the VPN technologies that Verbania, Inc. should take into consideration.
Desktop Software: By using this type of technology Verbania, Inc. will need not to acquire special purpose desktop software since this technology does not require updates.
Application and Network resource Access: This provides offering on board access to any network resource or application on a virtual basis.
End-user Access Device Options: With the help of this technology, Verbenia, Inc. can access and manage employees, vendors, business partners, and contractors information easily.
Customized User Access: A toll that offers accessibility to the policies of the company.
End-user Access Method: This method offers remote access through various VPN software and web browsers.
What solution would you propose to integrate the social media site with a CRM solution?
The importance of CRM to the company increases when the company creates a campaign based on customized appleaing each segment according to their exclusive behavior interests (Guedes, Nardi, Guimarães, Machado & King, 2016). CRM interaction enables comapies to,
Create userfriendly mobile accounts
Create discussion forums enabling users to post comments
Include componets of gaming
Explore people’s capability
Schedule reminders’ sections
Be available 24/7
Protect email features and email accounts
Do Voice Over Internet protocol (VOIP) and Instant messaging and
Rationalize present contacts to the CRM account
For social networking solution, the basic requirements that company should fulfill are:
Integrating composed data with CRM so that the process of customer support and business could be improved.
Collecting, storing, mining, and backing-up user data to have better understanding about users.
Analyzing behaviors, preferences, and patterns of users to present it to promotional agencies
Evaluting user generated traffic for advertising
The social networking application includes the requested functionality for:
Settingup an Account
Taking log-in function
Generting user’s profile
Providing option to add friends
Offering users to remove friends
Providing option to post their comments
The investment on CRM will definitely bring postive returns. Apart from CRM there is a need to train employees about CRM so that they could be able to keep customer data update. The CRM will help Verbania, Inc. to make appropriate decisions based on avaiable data in the system.
What security considerations are involved?
The attributes that social media provides to a business are obvious but the use of social media also brings radical threats to businesses. The customer-business interaction in today’s world is entirely changed and that becomes possible just because of social media. The associated threats with social media are;
Customer Identity compromised
The social profile of customers hacked
Security Considerations
The security consideration that should be taken into account in case of customer’s identity compromised, is two-factor authority system. Whenever a customer tries to open his/her account the system should ask him/her to provide his/her phone number and a pin code prior to entering password should be provided on registered phone number and customer should be required to enter that pin code and once pin code matches it further asks him/her to enter his/her password to enter the account (Newell & Lemon, 2001).
Relating to social profile customers hacked, the customers should be guided on a constant basis not to click any link unless they are certain about its source.
For the protection of customers Verbania, Inc. should formulate a social media policy pertaining to security threats. Once the staff is provided training on social media security they can contribute in a better way to protect customer’s identification and other necessary details.
Section Three: System Design (Week 3: 5 to 7 pages)
Section Five: System Implementation and Maintenance (Week 5 - Individual Activity: 3 to 4 pages)
Feedback:
References:
Clark, C. (2002). Network cabling handbook. Berkeley, Calif.: McGraw-Hill/Osborne.
Cohen, F. (2003). Switching Your Infrastructure. Network Security, 2003(2), 19-20. doi: 10.1016/s1353-4858(03)00213-7
Guedes, E., Nardi, A., Guimarães, F., Machado, S., & King, A. (2016). Social networking, a new online addiction: a review of Facebook and other addiction disorders. Medical Express, 3(1). doi: 10.5935/medicalexpress.2016.01.01
Lau, K. (2011). Ultra-high frequency linear fiber optic systems. Berlin: Springer.
Newell, F., & Lemon, K. (2001). Wireless rules. New York: McGraw-Hill.
Porup, J. (2018). SQL injection explained: How these attacks work and how to prevent them. Retrieved from https://www.csoonline.com/article/3257429/application-security/what-is-sql-injection-this-oldie-but-goodie-can-make-your-web-applications-hurt.html
Rahman, M., & Esmailpour, A. (2015). A Hybrid Network Architecture for Data Centers. 2015 IEEE First International Conference on Big Data Computing Service and Applications. doi: 10.1109/bigdataservice.2015.43
Winkelman, R (2013). Topology. Retrieved from https://fcit.usf.edu/network/chap5/chap5.htm
Valbuena, I. and Kallin, J. (2016). Excess XSS: A comprehensive tutorial on cross-site scripting. Retrieved from https://excess-xss.com/
20



