Attached is the template that you must download, complete and submit here. Instructions are located in the template.You are analyzing and researching the Threats and Vulnerabilities associated with t
ISOL 533 - Information Security and Risk Management Risk Management Plan
University of the Cumberlands
<Review the Scenario on Page #2 of the publisher’s Project: Risk Management Plan. Summarize the information about the company provided in the scenario and place it into this section of the report. Remove these instructions and all other instructions below before submitting the document for grading.>
This Risk Management Plan covers the Risks, Threats and Weaknesses of the Health Network, Inc. (Health Network).
Risks - Threats – Weaknesses within each domain<Using the Threats listed on Page #3 of the publisher’s Project: Risk Management Plan and the 7 Domains diagram on Page #3 of this template, complete the table on Page #2 of this template (review your Lab #1 solution). Once you enter the Threats into the table, list one or more Weaknesses that might exist in a typical organization using research and your imagination) and then list the Risk to the company if the Threat exploits that Weakness. Then group these Risks-Threats-Weaknesses (R-T-W) by Domain and discuss them below in this section.>
User Domain: <list each User Domain R-T--W identified in the table>
Workstation Domain: <list each Workstation Domain R-T--W identified in the table>
LAN Domain: <list each User Domain R-T--W identified in the table>
WAN-to-LAN Domain: <list each Workstation Domain R-T--W identified in the table>
WAN Domain: <list each User Domain R-T--W identified in the table>
Remote Access Domain: <list each Workstation Domain R-T--W identified in the table>
System/Application Domain: <list each User Domain R-T--W identified in the table>
Compliance Laws and Regulations<List the laws and regulations that affect this industry.>
…
| Risk – Threat - Weakness | Domain Impacted |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: | |
| Risk: |
Table 1
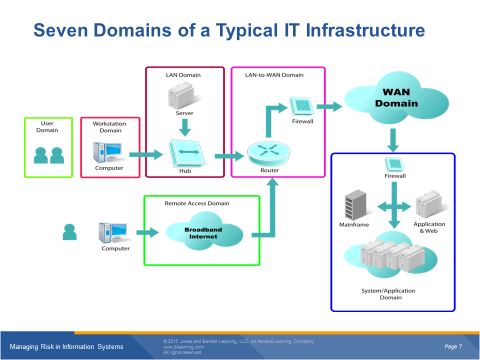
Figure 1



