Research paper:This assignment will be a continuation of your research paper 1. After writing a mini literature review about Deception Technology pick a specific deception technique and write a litera
Running head: RESEARCH PAPER 0
RESEARCH PAPER
Name of the Student: Poornima Devi Potula
Name of the Instructor : Dr. Ben Ayed
Course Code: (ITS834-53)
Date : 05/26/2019
Deception technology is a group of security apparatuses as well as methods that are designed to avoid a hacker who has already arrived in the network from doing destruction. The technology uses traps to lead astray the hacker as well as delay or avoid him from going deeper into the system and reaching his proposed goal.
The purpose of deception technology is to avoid a cybercriminal that has accomplished to penetrate a network from doing any noteworthy damage. The tools work by creating decoys or deception traps that mimic authentic technology properties throughout the infrastructure. These traps can run in a cybernetic or real operating system atmosphere as well as designed to trick the cybercriminal into thinking they have exposed a method to escalate privileges as well as steal authorizations (Suk, Kwan & Hyun, 2018).
How Deception Technology Works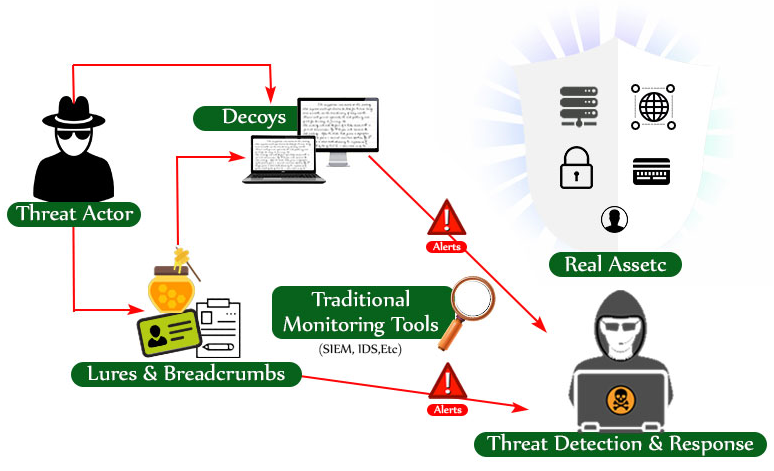
As a case, in fact, imagine the prehistoric city of Troy behind its barriers. The Greeks pretend to departure as well as leave a large horse by the entrances. The Trojans take it private. Privileged the horse, the Greeks catch the Trojans carousing as well as ultimately falling into a drunken torpor. They carefully exit the horse, intent on massacring the protectors as well as opening the gateways to let their army inside. In its place, they find themselves inside a well-guarded compound. They are taken in prison. The Trojans then expose the gates briefly to stand-in the Greek defense force to advance. When they do so, the gateways are protected as well as arrows rain down on the unprotected enemy. As a result, a fully different type of Homer's The Iliad. Such a triumph over a covert hacker is one of the objectives of deception applications.
Usage of Deception Technology Early Post-Breach DetectionNo security key can stop all attacks from occurring on a system, but deception technology aids to give attackers a wrong sense of safety by making them trust they have gained a toehold on the network.
Reduced False Positives and RiskDead ends, false positives, as well as alert exhaustion, can all hamper safety efforts as well as put a drain on properties if they are even investigated at all. Deception technology diminishes the noise with less false positives as well as high loyalty alerts packed full of valuable data.
Scale and Automate at WillWhile the risk to corporate systems as well as information is a regular growing concern, safety teams rarely obtain an increase in their budget to access the deluge of new intimidations. For this cause, deception technology can be a very comfortable resolution (Wang et al., 2018).
From Legacy to IoTDeception technology can be used to deliver breadcrumbs for a huge range of dissimilar devices, counting legacy surroundings, industry-specific atmospheres as well as IoT devices.
The Importance of Dynamic DeceptionOne of the most significant necessities for effective deception technology application is that it must stay vague as well as new to the hacker. If the hacker suspects they are being cuckolded they will do what they can to avoid traps as well as increase their labors in getting to the real possessions. Numerous deception safety solutions have machine learning as well as Artificial Intelligence built into their fundamental. These structures not only confirm deception methods are kept dynamic but also assist to decrease operational overheads as well as the influence on safety teams by freeing them from continually creating new deception movements.
Deception in depthJust as the enduring security chant has been a guard in depth, security specialists recommend deception in depth. It seems the deployment of these methods along the complete attack chain. When hackers are leading the investigation of the network as well as enterprise weak facts, feed them false data on the topography as well as assets. If they are previously inside as well as figuring out what apparatuses to use, delay their deployment with false data. Trick them into sandboxes as well as keep them engaged there for long epochs. Users can choose from separate DDP apparatuses or those that are combined into enterprise safety solutions for detection answer. For instance, some are joint with instrumentation, network access control or intelligence distribution tools (He et al., 2018).
Deception based detection using reliable traps highlights both internal as well as external attacks.
State of the art deception systems identify an extensive diversity of threats and aren’t needful on known signs, database lookups, or pattern matching: Credential Theft, Lateral movement, Attacks on directory systems, Man-in-the-middle, Sensitive data, Geo-fencing, etc.
Deception technology vendors and toolsWhile practical for positive attack trajectories, these approaches have their boundaries. Pingree suggested they ought to be augmented with DPP apparatuses, which are progressively gaining in maturity as well as functionality. There are numerous sellers operating in this space (Kim, 2019). The list contains:
Illusive Networks
Attivo Networks
Cymmetria
Acalvio
GuardiCore
CyberTrap
Specter
TopSpin Security
TrapX
There are an extensive array of deception strategies available to enterprises. But before tapping these to use, businesses ought to understand what makes deception most operative. Those are as follows
Deception must be authentic
Deception must be comprehensive
Deception must be scalable
Reduction in resides time as well as the mean time to recognition and remediation as well.
High-fidelity warnings that simplify as well as accelerate incident reply, while removing alert exhaustion.
Through the appointment, it delivers deeper forensics of adversary intelligence with Indicators of Compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs).
It is also not dependent on knowing each attack vector or technique as well as it is intended to notice early investigation, credential theft, and lateral measure (Bushby, 2019).
Gain discernibility to device adds as well as changes on a system and at risk identifications so that everyone can alleviate risk as well as decrease the attack surface the assailant is pointing.
DPP tools, though, has a method to go to enter the majority, and for now, the market is comparatively small. Gartner imagines no more than 10 percent of enterprises will be using it aggressively by the subsequent year. Among the probable candidates are economic services, healthcare, government, and software verticals.
Bushby, A. (2019). How deception can change cyber security defences. Computer Fraud & Security, 2019(1), 12-14.
He, W., Gao, X., Zhong, W., & Qian, F. (2018). Secure impulsive synchronization control of multi-agent systems under deception attacks. Information Sciences, 459, 354-368.
Kim, Y. G. (2019, January). Deception Tree Model for Cyber Operation. In 2019 International Conference on Platform Technology and Service (PlatCon) (pp. 1-4). IEEE.
Suk, L. J., Kwan, C. J., & Hyun, J. S. (2018). RESEARCH TO VERIFY AND UTILIZE PSYCHOPHYSIOLOGICAL DETECTION OF DECEPTION BASED ON VIBRAIMGE TECHNOLOGY. ELSYS Corp., European Academy of Natural Sciences (EANS), Russian Biometric Association (RBA), AI Burnazyan Federal Medical and Bio, 159.
Wang, Z., Wu, X., Liu, C., Liu, Q., & Zhang, J. (2018, June). RansomTracer: exploiting cyber deception for ransomware tracing. In 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC) (pp. 227-234). IEEE.



