A Penetration Tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities.Take on the role of Penetration Tester for a company provided in t
IntroductionThis is a security threats, attacks, and vulnerability assessment paper for an organization known as JJ People. JJ People is an organization that deals with software development, website development and mobile application development. JJ People only uses Java programming language to design its software.
Java is a computer programming language. It enables programmers to write computer instructions using English-based commands instead of having to write in numeric codes. Java is known as a high-level language because it can be read and written easily by humans.
JJ People IT designs its desktop applications using Java Standard Edition (Java SE), its websites using Java Enterprise Edition (Java EE) and its mobile applications using Android, which entirely depends on Java. JJ People is an international organization that was established in Canada in 2002. Its headquarters is in London, United Kingdom. JJ People has several assets, which include computers that are used to program, website hosting servers where they host their client’s websites, database servers where they put their client’s data, cloud computing services for the database and network infrastructure that supports all these.
Assessment scope of JJ PeopleHardware
Computers
Network fiber optic and cables
Routers, switches, gateways, modems, wireless access points, proxy servers and firewalls
Web servers
Database servers, mail servers, application server, and telnet server
Mobiles and tablets for testing website responsiveness
Software
Operating system
Utilities (antivirus etc.)
Commercial applications such as word processing, photo editing etc.
Database management system and all other software
System model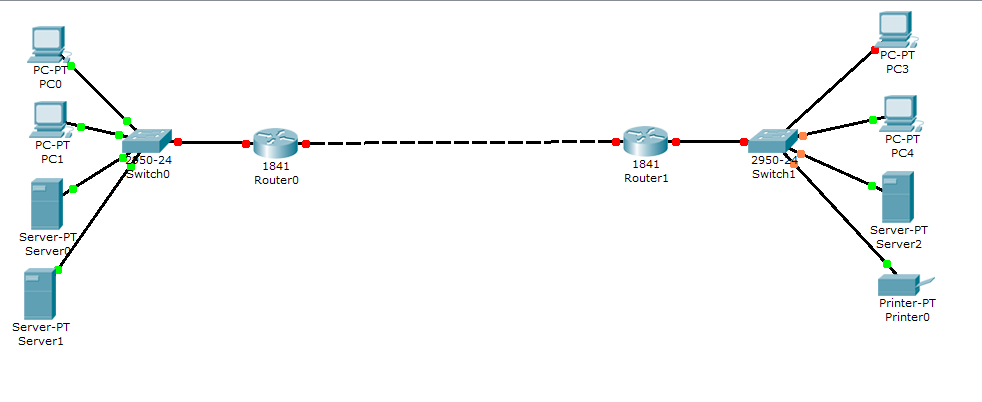
Router – this is a networking device that forwards packets between networks
Switch – a network device that connects devices together in a network
Server – a computer or computer program that manages access to a centralized resource in a network
Firewall – a software or hardware put on the network that prevents forbidden communication as depicted by the network policy
Existing countermeasuresBefore we look at the countermeasures used by JJ People organization, let us first define a couple of terms. They include: countermeasures, vulnerability and threats.
Countermeasures are seen as control. Control as an action, device, procedure, or technique that removes or reduces vulnerability. A vulnerability is a weakness in the system, for example, in procedures, design, or implementation that might be exploited to cause loss or harm. A threat to a computing system is a something that has the potential to cause loss or harm.
JJ People used the C.I.A triad also known as security triad to ensure that they protect their devices and software from threats. The C.I.A stands for confidentiality, integrity and availability. Confidentiality is the ability of a system to ensure that an asset is viewed only by authorized parties. Integrity is ensuring that an asset is modified only by authorized parties. Availability is the ability to ensure that an asset can be used by any authorized parties.
JJ People has in place security policies that are adhered to and touch on various areas including
Network devices and infrastructure
The network devices such as routers and switches will be accessed by network administrators.
Passwords of network devices such as routers and switches will be changed every fortnight and it should be a strong password that includes letters, numbers and special characters.
The network administrator should ensure that the password is encrypted.
The network devices such as routers should lock a user out of the network when he / she tries to access the network by providing two attempts of invalid passwords.
The network devices such as routers and switches should be accessed through the use of Secure Shell (SSH) protocol which is a protocol that facilitates strong authentication and secure connection.
Servers
Servers should be physically located in an access-controlled environment.
Servers should be up to date with the latest security patches.
Servers should only be accessed by system administrators.
Access to services on the server should be logged.
Servers should be accessed over the network through a Secure Shell (SSH) protocol.
Daily incremental back up and weekly full back up will be done on servers.
Users accessing the database server will be given limited access as possible in terms of rights and privileges.
Antivirus policy
All computers and mobile devices including servers should be installed with an antivirus by system administrators.
Antivirus software should be up to data at all times.
Always scan devices attached to computers such as flash drives before using them.
Never download files from unknown or suspicious sources.
Threat agents and possible attacksThreat agent can be seen as an individual or group or anything that can bring about a threat.
A user can save the wrong data thus compromising the integrity of the data.
A java programmer in our case who writes code that performs indefinite loop taking a lot of computer memory and therefore bringing about memory leaks rendering the computer unusable.
Software that does not have latest security patches opening the computer to various attacks such as virus attacks.
A person can try and guess the network passwords through trial and error causing brute force attack.
A person can overwhelm the web server with traffic so that it can crash and therefore leading to denial of services attack.
An attacker can attach a worm to an email attachment and when unsuspecting user downloads the attachment, the worm starts infecting his / her system as it penetrates through the network leading to worm attacks.
Malware attacks – a user can set up a website that has kits to find vulnerabilities in a system and when a user visits the site a malware is forced into their system.
An attacker can inject malicious code into a website so as to access the server through cross site scripting attack.
An attacker can enter SQL commands on a website so as to manipulate the data in the database server thus resulting in SQL injection attack.
An attacker can write a code to look at opened ports on a system through the network and exploit that vulnerability leading to scan attacks.
A disgruntled employee can steal company information or leak sensitive information to competitors leading to insider attack.
An employee can decide to steal a laptop or mobile devices leading to physical attack.
An attacker can send emails or set up a website whereby they ask users to enter their bank details and other details leading to theft of identity and user confidential details. This type of attack is known as phishing attack.
A group of elite team of hackers can target users so as to steal their information over a specific period of time using several techniques such phishing etc. This type of attack is known as advanced persistent threat.
Malvertising attack – this is whereby an attacker uses the online advertising to inject malware into a user’s system when they click on the infected advert.
The types of vulnerabilities that can be exploited by an attacker include
Insufficient testing of the Java programmed software.
Lack of proper design while coming up with the Java software.
Lack of implementing strong passwords to the system and having passwords such as “admin”.
Lack of having antivirus that are up to date.
Inadequate recruiting process of personnel.
Unprotected communication lines
Insecure network architecture
Lack of closing unused ports.



