Develop a 5- to 6-page manual using the Security Standards, Policies, and Procedures Template with recommendations to management of security standards, polices, and procedures which should be implemen
This is a security threats, attacks, and vulnerability assessment paper for an organization known as JJ People. JJ People is an organization that deals with software development, website development and mobile application development. JJ People only uses Java programming language to design its software.
Java is a computer programming language. It enables programmers to write computer instructions using English-based commands instead of having to write in numeric codes. Java is known as a high-level language because it can be read and written easily by humans.
JJ People IT designs its desktop applications using Java Standard Edition (Java SE), its websites using Java Enterprise Edition (Java EE) and its mobile applications using Android, which entirely depends on Java. JJ People is an international organization that was established in Canada in 2002. Its headquarters is in London, United Kingdom. JJ People has several assets, which include computers that are used to program, website hosting servers where they host their client’s websites, database servers where they put their client’s data, cloud computing services for the database and network infrastructure that supports all these.
Assessment scope of JJ PeopleHardware
Computers
Network fiber optic and cables
Routers, switches, gateways, modems, wireless access points, proxy servers and firewalls
Web servers
Database servers, mail servers, application server, and telnet server
Mobiles and tablets for testing website responsiveness
Software
Operating system
Utilities (antivirus etc.)
Commercial applications such as word processing, photo editing etc.
Database management system and all other software
System model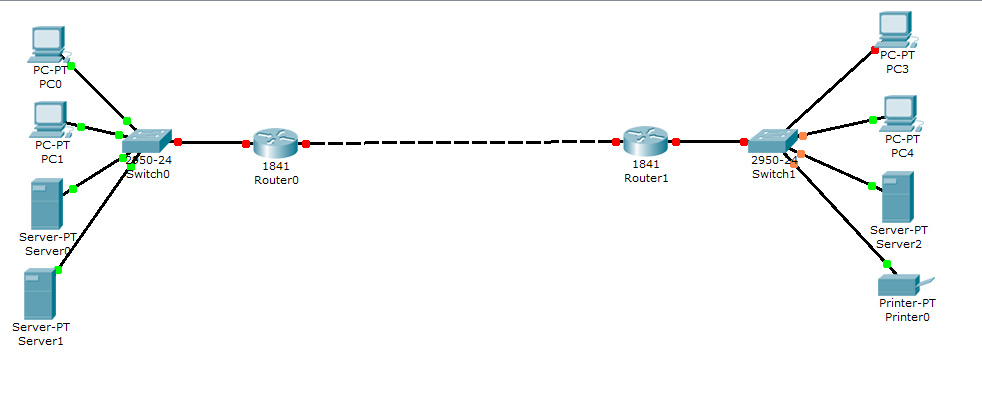
Router – this is a networking device that forwards packets between networks
Switch – a network device that connects devices together in a network
Server – a computer or computer program that manages access to a centralized resource in a network
Firewall – a software or hardware put on the network that prevents forbidden communication as depicted by the network policy
Existing countermeasuresBefore we look at the countermeasures used by JJ People organization, let us first define a couple of terms. They include: countermeasures, vulnerability and threats.
Countermeasures are seen as control. Control as an action, device, procedure, or technique that removes or reduces vulnerability. A vulnerability is a weakness in the system, for example, in procedures, design, or implementation that might be exploited to cause loss or harm. A threat to a computing system is a something that has the potential to cause loss or harm.
JJ People used the C.I.A triad also known as security triad to ensure that they protect their devices and software from threats. The C.I.A stands for confidentiality, integrity and availability. Confidentiality is the ability of a system to ensure that an asset is viewed only by authorized parties. Integrity is ensuring that an asset is modified only by authorized parties. Availability is the ability to ensure that an asset can be used by any authorized parties.
JJ People has in place security policies that are adhered to and touch on various areas including
Network devices and infrastructure
The network devices such as routers and switches will be accessed by network administrators.
Passwords of network devices such as routers and switches will be changed every fortnight and it should be a strong password that includes letters, numbers and special characters.
The network administrator should ensure that the password is encrypted.
The network devices such as routers should lock a user out of the network when he / she tries to access the network by providing two attempts of invalid passwords.
The network devices such as routers and switches should be accessed through the use of Secure Shell (SSH) protocol which is a protocol that facilitates strong authentication and secure connection.
Servers
Servers should be physically located in an access-controlled environment.
Servers should be up to date with the latest security patches.
Servers should only be accessed by system administrators.
Access to services on the server should be logged.
Servers should be accessed over the network through a Secure Shell (SSH) protocol.
Daily incremental back up and weekly full back up will be done on servers.
Users accessing the database server will be given limited access as possible in terms of rights and privileges.
Antivirus policy
All computers and mobile devices including servers should be installed with an antivirus by system administrators.
Antivirus software should be up to data at all times.
Always scan devices attached to computers such as flash drives before using them.
Never download files from unknown or suspicious sources.
Threat agents and possible attacksThreat agent can be seen as an individual or group or anything that can bring about a threat.
A user can save the wrong data thus compromising the integrity of the data.
A java programmer in our case who writes code that performs indefinite loop taking a lot of computer memory and therefore bringing about memory leaks rendering the computer unusable.
Software that does not have latest security patches opening the computer to various attacks such as virus attacks.
A person can try and guess the network passwords through trial and error causing brute force attack.
A person can overwhelm the web server with traffic so that it can crash and therefore leading to denial of services attack.
An attacker can attach a worm to an email attachment and when unsuspecting user downloads the attachment, the worm starts infecting his / her system as it penetrates through the network leading to worm attacks.
Malware attacks – a user can set up a website that has kits to find vulnerabilities in a system and when a user visits the site a malware is forced into their system.
An attacker can inject malicious code into a website so as to access the server through cross site scripting attack.
An attacker can enter SQL commands on a website so as to manipulate the data in the database server thus resulting in SQL injection attack.
An attacker can write a code to look at opened ports on a system through the network and exploit that vulnerability leading to scan attacks.
A disgruntled employee can steal company information or leak sensitive information to competitors leading to insider attack.
An employee can decide to steal a laptop or mobile devices leading to physical attack.
An attacker can send emails or set up a website whereby they ask users to enter their bank details and other details leading to theft of identity and user confidential details. This type of attack is known as phishing attack.
A group of elite team of hackers can target users so as to steal their information over a specific period of time using several techniques such phishing etc. This type of attack is known as advanced persistent threat.
Malvertising attack – this is whereby an attacker uses the online advertising to inject malware into a user’s system when they click on the infected advert.
The types of vulnerabilities that can be exploited by an attacker include
Insufficient testing of the Java programmed software.
Lack of proper design while coming up with the Java software.
Lack of implementing strong passwords to the system and having passwords such as “admin”.
Lack of having antivirus that are up to date.
Inadequate recruiting process of personnel.
Unprotected communication lines
Insecure network architecture
Lack of closing unused ports.
This document will deal with penetration testing of a website application developed by JJ People Limited. The website application has been developed using the Java Enterprise Edition (JavaEE) and the database used is MySQL database due to its popularity in website applications and E-commerce. The website application is known as Niko. In this penetration testing we will look at the pre-planning, the timeline required, the location of the testing, the countries where the tests will take place, the technologies used to conduct the penetration testing among other things. Let us start by defining penetration testing.
Penetration testing (or pentesting) simulates real attacks to assess the risk associated with potential security breaches. During a pentest, the testers not only discover vulnerabilities that could be used by attackers but also exploit vulnerabilities, where possible, to assess what attackers might gain after a successful exploitation.
Penetration testing scopeThe penetration testing will test various areas of the system. The areas will include:
Passwords attacks
Client-side attacks
Social engineering
Web application attacks such as SQL injection
Wireless attacks
Stack-based buffer overflow
Pentest Pre-planning
The penetration testing of the website application will take 3 weeks and every test will have its own phase, for example passwords attack will be phase one and stack-based buffer overflow will be phase six.
The Niko website application was developed at the headquarter office in London and it will be hosted in the headquarters’ servers. This implies that the testing will happen at the JJ People Limited headquarters’ office in London.
The website application penetration testing team will involve two senior full-stack website developers, who will test the website application attacks such as cross site scripting attacks, two systems administrators who will test password attacks, two network administrators who will test wireless and network attacks, two database administrators who will test database attacks such as SQL-injection attacks, and two senior java programmers who will test stack-based overflow and other Java related problems.
The client’s agreed that since the testing of a website application is a technical endeavor, client’s personnel that were aware of the testing were from technical departments and they include: one senior full-stack website developer, one senior Java programmer, one systems administrator, one network administrator, one senior database administrator and the Chief Information Security Officer (CISO).
The penetration testing team will be provided with various resources such as access to the server and the database server as long as it has been approved by the senior systems administrator, computers, and network access as long as it has been approved by the senior network administrator. The penetration team will also have access to the entire code and the database code.
Tools usedThe penetration testing team will use various technologies such as virtual machine known as VMware and Kali Linux. According to Kali.org website, Kali Linux is a “Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing”. We will also use other technologies such as:
Hyperion
We will use the hyperion encryption program to bypass the antivirus software
Veil-Evasion
Veil-Evasion is a tool that generates payload executables you can use to bypass common antivirus solutions.
Ettercap
Ettercap is a tool that is used to perform man-in-the-middle attacks.
We will use nslookup which is a tool that turns a domain name from the human-readable URL to an IP address. We will use Whois tool so as to know the information of a person who registered a certain domain. We will use Maltego technology which is a data-mining tool that has been designed to visualize open source intelligence gathering. We will use the nmap tool for port scanning. We will also use ghost-phisher which is a wireless and Ethernet security auditing and attack software. We will use nikto tool which is a web server scanner which scans the server for potentially dangerous files among others. We will use sqlmap which detects SQL injection in a database server. We will also use several other tools such as proxyStrike, jboss-autopwn, FunkLoad etc.
Test boundariesWhat is tested?
The penetration testing has got six phases: passwords attacks (testing how an attacker can access the system e.g. using weak passwords), client-side attacks (testing whether an attacker can inject malicious code using techniques such as cross-site scripting), website application attacks such as SQL injection, network and wireless attacks, social engineering attacks and stack-based buffer overflow.
Social engineering testing
A social engineering test uses techniques by professional ethical hackers to trick a customer’s staff into revealing sensitive information or perform the actions that create security holes for a hacker to access the network.
We will test the on-site and off-site social engineering penetration testing.
Physical security testing
A physical penetration test sets out to uncover weaknesses in your physical security before bad potential unauthorized persons enter. We will test the physical security from internal boundaries i.e. from within the organization such as an unauthorized employee trying to access the server and from external boundaries i.e. an unauthorized employee trying to access the organization building.
Restrictions on penetration testingLimitation of time
Penetration testing takes a shorter time to conduct whereas an attacker can have a week, month or even a year to plan his / her attack.
Limitation of scope
Organizations do not test everything because they have limited their scope of testing thus leaving areas that might be vulnerable and can be a perfect place for an attacker to attack.
Limitation of known exploits
Testers only test the system from areas that they only know such as cross-site scripting; SQL injection etc. leaving out areas that they don’t know which an attacker can find vulnerability and exploit.
The type of corporate policies that affect our test include password policies, network policies etc.
Pentest Execution planningReconnaissance
We gathered information about our target such as IP address, web server, network topology, underlying database used, mail servers etc.
Scanning
Here we interacted with the target system with an aim of identifying vulnerabilities. We persistently sent malicious code in input text boxes and HTTP requests. We also used scanning tools to see opened ports etc. and record all these response.
Gaining access
We identified vulnerability and that was by implanting malicious code to the system while sending the HTTP request.
Maintaining access
We maintained access by tricking the system that it is using a secure connection by injecting a malicious code when a request is sent, the server views as if it is sending request on a secure connection (HTTPS).
Penetration Testing analysis and report planningAll other aspects of the website application and the system are secure but it is easier to get into the system by putting a malicious code while sending an HTTP request.



