The Verbania project is nearing completion. The solution is nearly ready for implementation. As a highly valued member of the team, you alone have been selected to develop the Implementation Plan. Thi
Program Capstone in IT (ITCO498)
Systems Implementation Plan
Group members:
Arthur Foster – Risk/Security-Team member
Joshua Teague – Networking – Editor, Team member
Marcus Declouette – Networking-Team member
Riaad Kamaludeen – Networking –Team Leader
Date: July 7th, 2019
Abstract
Organizations today face a tumultuous environment when it comes to technological change. Companies are having to adapt to and often reinvent themselves more frequently than in the past. Our project company Verbania is essentially reinventing itself in the light of how people have through Social media become more digitally connected. The project will require instant messaging, blog post capability, mobile application and creation and maintenance of secure user accounts/profiles. The starting point is gathering the current state of the organization’s assets. These should be evaluated in terms of functionality, network topology, perimeter defense mechanisms, and disaster recovery among other critical areas. Business critical components are identified, and backups prepared in the event of man-made or natural disasters. Analysis of pertinent system will provide information for the next phase of the project. Major components involved in this portion of the project center on security of System assets through use of authentication mechanisms, secure communications, and effective use of policies and procedures. A network of this size will require subject matter experts gleaning information from use case, diagrams, and sequence to put together reasonable timelines and goals. The mobile application portion of the project. Software solutions are utilized during the implementation and final phases of the project. Finally, software solutions and training materials and programs are established to maintain a culture of security. Once the system design is complete, system development and implementation are the critical to move the project toward completion.
Table of Contents
Executive Summary 5
Final Insights of Capstone Project 6
Section One: Planning and System Requirements 6
Specific and Detailed Requirements (Joshua Teague) 7
Resources needed for I.T infrastructure (Marcus Declouette) 9
Hardware and Software Infrastructure (Arthur Foster) 9
High-Level Overview of Network Diagram (Riaad Kamaludeen) 11
Employees and End Users Access 11
Section Two: System Analysis 12
Which type of network topology would you recommend for the corporate backbone and the wired and wireless connections? Why do you think this would be the best choice? (Riaad Kamaludeen) 12
Which type of cabling would you recommend? Why do you think this would be the best choice? (Riaad Kamaludeen) 13
How will the network infrastructure accommodate remote access? (Marcus Declouette) 15
What solution would you propose to integrate the social media site with a CRM solution? (Arthur Foster). 16
What security considerations are involved? (Joshua Teague) 16
Physical Security 17
Digital Security 17
Section Three: System Design 18
Password creation and protection Policy (Riaad Kamaludeen) 18
Remote access (Arthur Foster) 20
Router and Switch Security Policy (Joshua Teague) 21
Server Policy (Arthur Foster) 23
Encryption Policy (Joshua Teague) 24
Email Policy (Riaad Kamaludeen) 24
Section Four: System Development 27
Case, sequence and class diagrams (Riaad Kamaludeen) 27
Mobile Application Encryption and Network Connectivity (Joshua Teague) 32
Business Design Document (BDD) and System Design Document (SDD) (Marcus Declouette) 35
Assumptions: 37
Feedback: 37
Section Five: System Implementation and Maintenance 38
Assumptions: 38
Feedback: 38
References 39
TBD
Final Insights of Capstone Project
TBD
Section One: Planning and System Requirements Specific and Detailed Requirements (Joshua Teague)There are three primary requirement sets for the Verbania project; user requirements, company requirements, and functionality requirements. The user requirements are a set of basic necessities the users require to interact with the social networking site. Normally a well-researched set of user-requirements are determined before the validation portion of the project begins. This information is then detailed and scrutinized by analysts for a comprehensive user requirement list (Parker, 2012). For this project the basic requirements have been laid out already and they are:
Creating an account and a profile
Creating discussion forums and posting
Search capability for people
Gaming component
Calendar component for reminders
Instant messaging and Voice Over Internet protocol (VOIP)-type calling between friends
Secure account and email feature
Availability seven days a week
The company requirements come from the owner, stakeholders, and company executives. These requirements are designed to be used for attracting potential advertisers and ultimately generate a revenue for the company. These requirements include:
Collect, store, back up, and mine user data to better understand users.
Integrate collected data with customer relationship management (CRM) to improve business and customer support processes.
Analyze user patterns, behavior, and generated traffic to present to advertisers.
The functionality requirements are what the software will do and how it will perform these duties. Meaning they determine how the user essentially uses the software. These functions will be the driving force for user interactions on the network. These requirements include:
Account setup and log-in functionality
Creating a profile
Adding or removing friends
Posting to a discussion area
Security apparatus (Physical and Digital)
In order for Verbania to get back to the good ole days of being on top of the internet age is a few things. The infrastructure need is a Router both wireless and wired that’s connected to the internet. Then a firewall to protect the internet and the backbone switch. Then have the servers such as mail web, proxy and DNS connect to the back bone switch. Then a fiber cord that connect to a switch that’s connected to the employee computers that’s also connected to the hub of the internet. I would also add a cloud made from IBM as they make the best technology that has security and storage of the data that will be saved and stored to the site. Security is a high priority along with storage space and being able to access the network with ease and having it work fast.
Within our planning and system requirements we are including more specific information about the hardware and software approach that Verbania will need. Once we have the architecture in place, we will understand how all the Requirements will fit together. As a reminder our requirements include the following:
-Creating Account/Profile
-Discussion Forums/Posting
-Search for other Users
-Gaming
-Calendar/Reminders
-Instant messaging
-Secure Account Email Feature
-247 365 Availability
Using Software as a Service (Saas) is an effective way to handle these needs. Instant messaging, reminders, and profile management can be handled in a central location. Any issues will shift responsibility to the third-party provider. It is also important to note the importance of using the correct tools to handle the project requirements (Mowl, 2012). The scalability of this type of service will assist with account and profile creation, discussion boards, and calendar management.
The amount of staff required, and subject matter experts required to lay much of the backbones of these services can be minimized by utilizing cloud services (Grant & Kenton, 2019). At the same time, it is important to not miss the forest for the trees and realize that a certain level of control will be given up but using this methodology will produce a better final product for Verbania. Using cloud services from major companies like Google cloud cane be used to handle game platform services and the discussion board and many of the other requirements ("Overview of Cloud Game Infrastructure", 2019). The more sensitive data utilized by applications can be managed by a small in-house team that is properly trained.
High-Level Overview of Network Diagram (Riaad Kamaludeen) 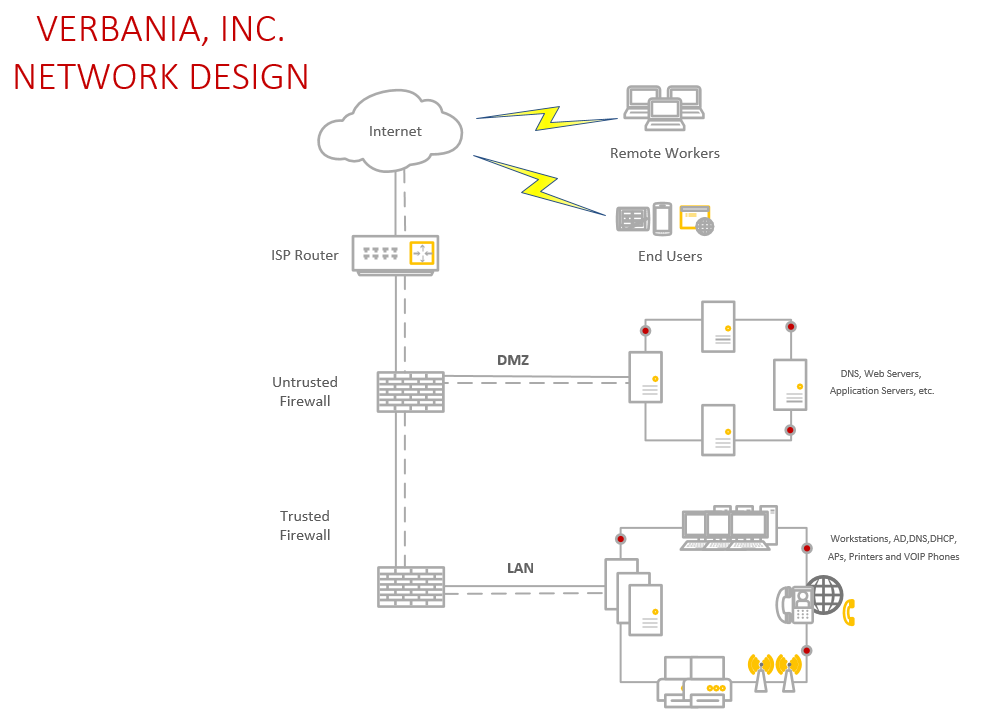
When talking about access, this can be achieved in many ways, but from the perspective of employees, access can be either internally or externally. Internal access is having access to files, emails, applications, and printers found on the Local area network in order to get work done. The same can be said about external, but it is done through a VPN software. For example, Cisco Any Connect can be used to establish a secure VPN session to provide access to resources to external employees working from home or on the road. However, end users remote access has to with access to the social networking website and the mobile application. From the perspective of the end user, they get access to make changes to their user profile, add/remove friends, posting, and login settings.
Section Two: System AnalysisWhich type of network topology would you recommend for the corporate backbone and the wired and wireless connections? Why do you think this would be the best choice? (Riaad Kamaludeen)
Star Topology is the most suitable and most commonly used topology for a cooperate backbone and wired connections in use today. The reason why star topology is the best choice form the corporate backbone and wired connections. This is because all networking devices, whether it is servers, workstations, printers, and more are wired to a central switch which establishes, break and maintains the connection between devices, unlike other topologies like Bus. Moreover, most star topology network is Ethernet, which means it uses a mechanism called CSMA/CD (Carrier Sense Multiple Access with Collision Detection) it works when a node transmits only after listening to the media and ensuring that no transmission is taking place. Further, sending nodes detect when a collision occurs and stop transmitting immediately, backing off for a random amount of time before trying again. This results in efficient use of the media since the bandwidth of transmitting the entire frame are not wasted making it efficient.
Star topology also offers a centralized management solution through the use of a switch that can be used to add devices to the network easily. Furthermore, if a computer or device fails the rest of the network is unaffected.
Which type of cabling would you recommend? Why do you think this would be the best choice? (Riaad Kamaludeen) For wireless connections, the implementation of an infrastructure wireless topology is used to extend the capability of the wired network to include wireless communication to devices that uses wireless technologies. The communication is facilitated by a base station known as an access point (AP) that form the bridge between the wired and the wireless LAN (Mitchell, 2019).
When considering the type of cable for the network in question and its standard that will be used to support the network infrastructure many factors have to be taken into account such as speed, length, POE compatibility, STP/UTP for interference and more (Garrison, 2016). However, administrators should choose Cat.6a although there are more development and many more in development Cat. 6a is widely accessible and offers many benefits over previous categories of Ethernet cables, as shown in the figure 1. below. It further meets the design requirements of Verbania, Inc., because of the need for VOIP, POE and high bandwidth utilization. Nevertheless, the design should incorporate 10 Gbps copper switching with Cat. 7 cabling but administrators can opt for Cat. 6a if the servers are within 55m to support 10 Gbps.
Moreover, twisted pair cables come in two forms namely shielded and unshielded. The shielded cable had a protect coating which is either made up of braided strands of copper, copper tape or a conductive polymer that reduces interferences. For example, when designing the network, shielded cables must be used in an area where there is EMI inference to help reduce / prevent cross talk.
Shielded cables can be identified by its letters. The first letter means the type of shield that will be used. For example, F stands for Foil shield, While S is for Braided Shielding. On the other hand, the second part of the code shows if a twisted pair is foiled or un-foiled. Nonetheless, Unshielded Twisted Pair (UTP) is twisted pair cables without shielding and is most commonly used for LAN implementations, and the letter U can identify the cables.
Figure 1. compares the different categories of Ethernet cables and their specifications.
Different Ethernet Categories
| Category 3 | Category 4 | Category 5 | Category 5e | Category 6a | Category 7 | |
| Cable Type | UTP | UTP | UTP | UTP | UTP or STP | S/FTP |
| Max. Data Transmission Speed | 10 Mbps | 10/100/1000 Mbps | 10/100/1000 Mbps | 10/100/1000 Mbps | 10,000 Mbps | 10,000 Mbps |
| Max. Bandwidth | 16 MHz | 100 MHz | 100 MHz | 250 MHz | 500 MHz | 600 MHz |
(Mailheau, 2019)
In conclusion, the cable standard does not have to be one standard, but careful selection of standard will help to mitigate cable issues and help to build a future proof and stable infrastructure for Verbania, Inc.
How will the network infrastructure accommodate remote access? (Marcus Declouette)
Remote access is normally accomplished with the mixture of software, hardware, and network connectivity. Usually, a normal remote access before the wide availability of the internet connectivity is accomplished by using a terminal emulation software that controls access over hardware modem, that runs through a telephone network. The remote access then becomes accomplished with using secure software and solutions such as a VPN, software by connecting with other host that are linked through a hard-wired network interface or a Wi-Fi network interface by connecting through the internet network.
Remote access VPN’s are used to connect different users to the private networks. The remote access VPN allows the user a VPN client capable of connecting to the private network’s VPN server.
This is one of the ways that the network will be able to accommodate the remote access. Remote access is being able to gain access to the network basically from almost anywhere. They computer system gain access to the VPN of the private VPN network allowing them to be on the network instead of being located in the immediate access to the network location. This allows the company to hire the best personnel for the company wherever they are located. Improving the overall workflow and accommodation to the company.
What solution would you propose to integrate the social media site with a CRM solution? (Arthur Foster).With the presence and influence of social media its integration into the Verbania project will require special care. Part of the reason this is so important is that it creates a portal or connection between the organization and its customers. The use of applications and software allows for integration and ease of access to customer data (Mendenhall, 2015). The value that this information represents is remarkable. Gartner advises that companies reward customers in order to create more of a fan base (Diana, 2019). These recommendations will make Verbania more marketable and make sense when the return is realized.
What security considerations are involved? (Joshua Teague)The security consideration is to be taken very seriously. These measures will protect the vital data of the company and the user’s information which the company is responsible for protecting. There are two sections of security that need to be considered for the Verbania project. The first section will be physical security. The second section is the digital security that will be employed on the network and devices to secure the company network and webpage.
Physical SecurityThe physical security aspects that would be recommended for the Verbania project would be installing an alarm system to prevent break-ins and alert authorities if they should be triggered. There should be security cameras in place around the perimeter of the building focusing on entry points. There should also be security cameras guarding vital devices such as the executive’s computer, the server room (inside and outside), and any other designated devices that should be monitored. There should also be a more advanced style of entry to the server room using something along the line of password verification entry, or ID card authentication. There should also be a security team if deemed necessary. Another important aspect of physical security is ensuring the temperature is kept in the correct range. This can be accomplished by adding extra ventilation to the server room (Rykhoff, 2016).
Digital SecurityDigital security is the network implemented aspects of security. This include things such as Firewalls, Username/Password authentication, Secondary authentication and SSL certificates, and Backup maintenance/update maintenance. The Firewalls inspect incoming and outgoing traffic to ensure only the desired traffic is accessing the network. If the firewall detects unknown credentials, the transmission is denied and logged for inspection later. The username/password authentication is one of the most common forms of verification methods for digital security. Each user should have a unique password and username combo for system identification (Rubens, 2016). The secondary authentication is more commonly referred to as MFA and can best be exampled by the I’m not a bot verification found on many websites or the security questions that make the user answer pre-determined questions as a secondary verification means (Rouse, 2015). The SSL certificate adds a layer of encryption to the website and data transmission. These are generally purchased from a third-party vendor. The backup and update maintenance could be considered the most important aspect of the digital security. Performing updates keep the system current on known hacker prevention patches and the backups are vital for data recovery in the event of any form of disaster strikes (Rubens, 2016).
Section Three: System DesignPassword creation and protection Policy (Riaad Kamaludeen)
Overview
Passwords plays an integral role in computer security, as such passwords that are not carefully selected can result in unauthorized access and exploitation of resources. All employees, including contractors, and other business relation partners with access to Verbania, Inc. network are responsible for taking the necessary steps outlined below to select and secure their passwords accurately.
Purpose
The purpose of this document is to establish a standard for creating a secure password and protecting those passwords.
Scope
The scope of this policy includes all persons who have an account or any way of authenticating to Verbania, Inc., networks, systems or requires a password for authentication.
Policy
Password creation/requirements
All levels including user and system must adhere to the password creation guidelines listed below:
Length – Minimum password length include eight characters.
Content Requirements – Passwords must contain a mixture of upper- and lower-case characters, numeric, and special characters.
Change Frequency – Passwords are required to be changed every three months (90 days). Compromise password should be changed immediately.
Reuse – Previous twelve passwords cannot be reused.
Elevated privileged accounts - Privileged accounts must use multi-form authentication.
Password Change
Passwords should be changed immediately when there is a reason to suspect it has been compromised.
Periodically or randomly Verbania, Inc., I.T team, will select users to check it can be guessed or cracked to ensure compliance with password creation guidelines.
Password Protection
Restrictions on Sharing Passwords – Passwords should be kept confidential, not written down, shared, or stored on users’ computers.
Restrictions on Recording Passwords - Passwords are concealed or suppressed on all active screens, never printed or included in the documentation and should be stored in an encrypted format.
Passwords should not be included in email messages or other forms of electronic communication, nor revealed over the phone to anyone.
Passwords may be stored only in “password managers” authorized by the organization.
The “Remember Password” feature found on browsers should not be used.
Any user suspecting that his/her password may have been compromised must report the incident and change all passwords.
Verbania will need to have a secure means to allow vendors to operate on various part of the network. For machines running Windows- Terminal services along with VPN should be used. Linux and Unix machines should utilize SSH. This process secure remote access by connecting to an SSH server (Ellingwood, 2013). Taking these steps will help create a narrower attack surface for attackers.
Router and Switch Security Policy (Joshua Teague)Overview
The Verbania Project will use routers and switches to transmit data across the network and these devices need to be configured for all possible security enhancement. Routers and switches communicate at the network level of the OSI model and can be configured to allow certain transmissions to be allowed to pass to and from the network. This allows for another level of security on the Verbania network. Having a security policy for the routers and switches will give Verbania a good means of controlling what traffic is allowed on their network (Molenaar, 2017).
Purpose
The purpose of using security enhancements on routers and switches is to help protect from outside and inside attacks. These attacks can find weaknesses on routers and switches and proper security protocols will prevent these attacks from occurring.
Scope
The scope of the policy are all routers and switches on the network. The scope also includes all employees that will be transmitting data on the network, who has access to the devices, and what authorized users can do on the router.
Policy
Authentication
There will be authentication standards placed on the routers and devices to control access. Using a TACACS authentication means the routers and switches will have means to prevent unwanted access. Each user will be given login credentials to safeguard the devices. The credentials will be stored on the server and will be called upon when needed (Molenaar, 2017).
Physical Access/Protection
Like a server, routers and switches should be physically safeguarded as well. They should be kept in a well-controlled room with access control means. Only certain personal will be given access and monitoring will be placed on entry points to the devices.
Monitoring
The policy for monitoring the routers and switches will include log files and documentation.
Log files: These files will record traffic on the devices that can be used for comparison and monitoring functions.
Documentation: This will include manually recording of anything that is done on the network. This will help if anything should arise and the documentation can be used to compare with irregularities that may arise (Molenaar, 2017).
This server security policy will cover all servers connected to Verbania network used for any purpose.
Location
Servers need to be placed in secure physical location. This access control method is intended to prevent the theft of servers or the alteration of device configuration (Utilize Windows, 2013). These locations should have proper ventilation, be secure to other structures in a server room, and put them in a room by themselves.
Services
Server should run the minimum service that are required, and each service should be viewed as a potential entry point. Security of servers should include virus protection and restrictions on who can log in. Servers should include stringent password protection along with service banners warning anyone attempting unauthorized access. Logs should also be kept as to who access the server room and what they did while they were there especially is the server processes with sensitive data.
Encryption Policy (Joshua Teague)Overview
Encryption is when the data is scrambled into unreadable information and then using a key system, unscrambled by the intended receiver. This allows data to be secured in transit and while being stored. The encryption can be done in various methods but the two most common are end-to-end encryption and Stored key encryption (Bisson, 2018).
Purpose
The purpose of encryption policies is to define what types of acceptable encryption will be used on the Verbania Project.
Scope
The scope of the encryption policy is the encryption type that will be used on the network.
Policy
Any encryption done on the Verbania Project will be done using the end-to-end encryption method. If the incorrect encryption is used there will be repercussion. This policy is vital to maintaining security on the network (Bisson, 2018).
Email Policy (Riaad Kamaludeen)
Overview
Electronic email is primarily used by all organizations today as a method for communication and bring awareness to the company. However, the misuse of email can post significant security, privacy, and legal issues. Thus, it is imperative that users understand the correct use of emails.
Purpose
The purpose of this policy is to enforce proper use of Verbania, Inc., email system and to bring to users’ attention of what is acceptable and unacceptable use of the email system.
Scope
The scope of this policy covers the proper use of any email transmitted from Verbania, Inc., and applies to all persons including employees, vendors, contractors and other business-related partners who conducts work on behalf of Verbania, Inc.
Policy
Email usages must be consistent with Verbania, Inc., policies, and procedures of ethical conduct, safety, compliance with applicable laws, and proper business practices.
Email account must be used to conduct business-related purposes. Personnel communication is permitted but must be limited. Any non Verbania, Inc., related commercial uses are prohibited.
Data enclosed within an email message or an attachment must be secured.
The email system shall not be used for the creation or distribution of any disruptive or offensive messages, including offensive comments about race, gender, hair color, disabilities, age, sexual orientation, pornography, religious beliefs and practice, political beliefs, or national origin. Employees who receive any emails with this content from any Verbania, Inc., the employee should report the matter to their supervisor immediately.
Users are prohibited from forwarding emails to their third-party email system. Individual messages which are forwarded by the user must not contain Verbania, Inc., confidential information.
Users are prohibited from using third-party email systems and storage servers such as Google, Yahoo, and Outlook to conduct Verbania, Inc., business or to store or retain email.
Verbania, Inc., may monitor emails without informing the user and it not obliged to monitor all email messages.
Case, sequence and class diagrams (Riaad Kamaludeen)
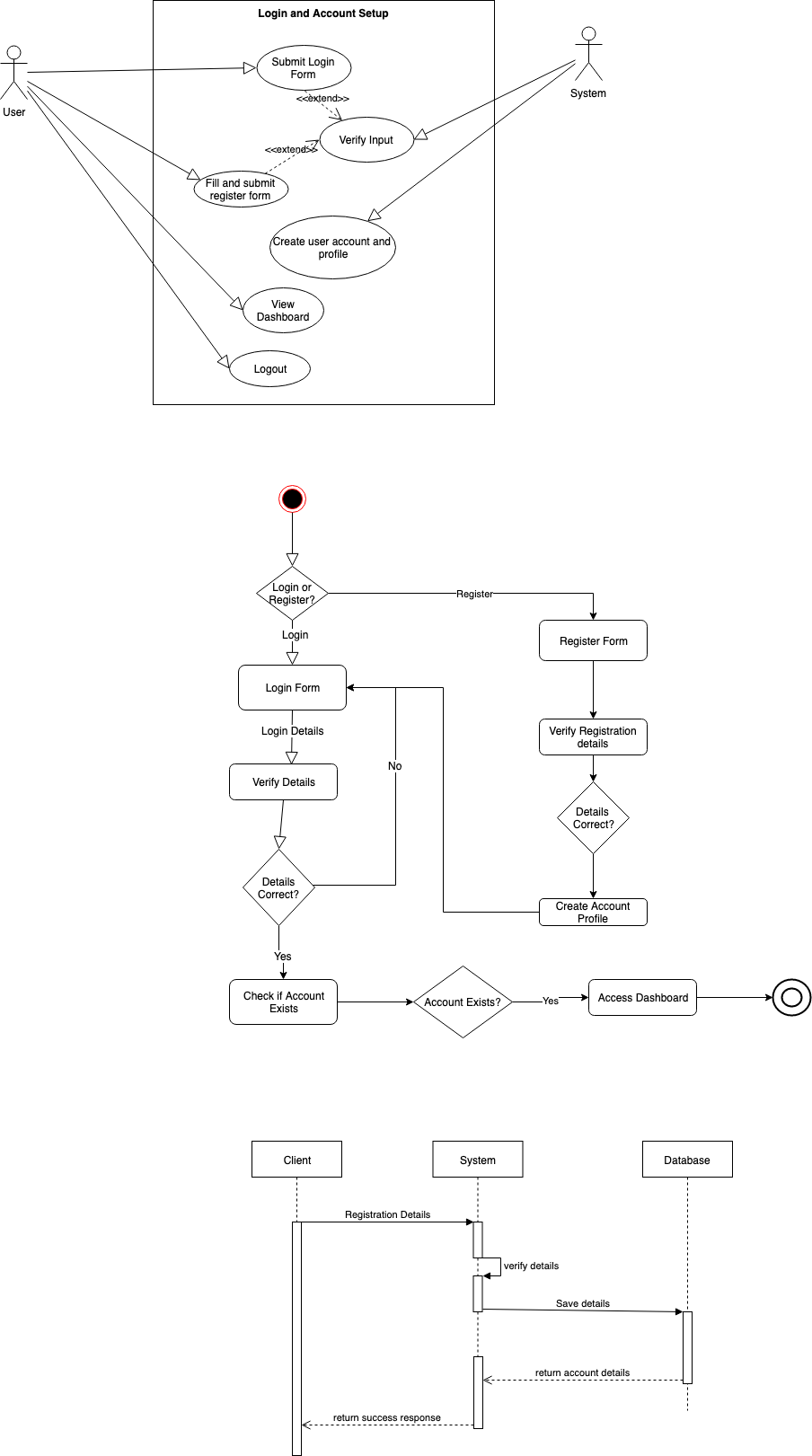
Account setup & Login diagrams
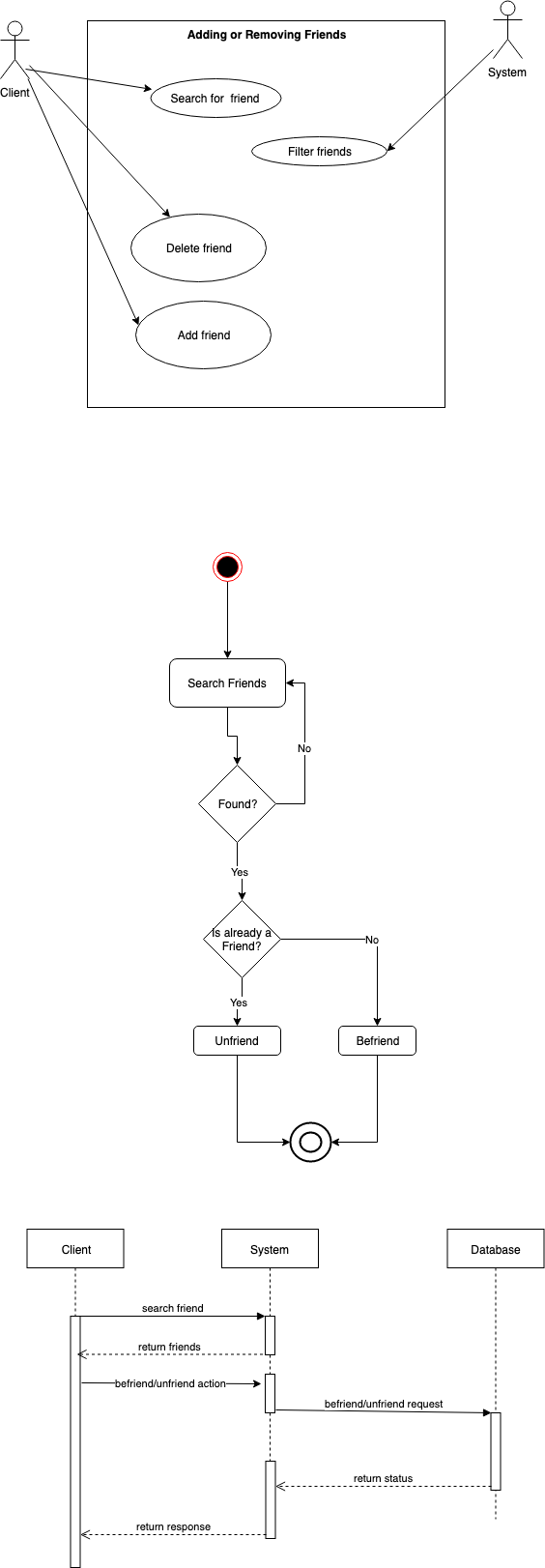
Adding or removing friends
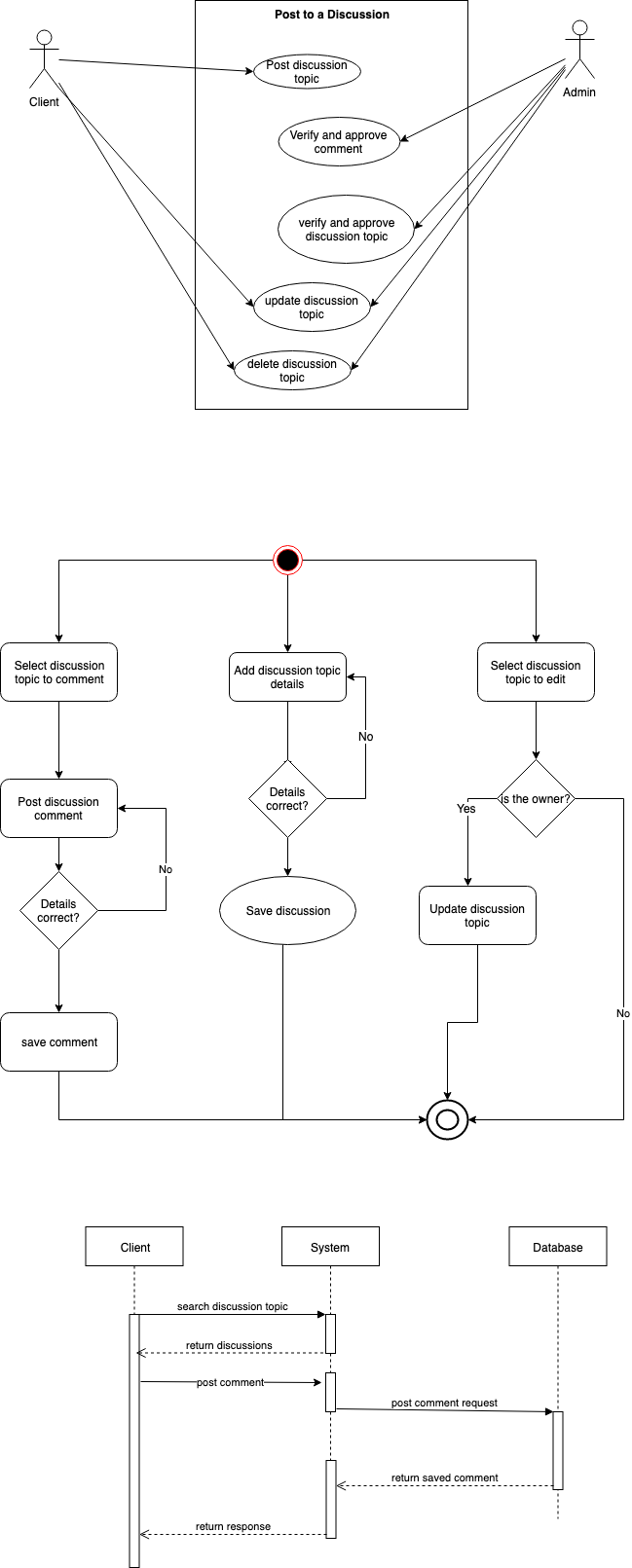
Posting to a discussion area
Login and account setup
A user accesses the system and navigates to the login form. The user then inputs his/her username and the password, then submits the form. The system evaluates the form input. If the details are invalid or incorrect, the user is redirected back to the login form. Else, the system validates the account existence. If the account does not exist, the user is redirected to the registration page. Else, the user login details are verified. Once the validation is completed, the user is logged in and redirected to the dashboard.
On the register page, the user fills out the registration form. Once done and submitted, the system validates the input. If validation is unsuccessful, the user is redirected to the registration page. Else, the system creates an account profile for the user and once done redirects the user to the dashboard
Adding or removing friends
The user searches for a friend via the search form and performs a lookup for users whose names match the search input and returns the results. The user selects a friend from the list. If the selected friend is already a friend, an option to unfriend the user pops up. Else, an opportunity to add the user as a friend is presented. The system receives the action and returns a response to the action.
Posting to a discussion area
The user chooses to either post a new discussion topic or comment on posted discussions. If the latter is selected as the desired action, the system presents a search form to the user. The user inputs search details and submit the form and perform search and return related discussions. The user selects the discussion of their choice and posts a comment. It then saves the comment to the database and returns a success response. Moreover, an administrative user can also moderate discussions and comments in the system.
Mobile Application Encryption and Network Connectivity (Joshua Teague)Making sure that the Verbania Mobile Application has safe and encrypted data is essential for the project success. There are three types of data and each type needs to be secure and different types of encryption are required. The data at rest is data that is being stored or not in use. This data could be anything from user login credentials to user likes and dislikes. Then there is data in transit. Data in transit is just as it sounds, data that is moving along the network from on destination to another. This type of data is vulnerable to different manners of attacks and requires new methods of protection and encryption. The final data type is data in use. This is data that the user is interacting with. This is the most difficult type of data to protect and requires unique security methods.
Data at Rest
Data that is at rest is data being stored for later use. This type of data can be anything stored in a database, CPU memory, memory sticks, and anything where data is stored. Data at rest in the Verbania Project will be focused to the server where the database is stored. Users will input data into the mobile application and that data will be sent to the running application on the server and then moved into the database for storage. Then when the user needs to call the data it is sent the server application and then passed on to the application the user is interacting with. The way this data is secured is to use some form of encryption. The way data is encrypted is by scrambling the data into incoherent nonsense based on a coded key. The key is the decipher that the unscrambles the encryption into readable data. Data encryption will be done when the data is stored on the server and then the key will be utilized when the data is being called on (Microsoft, 2019).
Data in Transit
Data that is moving on the network can be labeled as data in transit. Basically, any data that is in motion will fall under this classification. This could be data that is moving from the server to the mobile application or data that is moving from one user’s app to another. This data becomes vulnerable to attacks by interception means and needs to be protected while making its way to its destination. This can be done in several ways working in conjunction. The first thing that needs to be done is to use an SSL Certificate for secure transmission. The SSL works with the TSL to provide high end security. If the data is being sent via email the encryption used is PGP or S/MIME. Another alternative would be to use a file encryption tool to secure the email before transit. This will come into play when users want to send emails to each other while using the software. Using cryptographic algorithms will also provide protection when the data is not being transmitted over the web application. The fire wall will also play a vital role in protecting data in transit because it scans the traffic on the network and only allows the desired transmissions to pass through (Berkley, 2019).
Data in Use
Data in use is data that the user is interacting with at any given time. This data is vulnerable to attack and is extremely difficult to secure due to its very nature. The data that is being used is communicated by the user calling the page and then interacting with the page and the data is recorded and then transmitted to its destination. The reason data in use is difficult to secure is because encrypted data cannot be read by the end user and must be decrypted before being showed to the user. This leaves the data open for attack and more trust placed on the user. When there are extremely large amounts of users this can be a dangerous situation. Therefore, user authentication is one of the best methods of protecting data in use. The user authentication would generally be a username and password combination and the strong the combination the harder it is to penetrate. The username and passwords should be given strict combination qualifications to make it harder for attackers to replicate. There are also a secondary authentication means. These can be in the form of security questions only the user would know. Two-way authentication between different devices owned by the user. The system would send a code to one designated device and the user would then input the code onto another device to verify who the user was. Then there is email verification where the code would be sent to a trusted email and the code would be used to verify identity. One last means of protecting data in use would be to have a timeout feature on the mobile application to trigger automatic logout if the user is inactive for a certain period of time (Heron, 2012).
Business Design Document (BDD) and System Design Document (SDD) (Marcus Declouette)So, in order for Verbania to get back to the good ole days of being on top of the internet age is a few things. The infrastructure need is a Router both wireless and wired that’s connected to the internet. Then a firewall to protect the internet and the backbone switch. Then have the servers such as mail web, proxy and DNS connect to the back-bone switch. Then a fiber cord that connect to a switch that’s connected to the employee computers that’s also connected to the hub of the internet. I would also add a cloud made from IBM as they make the best technology that has security and storage of the data that will be saved and stored to the site. Security is a high priority along with storage space and being able to access the network with ease and having it work fast.
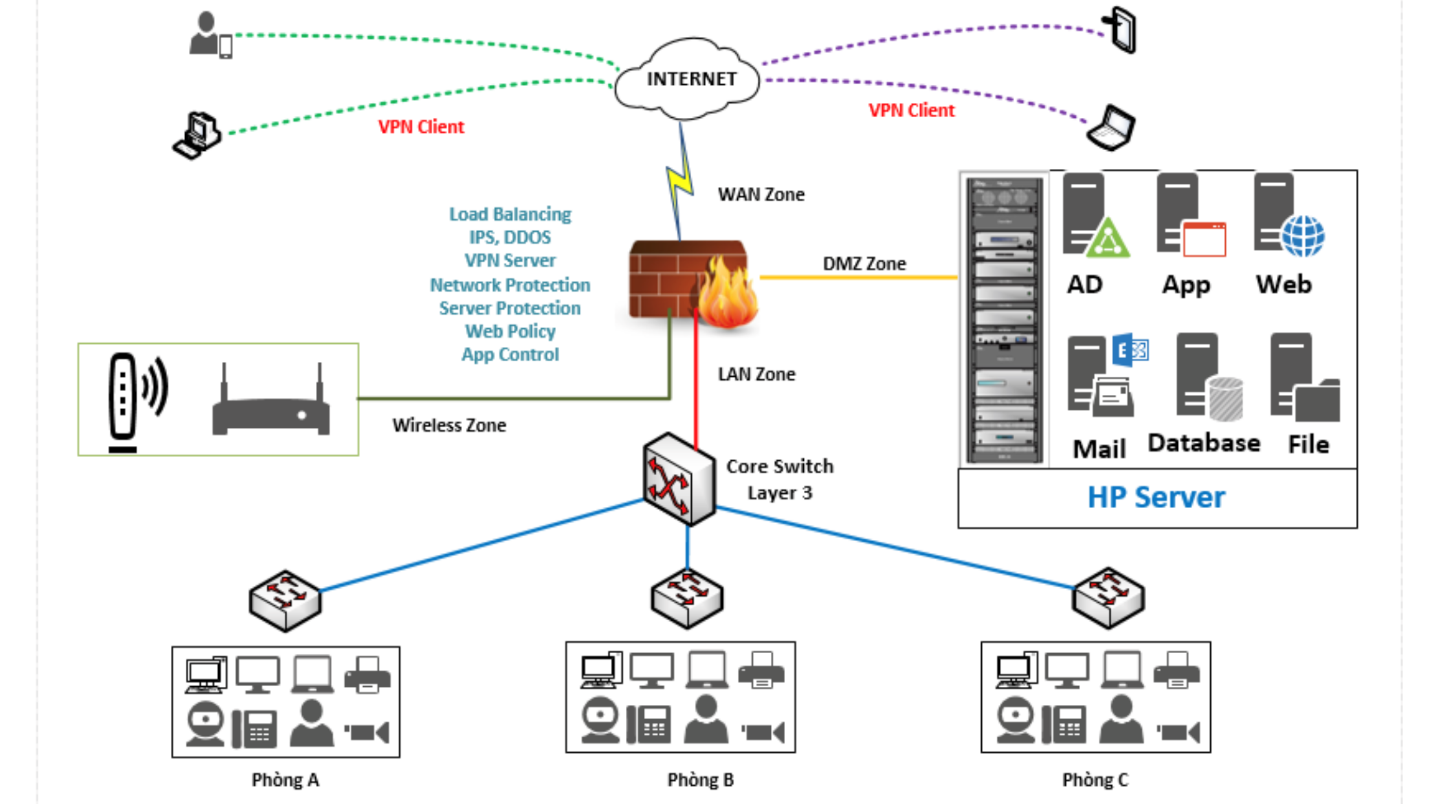
you can see from the diagram up above. The internet can be connected to multiple devices as shown because this is important as work get accomplished on many different devices in today’s society. Next is the wan zone this helps protect the intent from unauthorized user and other attempts to gain access to the server or network. If you look at to the left of the diagram you see the wireless zone. This is connected to the wireless router and router so that the devices can be connected to the internet without being connected to hard wire line. Look to the right and you will see the DMZ zone which the brain of the network is. This area holds the sever and usually connects to the entire organization. It’s usually located at the highest point of the building to avoid damage and tampering with. If you look at the bottom you see the core switch which allows the internet and severs to connect to the employees using them. It’s the last communication to the devices and employees working. What’s not shown is a remote access this allows the employees to access the internet and network from anywhere they are located. This helps as it can connect employees from anywhere.
Assumptions: Feedback: Section Five: System Implementation and MaintenanceAssumptions: Feedback: References
Berkley. (2019). Data Encryption in Transit Guideline. Retrieved July 2, 2019, from https://security.berkeley.edu/data-encryption-transit-guideline
Bisson, D. (2017, June 08). Encryption: The GDPR Standard That's Got Web Privacy Services Hopeful. Retrieved June 24, 2019, from https://www.tripwire.com/state-of-security/security-data-protection/encryption-gdpr-standard-thats-got-web-privacy-services-hopeful/
Diana, A. (2019, June 18). Integrating Social Media and Customer Relationship Management. Social Media Advances CRM to Increase Revenue, Market Share and Brand. Retrieved June 18, 2019, from http://crmsearch.com/social.php
Ellingwood, J. (2013). How to Use SSH to Connect to a Remote Server in Ubuntu | DigitalOcean. [online] Digitalocean.com. Available at: https://www.digitalocean.com/community/tutorials/how-to-use-ssh-to-connect-to-a-remote-server-in-ubuntu
Grant, M., & Kenton, W. (2019). Understanding Software-as-a-Service (SaaS). Retrieved from https://www.investopedia.com/terms/s/software-as-a-service-saas.asp
Garrison, J. (2016, December 13). What Kind of Ethernet (Cat5, Cat5e, Cat6, Cat6a) Cable Should I Use? Retrieved from https://www.howtogeek.com/70494/what-kind-of-ethernet-cat-5e6a-cable-should-i-use/
Heron, S. (2012, April 26). Protecting Data in Use. Retrieved July 2, 2019, from http://www.infosecisland.com/blogview/20173-Protecting-Data-in-Use.html
Hibbert, B. (2016). Securing Your Remote Access Solution with Better Enterprise Password Security | BeyondTrust. [online] Beyondtrust.com. Available at: https://www.beyondtrust.com/blog/entry/securing-remote-access-solution-enterprise-password-security
Mailheau, R. (2019, June 14). Demystifying Ethernet Types— Difference between Cat5e, Cat 6, and Cat7. Retrieved from https://planetechusa.com/blog/ethernet-different-ethernet-categories-cat3-vs-cat5e-vs-cat6-vs-cat6a-vs-cat7-vs-cat8/
Mendenhall, N. (2015, March 3). How To Integrate Social and CRM Data to Improve Your Twitter and Facebook Ads. Social Media Marketing | Social Media Examiner Your Guide to the Social Media Jungle. Retrieved June 18, 2019, from https://www.socialmediaexaminer.com/integrate-social-and-crm-data-to-improve-your-twitter-and-facebook-ads/
Microsoft. (2019, May 6). Microsoft Azure Data Encryption-at-Rest. Retrieved July 2, 2019, from https://docs.microsoft.com/en-us/azure/security/azure-security-encryption-atrest
Mitchell, B. (2019, June 17). Understanding Infrastructure Mode in Wireless Networking. Retrieved from https://www.lifewire.com/infrastructure-mode-in-wireless-networking-816539
Molenaar, R. (2017, August 23). Router Security Policy. Retrieved June 25, 2019, from https://networklessons.com/cisco/ccnp-route/router-security-policy
Mowl, J. (2012). How to Choose the Best Hardware and Software for Your Business. Retrieved from https://www.entrepreneur.com/article/224538
Overview of Cloud Game Infrastructure. (2019). Retrieved from https://cloud.google.com/solutions/gaming/cloud-game-infrastructure
Parker, J. (2012, October 01). Business, User, and System Requirements. Retrieved June 10, 2019, from http://enfocussolutions.com/business-user-and-system-requirements/
Rouse, M. (2015, March). What is multifactor authentication (MFA)? - Definition from WhatIs.com. Retrieved June 16, 2019, from https://searchsecurity.techtarget.com/definition/multifactor-authentication-MFA
Ruben, P. (2016, August 23). 7 Database Security Best Practices. Retrieved June 14, 2019, from https://www.esecurityplanet.com/network-security/6-database-security-best-practices.html
Rykhoff, N. (2016, March 16). Security for Small Business Server Rooms. Retrieved June 19, 2019, from https://quantumsecuritygates.com/security-for-small-business-server-rooms/
Utilize Windows. (2013). The Importance of Physical Security of Servers - Utilize Windows. [online] Available at: https://www.utilizewindows.com/the-importance-of-physical-security-of-servers/
42



