Cyber Security Engineers are responsible for safeguarding computer networks and systems in an organization in order to protect the sensitive data they store. Take on the role of Cyber Security Engin
CMGT/400 v7
Threats, Attacks, and Vulnerability Assessment Template
Instructions: Replace the information in brackets [ ] with information relevant to your project.
A Cyber Security Threat Analyst conducts analysis, digital forensics, and targeting to identify, monitor, assess, and counter cyber-attack threats against information systems, critical infrastructure, and cyber-related interests. Take on the role of a Cyber Security Threat Analyst for the approved organization you chose. Research the following information about the organization you chose and complete the Threats, Attacks, and Vulnerability Assessment template.
Brainhub LimitedReady to build your app
Assessment ScopeWhat are the tangible assets included? (Must include virtualization, cloud, database, network, mobile, information systems.) Identify all information systems, critical infrastructure, and cyber-related interests and combinations that will be assessed. Also, describe information systems, critical infrastructure, and cyber-related interests which will not be assessed and explain why.
Virtualization
This will involve virtual storage devices, desktop virtualization etc.
Cloud
This will include computing services that are offered to users such as cloud databases
Network devices
This will include network cables, patch panels, routers, switches, gateways, modems, wireless access points, firewalls and proxy servers
Servers
This will include mail servers, web servers, application servers, telnet server and database servers
Mobile devices
This will include smart phones and tablets
Information system
This will include Operating System, utilities such as antivirus, commercial applications, database management system etc.
System ModelA diagram and descriptions of each asset included in the assessment scope.
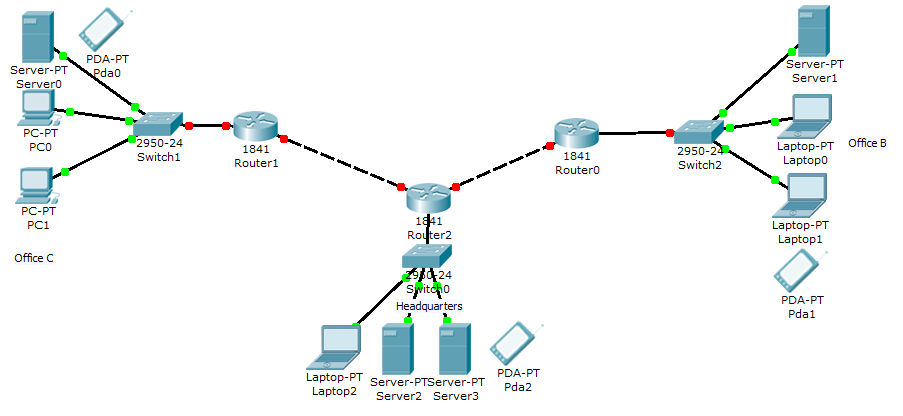
Router – router is a networking device that forwards packets between networks
Switch – switch is a network device that connects devices together in a network
Firewall – firewall is software or hardware put on the network and it prevents forbidden communication
Server – server is a computer or computer program that manages access to a centralized resource in a network
Mobile devices – these are mobile devices such as smart phones and tablets
Existing CountermeasuresDescribe existing countermeasure already in place.
Password policies
Passwords needs to be changed every fortnight
Password should not be less than 10 characters and should contain letters, numbers and special characters such @
Users should not leave their passwords in plain sight
The system should log out a user who has try to input password thrice without succeeding
Network devices and infrastructure
Network devices such as routers should only be accessed by network administrator
The network administrator should access the network devices such as switches over a Secure Shell (SSH)
The network devices should have an encrypted password
Antivirus policy
All computers and mobile devices should be installed with an up to date antivirus
Always scan devices attached to the computer before using them
Scan online attachments before opening them
Don’t download files from unknown sources. For example, don’t download apps on Android devices that do not originate from Google play store
Threat Agents and Possible AttacksDefine 12 to 15 threat agents and possible attacks.
Advanced persistent threat – this is whereby a group of elite team of hackers target users so as to steal information over a specific period of time using techniques such as phishing etc.
Malvertising attack – an attacker can put a malicious code in an online advert and when a user clicks on the advert then the code infects the system
Phishing attack – this is whereby an attacker sends emails or sets up a website asking a user to enter personal details such as bank details leading to identity theft.
An employee can decide to steal laptop from the office leading to physical attack
Scan attacks – an attacker can come up with a code that looks at opened ports on a system and exploiting that vulnerability
An attacker can perform SQL injection – this is whereby an attacker enters SQL commands on an input text box resulting in manipulating the data on the database
Malware attacks – an attacker can set up a website that has kits to find vulnerabilities in a system and when a user visits that website, malware is forced into their system.
Worm attacks – an attacker can attach a worm to an email and when unsuspecting user opens that attachment, then the worm starts infecting his/her system as it propagates through the network.
Denial of services attack- this is whereby an attacker overwhelms the server with traffic leading the server to crash
Brute force attack – an attacker with time on his hand can keep on guessing the network passwords through trial and errors and eventually gaining access of the system.
Software such as an antivirus can lack the latest security patches leading to attacks on a system
Cross site scripting – a user can attack a website server through inputting data on a website input text box.
Identify 7 to 9 exploitable vulnerabilities.
Lack of proper design in programming of software using JavaScript
Lack of having well thought and implemented passwords
Lack of having an antivirus that is up to date with the latest security patches
Lack of closing unused ports
Having unprotected communication lines
Having of poorly designed network architecture
Lack of performing adequate recruiting process of personnel
| Threat History Events | Duration | Business Impact | Threat Resolution |
| Lack of updating antivirus | 3 months | Slowed computers | Bought Kaspersky antivirus |
| Network attacks such as worm in infected mail attachment | 1 month | Slowed computers | Bought internet antivirus |
| Poorly designed programs | 4 months | Unsatisfied customers | Improved our software testing phase |
| Risk | Probability | Priority | Owner | Countermeasures/Contingencies/Mitigation Approach |
| Physical attack | high | high | The company | Counter it by enforcing policies and ensuring locking of rooms etc. |
| Network attacks | higher | higher | Network administrator | Enforce network security policies, email usage policies, password policies etc. |
| System attack | high | high | System administrator | Enforce security policies |
Copyright© 2018 by University of Phoenix. All rights reserved.



