hi
Home Work # 02
Problem 1:
Suppose that Alice and Bob are employees of a fake company named ’foobar’. All employees of the company use the RSA protocol for encrypting and signing their emails. RSA public keys of all employees are stored in a file on the company’s server. The contents of this file are available for public view on foobar’s non-SSL enabled key download web site, hosted at this fake URL: http://foobar.com/pubkeys.html
The email client software used internally in the company has an email signing feature. It works as follows: When the user clicks on the ’Sign and Send’ button in his email client, the client software appends a special ’signature’ tag to the regular email header before sending the email. The signature tag contains the author’s name and the date signed by the author’s RSA private key. The receiver’s email client software automatically verifies the signature tag, if present, by first obtaining the RSA public key of the sender from the foobar’s key web site. It then verifies that the email sender’s name and the date in the regular email header match the signed name and date in the signature tag.
Suppose that a curious employee, Eve, is able to break into the server and alter the file containing RSA public keys. How should Eve alter that file so that she can read confidential encrypted emails sent between Alice and Bob? Justify your answer. Your solution to this problem should be different from the one proposed for Problem 1 (Be precise; vague answer will not be accepted).
Vernam cipher
Consider the following letter encodings:
| Letter | A | E | I | M | O | R | T | V |
| Encoding | 000 | 001 | 010 | 011 | 100 | 101 | 110 | 111 |
A message M = MARIO is Vernam encrypted into ciphertext C = AOAMV. Find the corresponding encryption key (note that it should be 5 letters long). Provide details of your cryptanalysis. Vague answer will not be accepted.
Consider the following two ciphertexts C1= MAOEE and C2=RTITR that are obtained by Vernam encrypting messages M1 and M2, respectively, using the same encryption key. The letter encodings is the same as shown in Step (a). The encrypted messages are two names. Let mi,k be the kth letter in the message Mi.
The following is known about the messages (names): m1,1 = R and m2,4 = T. Using this limited information, try to recover messages M1 and M2, as well as the encryption key. Provide details of your cryptanalysis. Vague answer will not be accepted.
Assume that Malice mounts the Man-in-the-Middle (MITM) attack on Diffie-Hellman key exchange protocol as illustrated in Fig. 1.
Let YA = gXA mod p, and YB = gXB mod p be Diffie-Hellman public keys of Alice and Bob, respectively. Private keys XA, XB and XM remain known only to the respective owners Alice, Bob and Malice. Suppose that Malice wants to establish a single Diffie- Hellman key, KABM = gXAXBXM mod p, that he, Alice and Bob all share. Does the attack illustrated in Figure 1 accomplish this? Justify your answer (Be precise; vague answer will not be accepted).
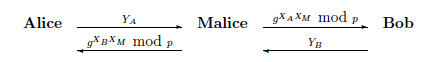
Fig. 1: The MITM attack against Diffie-Hellman protocol executed between Alice and Bob
Two parties Alice and Bob wish to exchange a session key Kab with the help of a trusted party Cathy. Initially, Alice has a shared key Kac with Cathy. Likewise, Bob has a shared key Kbc with Cathy. The following protocol is used to exchange the session key Kab.
First, Alice generates a new session key Kab. She then encrypts this key and a timestamp Ta using Kac. She sends the encrypted message to Bob. Bob, in turn, encrypts the received message and a new timestamp Tb using Kbc. He then sends the encrypted message to Cathy. Cathy, in turn, double-decrypts the message (i.e. decrypts the message twice) and extracts the session key Kab. Then, she encrypts the session key Kab using Kbc and sends the message to Bob.
Show graphically how the protocol works. Use arrows and numbers to complete the following diagram. All symbols used in your answer must be justified and explained clearly.
Use the Alice-Bob notation to describe the protocol. Use A for Alice, B for Bob and C for Cathy.
Problem 2:
Objective: In this question, you will
Explore block cipher modes and experience the effect of using a weak key DES
Explore an example of brute force analysis and the use of AES
Note: For the remaining questions, you are requested to show all the steps that you've used, followed by the content of the working area window of CrypTool that you have obtained in each step (wherever applicable) in order to justify the answers that you provide. Also, be precise on all your answers. Vague answers will not be accepted.
Task 1: Use of Block Cipher Modes
For this task, you will encrypt the same message using CrypTool, and the same key twice: using the Electronic Codebook (ECB) mode first, then the Cipher Block Chaining (CBC) mode.
• Open CrypTool > File > New >. Enter your plaintext in the working area window:
Plaintext (8 bytes length in hexadecimal): 456ACFDB
• Copy and repeat this text twice (with no space inserted)
• Select Encrypt/Decrypt > Symmetric (Modern) > DES (ECB)
Enter your key (in hexadecimal): 11 CC 11 BB 00 AA 00 AA
• Click View, then click Show as HexDump so that the ciphertext is displayed in hexadecimal. Copy the encrypted text in hexadecimal.
• Select Encrypt/Decrypt > Symmetric (Modern) > DES (CBC). Enter the same key that you have used in Step 3. Copy the encrypted text
• Compare the encrypted text in Step 3 (ECB mode) and Step 5 (CBC mode). What can you say about the block cipher in each mode? Justify your answer
Task 2: Weak Key DES and Brute Force Analysis
1. By using the plaintext and key below, encrypt the plaintext using CrypTool in DES (ECB) mode.
| Plaintext | She sells sea shells at the sea shore |
| Key | 0110 0110 0001 0001 |
2. Encrypt the plaintext and key given in Question 1 using the DES (CBC mode).
Encrypt the same plaintext twice. What can you conclude from the ciphertext and key used in this encryption?
3. What is the difference between the ciphertext obtained using the ECB mode versus that obtained using the CBC mode? What can you conclude about the key in each of these modes?
4. Apply Brute Force Analysis to the ciphertext that you got from Question 1.
Select Analysis > Symmetric (Modern) > DES (ECB)
On the pop-up window, replace the asterisk “*” by inserting part of the key given in
Question 1 (for example: 0111 0111 **** ****). Then click “Start”. A pop up window will appear to indicate that the analysis is in progress. Do not wait for the analysis to complete. Click “Cancel”. Did the original plaintext appear in the pop-up windows?
5. By using DES (ECB) mode, encrypt the plaintext given in Question 1 using the following key: 7C64A1BB779A89AB
6. Apply the Brute Force Analysis on the ciphertext obtained from Step 5 and show the results.
7. What did you learned from this experiment?
Task 3: Operations of the AES
For any AES calculator you will find online, you will need to do the calculation (for AES encryption) manually from round to round, up to at least 10 rounds. You can use any of these calculators:
http://testprotect.com/appendix/AEScalc http://extranet.cryptomathic.com/aescalc/index http://aes.online-domain-tools.com
Using this AES Calculator, encrypt the plaintext given below using the key in
128-bit (32 hex digit). To do so:
Copy the value of the plaintext and key in the AES Calculator. Click encrypt, and copy the obtained ciphertext in the space provided in the table below:
| Plaintext1 | 0111 2333 3355 5687 4477 aacc aaad ccbb |
| Key | 0101 0203 0505 0707 0707 0d0d 0a0a 0a0a |
| Ciphertext1 |
Note how the value of the state (result of each round) changes round by round. Copy the ciphertext (from the AES calculator) for each round into Table 1 shown below, precisely in row CTxt1 (as shown) – where CTxt1 denotes Ciphertext1.
Consider Plaintext2 given below. Encrypt it using the same Key as in Step 2a and then copy the obtained ciphertext in the space provided in the table below. Compare the values of Plaintext1 with that of Plaintext2. Determine what that bit number is (note that bit numbers start with 1 and ends with 128 from left to right).
| Plaintext2 | 0111 1133 5555 5577 8899 aaaa addd cccc |
| Ciphertext2 |
Copy the ciphertext obtained for each round into the above-mentioned
Table 1, writing it on row CTxt2 – where CTxt2 denotes Ciphertext2.
Calculate the bit difference in the ciphertext for each column. Then determine the total number of bit difference for each round. You should run up to a minimum of 5 rounds of AES. You can use Table 2 given below to find the bit difference. Note: The … means you need to expand the chart to include the missing values.
Table 1: Fill out the plaintext and ciphertext hex values (1 hex value for each column)
| Round | Text Type |
|
|
|
|
|
| Total in bit difference |
|
| PTxt1 | 0 | 1 | 1 | 1 | … | b |
|
| PTx2 | 0 | 1 | 1 | 1 | … | c | ||
| Diff |
|
| … |
| ||||
| 0 | CTxt1 |
|
| … |
|
| ||
| CTxt2 |
|
| … |
| ||||
| Diff |
|
| … |
| ||||
| 1 | CTxt1 |
|
| … |
|
| ||
| CTxt2 |
|
| … |
| ||||
| Diff |
|
| … |
| ||||
| 2 | CTxt1 |
|
| … |
|
| ||
| CTxt2 |
|
| … |
| ||||
| Diff |
|
| … |
| ||||
| 3 | CTxt1 |
|
| … |
|
| ||
| CTxt2 |
|
| … |
| ||||
| Diff |
|
| … |
| ||||
| 4 | CTxt1 |
|
| … |
|
| ||
| CTxt2 |
|
| .. |
| ||||
| Diff |
|
| … |
| ||||
| 5 | CTxt1 |
|
| … |
|
| ||
| CTxt2 |
|
| … |
| ||||
| Diff |
|
| … |
|
What can you conclude about the avalanche effect in AES? Justify your answer. Vague answer will not be accepted.
Note: Avalanche effect occurs in AES when a change in the ciphertext or plaintext would result in a change in the AES output.
Table 2: The row and column are specified in hexadecimal digit. To find the bit difference, simply match the hexadecimal digit, and find the intersection cell of row and column. The digit in the intersection cell is the difference in bit.
8



