Part 1 As the IT liaison, Senior tasked you with defining the technical components of the SLA with the consultants. Write a 2-page summary that includes: A listing of the Drotos Engineering IT manager
IntroductionThis paper will look at security technologies to use to meet our security requirements and design for the proposed cloud-based network environment. We will also look at automated scanning and monitoring techniques or tools to use for the cloud-based environment and also list the steps to implement the tools.
Security technologiesWhen it comes to security in cloud-based environment, both parties i.e. the cloud service provider and the consumer of the services must ensure they practice security measures so as to prevent attacks. It is the responsibility of the cloud service provider to ensure that their infrastructure is secure and client’s data and applications are protected. It is also the responsibility of the consumer (Drotos Engineering) to ensure that applications are accessed after the user has been authenticated.
The security technologies employed in a cloud-based environment include:
Virtualization
According to Rivera A (2018) virtualization is creating of virtual version of something, for example, we can have virtual server, virtual operating system, virtual network resources etc.
Cloud service providers store data from several clients and virtualization can ensure that one client does not accidentally view another client’s data.
Encryption
According to Pfleeger C et al (2015) encryption is encoding a message so that its meaning is not understood by a layman. Pfleeger C et al (2015) define decryption as reversing an encrypted message to its original form. The cloud service provider will use encryption to ensure security of the data. The cloud service provider will use Attribute-based encryption (ABE).
Data security
The cloud service provider will ensure that the data is secure and it is confidential, maintains integrity and it is available when needed.
Multi-factor authentication
The cloud service provider will provide multi-factor authentication whereby a user does not only need to provide a password but he/she also needs to provide a secret key/pin from a special hardware device and this can be seen as hard token or even from software apps.
Automated scanning and monitoring techniques or toolsThe cloud service provider is responsible for monitoring the services it provides to consumers e.g. network, storage service etc. On the other hand, the consumer (Drotos Engineering) is responsible for monitoring the systems and applications created by the consumer using these services.
The network will be monitored using PRTG network monitoring tool. According to PRTG website paessler.com the PRTG network monitoring tool monitors switches, routers, firewall, workstations, servers, VMware etc.
We will use New Relic to monitor database performance
We will use Zabbix to monitor our systems and applications
High-level steps to implement the recommended toolsThe most critical one is the network since without the cloud-based network we cannot access these other services such as storage services etc.
Implementation of PRTG networking tool
You need to buy the PRTG monitoring tool from their website Paessler.com and download it. After downloading it, you need to install it and run through the installation wizard. The following image depicts the PRTG system administration interface.
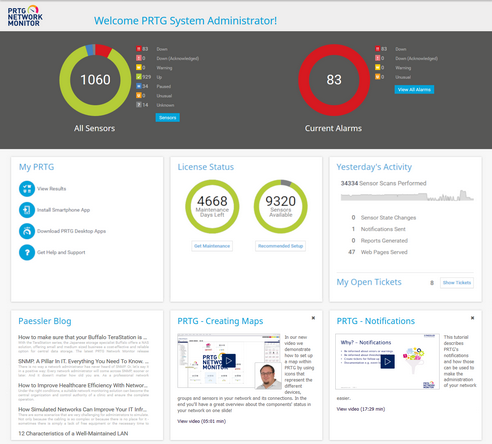
Implementation of the new relic monitoring tool
You need to buy the new relic monitoring tool from their website Newrelic.com and install it and from there you are able to monitor slow transactions, error rates, database performance etc.
IntroductionWe are currently operating on a traditional private network. For us to be able to ensure that our employees can access files and software locally and remotely, software applications and storage are scalable as employee number increases, software application response time is high even with employee growth, business continuity even in case of network failure etc. we need to migrate our network to cloud-based network.
This paper will look at the rationale for transitioning from the traditional network environment to the cloud-based environment. We will also look at the hardware requirements to support the cloud-based environment. We will list the steps to implement the recommended cloud-based solution. We will finish by giving our opinion on whether the solution will address our business needs or we need further modifications.
Rationale for transitioning from traditional network to cloud-based environmentBefore looking at the reasons for transitioning, let’s first define traditional network and cloud-based network.
According to Wadia Y (2016) traditional network consists of switches and routers that are connected to physical hardware and its main purpose is transmitting and forwarding packets from one place to another.
Wadia Y (2016) says that cloud based network has virtual devices such as virtual servers, virtual routers and switches that are provided by cloud service provider. An organization doesn’t need to install these devices.
The reasons for migrating from traditional network to cloud-based environment are:
Security
Cloud based solution is heavily filtered compared to the traditional network. Cloud service providers allow only unicast datagrams while restricting all broadcast datagrams over their network. Cloud service providers have got security specialists who oversee network security issues such as denial of services since they are in the business of providing cloud based networking.
Database server and other severs
Cloud-based solution has got servers such as database servers, application servers, mail servers etc. The database server usually scales nicely with increase in data volume and thus catering for growth in organization.
Price consideration
It is cheaper to use third party servers for storage, computing, applications etc. than buying our own servers and having them configured at the organizations premises. The same applies for network devices, it is cheaper to use cloud service provider network devices than buying our own and configuring them.
Reduction in work load
Since we are having our applications and database storage provided by cloud service provider, we can only focus on our core business as Drotos Engineering and not focus on things such as, is our network antivirus up to date? Is our database secure and is our data integrity intact?
Hardware requirements to support cloud-based environmentWe will not be adding any hardware as an organization since we will be using the cloud service provider hardware such as virtual switches, database servers, application servers, mail servers etc.
Implementation of the recommended cloud-based solutionWe don’t need the network hardware to implement the cloud-based solution. What we need is OpenFlow protocol, which is a software-defined networking protocol that issues access to forwarding plane of a network switch or router over the network. We also need an interface that facilitates communication of applications through Application Programming Interfaces (API).
Additional considerationsWe need to consider compliance. Does the cloud-based provider comply with various compliance policies such as FERPA etc.
We need to consider whether we will receive technical support for the service or not
Final opinionThe migration to cloud-based solution will address all our business needs since our data storage and usage intends to increase. Cloud service providers always keep their software up to date with the latest patches, therefore, we are guaranteed that we will be using the latest Microsoft Office package for our daily operations.
Management strategyThe network administrators will be responsible for monitoring the network every hour and this will include the virtual routers, switches etc. They will give a report on the health of the network every fortnight.
The database administrators will be responsible for monitoring the database every hour and they should give a report to the top management every week.
The systems administrator will monitor the systems every hour and they will also give a report on the systems and applications every fortnight.
Backup strategyWe will use two backup strategies. They include:
On-premises backup
Remote backup
On-premises backup
According to Lo K and Harmon E (2012) on-premises backup is whereby you copy your data on a hard drive, shared drive or any other media device, either manually or at specified intervals.
It will be the duty of the database administrators to ensure that our data is copied to external hard drives on weekly basis.
Remote backup
According to Lo K and Harmon E (2012) remote backup is whereby a computer sends data to a remote center at specified intervals.
Since we will be using cloud-based services, our data will be sent to cloud service providers’ servers automatically.
Full and incremental backup planA full backup is a complete backup of all files while an incremental backup is a backup of files that changed since the last full backup.
Our database administrators will ensure an incremental backup is done every week and a full backup every month.
Planned use of automated toolsThe automated tools such as network monitoring tool will be installed and monitored by the network administrator every hour. The database monitoring tool will also be installed and monitored by the database administrator every hour. The automated monitoring tools will be able to update themselves when new patches are introduced to the market. The systems monitoring tool will also be monitored every hour by the systems administrator.
Types of disastersThe types of disasters and potential causes of business interruption include:
Natural hazards
Human-cause hazards
Accidents and technological hazards
Our DR/BC will cover natural hazards that may affect business operations such as cold weather related hazards (avalanche, severe snow, ice storm, hail storm), warm weather related hazards (floods, fire, hurricanes, cyclones, tornado, wind storm), geological hazards (tsunami, earthquake)
The DR/BC will also cover human-cause hazards such as terrorism, cyber-attacks, arson, theft etc. We will also cover accidents and technological hazards such as power outage, internet infrastructure outage, communication infrastructure outage etc.



