Project rollout begins after a project has been implemented, tested, and judged stable and functional enough to be moved into production. The project rollout process comprises of specific steps that m
Project Plan Draft
Instructions: Fill out each of the sections below with information relevant to your project. Be sure to include the company name associated with your project.
CHASE BANK
Project Plan Draft
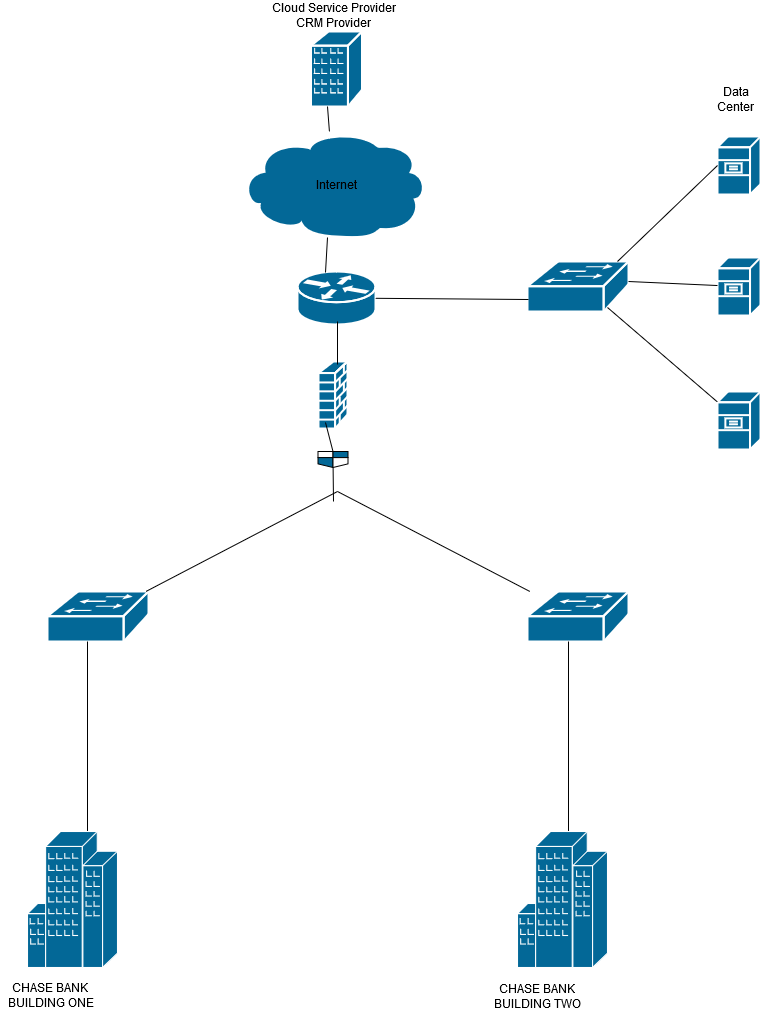
Network Technology Recommendations
Network Technology Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Cost | We will select our network technology based on cost | Installation and configuration of the network needs to be well done and cheap |
| Network growth | We will consider a network that allows growth | Network needs to facilitate growth due to company expansion |
| Reliability | We will consider a network that is reliable | It needs to be easy to detect faults and isolate them |
| Security | We will consider a network that is secure | Network needs to be secure from cyber threat attacks |
Network Technology Recommendation
| Recommended Network Technologies | Description | Benefits | Aggregate Selection Criteria Score |
| LAN | LAN stands for Local Area Network. This is a network that connects groups of computers within a building or two or three buildings. It uses cables etc. | LAN allows communication between computers on the same network or outside network through the use of routers. | |
| WLAN | WLAN stands for Wireless Local Area Network. It will be used to allow smart devices such as tablets to access the network | Will allow portable devices such as tablets to access the network |
Network Technology Vendor Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Technology solution | We will look at the network technology used by vendors. Some vendors may have superior technology solutions than others while others may only support certain technologies such as Cisco etc. | The network technology solution needs to be current and superior |
| Portfolio | We will look at the portfolio of the vendor and see what they have done in the past years | The company needs to have done a couple of network technology projects |
| Cost | We will look at the price offered by each vendor |
Network Technology Recommended Vendors
| Vendor Name | Vendor Strengths | Vendor Weaknesses | Products / Services Provided To Project | Aggregate Selection Criteria Score |
| Cisco | It’s a well-known brand Its strong point is networking technology | Products are costly for micro enterprises | Installation and configuration of network devices | |
| Extreme networks | Boasts of acquiring Zebra Technologies WLAN and Avaya’s networking business | Not well known in remote areas | Installation and configuration of network devices |
Network Technology Deployment Challenges
| Deployment Challenge | Deployment Challenge Description |
| Compatibility | Some of the new network devices may not work with the old devices |
| Training | If the network devices are new then the network administrator needs to be trained on the working and configuration of the new devices |
Technology Adoption Methods
| Method Name | Method Description |
| Technology Acceptance Method | This is a model that shows how the user will come to accept and use the network system. This is contributed by how easy it is to use the network and also whether the network improves performance of the user and the company at large. |
Cost/Benefit Considerations
| Benefits | Costs | Considerations |
| Communication | It is costly to implement a network | You need to consider bandwidth |
| Transfer of files etc. | You need to consider training of network administrators |
Database System Recommendation
Database System Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Security | We will consider the security of the database system | The database system needs to enforce security of the data |
| Cost | We will consider the cost of the database system | The database system needs to have a reasonable price |
| Performance | We will consider the performance of the database system | The database system needs to have a high performance |
| Reliability | We will consider whether the database system is reliable or not | The database needs to be reliable and recover when failure occurs |
Database System Recommendation
| Recommended Database System | Description | Benefits | Aggregate Selection Criteria Score |
| Oracle database system | Oracle is a database management system that is owned by Oracle Corporation and its used as a database and also for online transactional processing and data warehouse | Oracle offers benefits such as: Data storage, backup and recovery, supports SQL dialect, can scale nicely with increase in data, security etc. | |
| MySQL database system | MySQL is a relational database management system that I open source | MySQL offers benefits such as: Data security, high performance, scalability, availability etc. | |
| Oracle data warehouse | Oracle Autonomous data warehouse is a data warehouse that allows scaling and also quick performance querying | It offers scaling of data and stores historical data | |
| Oracle data mining | Oracle data mining allows future decision making, prediction, anomaly detection etc. | Facilitates prediction e.g. sales prediction and decision making |
Database System Vendor Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Cost | We need to consider the price of database system and installation, training etc. of each vendor | The vendor price needs to be reasonable |
| Support | We need to consider whether the vendor will offer maintenance and support of the database system | The vendor needs to provide support when things go wrong |
Database System Recommended Vendors
| Vendor Name | Vendor Strengths | Vendor Weaknesses | Products / Services Provided To Project | Aggregate Selection Criteria Score |
| Oracle | Oracle boast to be the first database designed for cloud | The database system is costly for production use | Data storage, security of data, backup and recovery of data | |
| MySQL | MySQL database is used widely for website applications | The enterprise editions are costly | Data storage, backup and recovery, data security etc |
Database System Deployment Challenges
| Deployment Challenge | Deployment Challenge Description |
| Training | We will need to train users on how to use the new database system and therefor incurring costs and also time spent on training instead of doing other activities that will benefit the organization |
| Resistance | Sometimes people are resistant to change so we may face resistance while deploying the database system |
Technology Adoption Methods
| Method Name | Method Description |
| Technology Acceptance Method | This is a model that shows how the user will come to accept and use the database system. This is contributed by how easy it is to use the system and also whether the system improves performance of the user and the company at large. |
Cost/Benefit Considerations
| Benefits | Costs | Considerations |
| Data storage | It is costly to implement database system | You need to consider training of users |
| Data recovery in case of failure | You need to consider resistance from users | |
| Easy data manipulation | ||
| Security of data is enforced |
Software Application Recommendations
Software Application Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Integration | We will consider whether the software application integrates with other software | The software needs to integrate with other systems |
| Improved sales process | We will consider whether the software has improved the sales process | The software needs to improve the sales process |
| Usability | We will consider whether the software is easy to use | The software needs to be user-friendly |
Software Application Recommendation
| Recommended Software Application | Description | Benefits | Aggregate Selection Criteria Score |
| Sales software application | The sales software application is to improve the sales process of the financial institution | Improved sales process Integration with other systems User-friendly Increased company revenues |
Software Application Vendor Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Time | The time taken to come up with the software | The software application needs to be delivered on time |
| Programming language | The programming language that will be used to come up with the software application | The programming language needs to be cross-platform, current, stable and widely used by enterprises |
Software Application Recommended Vendors
| Vendor Name | Vendor Strengths | Vendor Weaknesses | Products / Services Provided To Project | Aggregate Selection Criteria Score |
| Eleks Company | It is an international software development company It has a lot of customers | It only deals with Java technology | A fully functioning sales software application | |
| End Point Company | It has a lot of clients | It only deals with Java technology | A fully functioning sales software application |
Software Application Deployment Challenges
| Deployment Challenge | Deployment Challenge Description |
| Resistance | The users may resist the changes |
| Training | The users will need to be trained |
Technology Adoption Methods
| Method Name | Method Description |
| Technology Acceptance Method | This is a model that shows how the user will come to accept and use the software application system. This is contributed by how easy it is to use the system and also whether the system improves performance of the user and the company at large. |
Cost/Benefit Considerations
| Benefits | Costs | Considerations |
| A software that integrates with other systems | Time Since requirements may change the software may not be delivered on time | We need to consider the programming language used We need to consider the methodology used |
| A software that facilitates improvement of sales | ||
| A software that is easy to use |
Cloud Services Recommendations
Cloud Services Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Cost | We will consider the cost of the cloud service provider | Will need to select a cloud service provider that offers great services and also saves us money |
| Compliance | We will consider whether the provider complies with all required compliance such as security etc. | Will need to select a cloud service provider that is at per with various compliance such as GDPR, HIPAA etc |
| Type of cloud service | We will consider the type of service that we need e.g. software-as-a-service, infrastructure-as-a-service, and platform-as-a-service |
Cloud Services Recommendation
| Recommended Cloud Services | Description | Benefits | Aggregate Selection Criteria Score |
| Software-as-a-service | This is where host applications will be available to Chase financial service provider through the use of the internet. | Reduced cost compared to if the applications were on-premise Saas allows scalability |
Cloud Services Vendor Selection Criteria
| Selection Criteria Name | Selection Criteria Description | Selection Criteria Value (Weighting In Points) |
| Cost | We need to consider the price of the service offered by the vendor | Service must be great and cheap |
| Portfolio | We need to consider the clients that the vendor has offered the services to | Service provider must have a good portfolio |
| Compliance | We need to consider viewing the compliance documents if available | Service provider must have compliance documents |
Cloud Services Recommended Vendors
| Vendor Name | Vendor Strengths | Vendor Weaknesses | Products / Services Provided To Project | Aggregate Selection Criteria Score |
| Amazon | Has several services at reasonable prices It has a strong brand | Not well known in developing markets | Software-as-a service product | |
| | Offers a couple of services It’s a well-known brand | Services are costly to micro enterprises | Software-as-a-service product |
Cloud Services Deployment Challenges
| Deployment Challenge | Deployment Challenge Description |
| Internet | Cloud services rely on the internet to access them. If the internet is down may mean lack of access to the services |
| Third party | It may be difficult to have your data saved with third party company especially if it sensitive in nature |
Technology Adoption Methods
| Method Name | Method Description |
| Technology Acceptance Method | This is a model that shows how the user will come to accept and use the cloud-based CRM system. This is contributed by how easy it is to use the system and also whether the system improves performance of the user and the company at large. |
Cost/Benefit Considerations
| Benefits | Costs | Considerations |
| Use of CRM service offered by cloud-based | May be costly to implement since the service is paid monthly or annually | You need to consider training of users on the CRM system |
| You need to consider resistance from users |

From the diagram we can see that a customer interacts with the system he/she can perform various transactions such as requesting credit card, borrowing loan, perform over the counter transaction, check balance, and also access the online.
Software Test Plan
Enter the name of the project here.
Describe the purpose of the project here.
The purpose of the project is to improve the sales software application which lacks in various areas such as, it does not integrate with other systems, and it does not generate reports that maybe used in proper decision making. The project will improve the sales process and we will also incorporate a cloud-based CRM.
Features To Be Tested / Not To Be Tested
The features that will be tested include:
Modules
Integration of the modules
Database testing
Integration of the system with database
Integration with other systems
Graphical User Interface testing
Functional testing
Security testing
User acceptance testing
Performance testing
The features that will not be tested include:
There is no feature that will not be tested
Testing Pass / Fail Criteria
Define the pass / fail criteria for each of the tests defined in this test plan.
Modules
The following criteria make the modules to pass testing:
Each module does one thing
Each module is written with less and the best code in terms of memory performance
The following criteria make the modules to fail testing:
Each module performs several actions
Each module has poor algorithm in terms of memory management
Integration of the modules
The following criteria make the modules to pass testing:
The modules integrate with each other smoothly using Object Oriented Methodology (Inheritance, Polymorphism, Abstraction, and Encapsulation).
The following criteria make the modules to fail testing:
The modules do not integrate with each other
Database testing
The following criteria make the database to pass testing:
Query optimization
High performance
Scalability
Security e.g. encryption etc.
The following criteria make the database to fail testing:
Lack of security
Poor performance
Takes time to load queries
Integration of the system with database
The following criteria make the integration of the system with database to pass testing:
Someone can create, read, update, and delete data using the software application
The following criteria make the integration of the system with database to fail testing:
A person cannot create, read, update, and delete data using the software application
Integration with other systems
The following criteria make the integration with other systems to pass:
The software can work smoothly with other applications without problems
The following criteria make the integration with other systems to fail:
The application conflicts with other software
GUI testing
The following criteria make GUI testing to pass testing:
The GUI is simple to use
The GUI can be used on various devices i.e. it is responsive
The GUI colors blends well
The following criteria make GUI to fail testing:
The GUI colors does not blend well
The GUI does not look good
The GUI is not responsive
Functional testing
The following criteria make the functional testing to pass testing:
Every unit does what is expected of them
The entire software functions as expected
The following criteria make the functional testing to fail testing:
The software does not operate as expected
Security testing
The following criteria make security testing to pass testing:
The software is signed
The software sanitizes data received from users
The software allows multi-factor authentication of users
The software allows encryption of sensitive data such as passwords
The following criteria make the security testing to fail testing:
The software is not signed
The software does not sanitize data from users thus it can allow malicious code
User acceptance testing
The following criteria make the user acceptance testing to pass testing:
Users love the software and they find it easy to use
The following criteria make the user acceptance testing to fail testing:
The software is difficult to use
Performance testing
The following criteria make the performance testing to pass testing:
The software does not take time to load
The software does not use a lot of memory while running
The following criteria make the performance testing to fail testing:
The software uses a lot of memory to operate making it hard to run other programs
Testing Approach
Describe the testing processes, testing types, and testing methods which will be used in this testing project. Discuss the testing strategy and how this testing strategy will be applied to test this application.
Testing process
The testing process that we will use is:
Planning and control
Under project planning and control we will come up with the approach that we will use to test and also the test objectives
Analysis and design
Under analysis and design, we will come up with the test conditions and also design the test. We will also design the test environment
Implementation and execution
Under implementation and execution, we will execute our specified tests
Evaluating exit criteria and reporting
Under the evaluation of exit criteria, plan to end test when the bugs have decreased to a certain level
Test closure
We will perform test closure when we have achieved our testing goals.
Testing types
We will test our application for both functional and non-functional testing. Under the functional we will perform the following testing:
Unit testing – we will test every unit of the program to ensure that it is working correctly
Integration testing – we will test the parts of the application to ensure that they are working correctly
Interface testing – we will test the interface to see whether it is working as intended
System testing – we will test the entire system to ensure that is at per with the quality standards
Regression testing – since we are making improvements to our previous sales software application, we will ensure that the improvement does not bring bugs
User acceptance testing – we will test to see whether the users accept the new software
Under the non-functional testing we will perform the following testing:
Performance testing – we will test to see whether performance issues arise. We will concentrate on load testing, stress testing, and scalability testing.
Reliability testing – we will test whether the application is reliable or not
Security testing – we will test the security of the application and ensure that it cannot be compromised
Testing methods
The testing methods that we will use include:
Black-box testing
This is where we will test the application without knowing the inner workings of the application
White-box testing
This is where we will test the internal working of the application and also the structure of the code
Testing Cases
Define 12 to 15 test cases for your project.
Analyze system behavior when invalid username and password is entered
Analyze system behavior when valid username and invalid password is entered
Analyze system behavior when invalid username and valid password is entered
Analyze system behavior when a customer requests more money than the one in the account
Analyze system behavior when a customer exceeds that maximum money dispensed using a credit card
Analyze system behavior when a customer performs a transaction online
Analyze the behavior of the system when the “Keep me signed in” checkbox is ticked
Look whether the “Forgot password” button is working as expected when clicked
Look whether menus are working correctly when clicked
Analyze the system behavior when valid username and password is entered
Analyze the system behavior when the username is not of required length
Analyze the system behavior when the password does not contain the required characters (letters, numbers and special characters)
Testing Materials (Hardware/Software Requirements)
Identify the resources that are needed for testing in this project. Include the physical facilities, hardware, software, tools, and any other resources this project will use during testing.
Testing server
Computer, mouse, keyboard
jUnit software for testing Java code
Testing Schedule
| Testing Activity | Duration | Resource | Comments |
| Test Plan Creation | 5 days | Test Manager | Test manager creates a plan on how the test will be performed and the objective of the test |
| Test Specification Creation | 10 days | Test Leads | Test scenario and cases are created |
| Test Specification Team Review | 5 days | Project Team | A team review the laid down test scenario and test cases and the entire purpose of the test |
| Component Testing | 20 days | Component Testers | Each component of the software is tested individually |
| Integration Testing | 20 days | Component and System Testers | Parts of components that work together are tested to see whether they work smoothly |
| System Testing | 15 days | System Testers | The entire system is tested |
| Performance Testing | 5 days | System Testers | The performance of the application is tested e.g. does it use a lot of memory? |
| Use Case Validation | 10 days | System Testers | The test cases we had created are tested e.g. is the password more than eight characters? |
| Alpha Testing | 5 days | Product Managers / Analysts | The software is tested before it is released to users |
| Beta Testing / Pilot Program | 20 days | Pilot Program End-Users | The software is tested by real users of the system |
Risks and Contingencies Matrix
| Risk | Probability | Risk Type | Owner | Contingencies / Mitigation Approach |
| Do not have enough skilled workers to test components as they are ready for testing. | 25% | Project Resources | Testing Manager | Testing schedule will be adjusted based upon available resources. |
| Testing team member turnover | 10% | Project Resources | Testing Manager | Adjust testing schedules. Make sure testing team members are cross-trained on testing techniques in case a team member leaves the organization. |
| Do not have enough time to test components | 10% | Project Resources | Testing Manager | The time will be increased to ensure proper testing. |
Network Diagram