Security Technical Implementation Guides (STIGs) are developed by the Defense Information Systems Agency (DISA) in conjunction with the National Security Agency (NSA) and the National Institute of Sta
Security Technical Implementation Guide (STIG) Lab
Class: CYB.6010
Name:
Date:
Security Technical Implementation Guides (STIGs) are developed by the Defense Information Systems Agency (DISA) in conjunction with the National Security Agency (NSA) and the National Institute of Standards and Technology (NIST). STIGs are used to harden information technology resources such as routers, databases, networks, software development, and other related technologies. STIGs are delivered in SCAP-compliant XML formats for use by SCAP-compliant tools such as Nessus. STIGs are able to be manually examined by using the STIG Viewer. Being able to manually step through a STIG is especially important for uniquely sensitive systems that do not respond well to the use of automated tools.
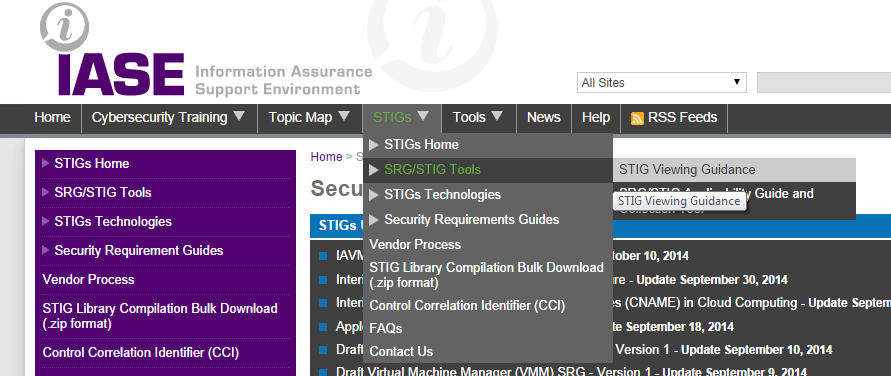
Let’s visit the Information Assurance Support Environment (IASE). Go to: http://iase.disa.mil/stigs/Pages/index.aspx
Click on “STIG Viewing Guidance”.
![Security Technical Implementation Guides (STIGs) are developed by the Defense Information Systems Agency (DISA) in conjunction with the National Security Agency (NSA) and the National Institute of Sta 1]()
Click on “STIG Viewer Version 2.6.1.” and download and follow the instructions to run.
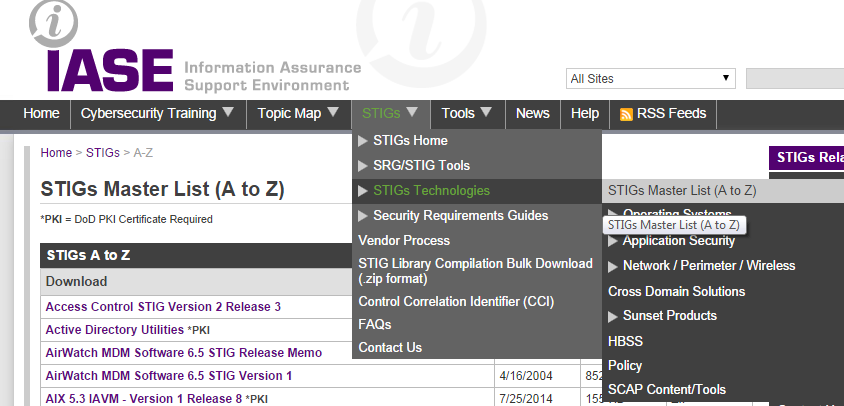
Return to the IASE website and click on “STIGs Master List (A to Z)”. This is a list of all of the STIGs available. Notice there are STIGs for all technologies.
![Security Technical Implementation Guides (STIGs) are developed by the Defense Information Systems Agency (DISA) in conjunction with the National Security Agency (NSA) and the National Institute of Sta 2]()
Click on “Apache 2.2 STIG-UNIX - Version 1, Release 9”.
Open the folder “u_apache_2.2_unix_v1r9_stigs.zip” and then open the folder “U_APACHE_2.2_SERVER_UNIX_V1R9_MANUAL_STIG.zip”
Copy the file “U_APACHE_2.2_SERVER_UNIX_V1R9_manual-xccdf” to your desktop.
Open the STIG Viewer. Please provide the STIG Viewer screenshot.
Go to “File-Import STIG” and import the file you just saved to your desktop.
Notice how you are able to step through and read each configuration. You are able to make notes. Please provide the STIG Viewer screenshot.
Look for STIG ID “WG400 A22 – WG400”.
What is the Rule Title?
Look for STIG ID “WG250 A22 – WG250”.
What is the Rule Title?
Look for STIG ID “WG237 A22 – WG237”.
What is the Rule Title?
What controls for NIST 800-53 do Questions 1, 12, and 13 above meet?
As you can see, performing these checks manually is possible. Using SCAP-compliant automated tools such as Nessus is much easier but if it’s not applicable you may perform these checks and configurations on your own.