check the attach files
SportX company is specialized on selling sports products. The company’s main sales are through their e-commerce website, where customers can issue orders and pay online. SportX company can receive orders through the following lines of sales
Online e-commerce website
Phone calls
Email orders
Then the sales team are responsible on checking those emails and orders, prepare them and the deliver them to customer.
Technical Specification.
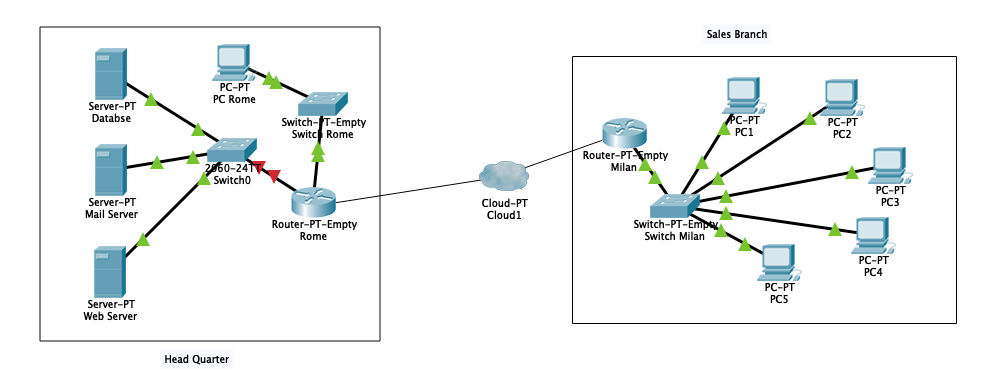
Currently SportX have two branches – one headquarter and one site branches
HQ contains the following –
Email server
Web Server that hosts the e-commerce site.
Databases Server that include the following databases
-
Employee Database
Customer Database
Product Database
Orders Database
Figure 1 shows the entire topology
SportX’s business got an exponential growth from the beginning of 2018. This steady growth also brought challenges for SportX They have to secure the sensitive information of their employee, customer and the most important assets are the orders Database. Moreover, their employees receive many emails and they have to filter the orders emails from other emails.
SportX had no dedicated security team and therefore till now no security policy is in place. Recently, the governing body of SportX forms a security team and makes following two goals that they would like to achieve in six months –
Assessing the current risk of the entire organization
Treat the Risk as much as possible
In achieving the above two goals, today you will do the followings –
Find at least five assets
Find at least two threats against each asset
Idenitfiy vulnerabilities for the assets
Calculate Risk
Provide treatment strategy for each risk
Make the HQ’s network secure by design
Finally, provide plausible protection mechanism
**Please follow the answer guideline
Question 1 (5 points)
Saved
List five most valuable assets of SportX
Question 2 (10 points)
Create a weighted factor analysis worksheet (WFAW). In WFAW, use at least four criteria.
Question 3 (10 points)
Identify and list two threats for each asset.
Question 4 (10 points)
Identify and list the vulnerability of each asset. (One vulnerability against each asset)
Question 5 (15 points)
At the end of the risk identification process, you should have i) a prioritized list of assets and ii) a prioritized list of threats facing those assets and iii) Vulnerabilities of assets. At this point, create Threats-Vulnerabilities-Assets (TVA) worksheet.
Question 6 (5 points)
Each TVA triplet represents risk. Choose any five triplets and identify the impact and likelihood of each risk.
Question 7 (15 points)
Calculate the risk rating of each of the five triplets out of 25. Consider that your assumptions and data are 95% accurate
Question 8 (15 points)
For each of the five identified risk, state what basic strategy you will take. Justify for each decision.
Question 9 (15 points)
Advise all possible protection mechanism and corresponding place of application.



