The paper should contain subheadings: 1.) Literature Review on Gamification for security training. 2.) Literature Review on information Security Compliance. 3.) Literature review on flow theory ( http
Running head: GAMIFICATION FOR SECURITY TRAINING 1
Gamification for Security Training
Problem Statement
The number of cyber-attacks has been increasing rapidly in organizations and these attacks can bring down the reputation of organizations and can cause a loss of millions of dollars for the organizations. Most of the vulnerabilities, attacks, risks, and viruses are the result of a lack of security awareness of employees and users (Seaborn & Fels, 2015).
These risks, vulnerabilities, and attacks can be reduced by improving the knowledge and skills of employees in strengthening the IT infrastructure of the companies. For this purpose, organizations can arrange several types of workshops and training sessions related to cyber-security awareness. Many employees do not show interest and feel boredom in attending those workshops and training sessions. Gamification is considered a practice that can help in boosting the interest and engagement level of employees during security awareness training.
Gamification will have a positive impact on the security training offered to employees by increasing their interest and engagement level. The main problem which is going to be addressed in this research is the understanding of the impact of gamification on the training session offered to employees for improving the security of IT infrastructure.
The present research study is considered highly useful for finding the impact of gamification on the training sessions offered to employees for improving the security of IT infrastructure. This study would enable organizations to understand the significance of gamification, the possible methods that can be utilized for taking advantage of gamification, and why it is one of the best approaches for increasing the engagement level and involvement of employees in training sessions.
Many employees feel difficulty and face a problem of lack of interest and enthusiasm while attending the workshops and training sessions arranged by their employers and managers (Alotaibi, Furnell, Stengel, & Papadaki, 2016). Hence the use of gamification can be a highly effective technique available for organizations to increase the interest and engagement level of employees in the offered workshops and training sessions (Baxter, Kip, & Wood, 2016).
Model Diagram
Flow Theory
Gamification for Security Training
User Security Compliance
Gamification is the method in which the knowledge and experience gained from gaming theory and flow theory have utilized in a non-gaming context. The concept of gamification was implemented for the first time during the Cold War to improve productivity (Alotaibi, Furnell, Stengel, & Papadaki, 2016). Coonradt in 1984 was the early researcher who applied gamification in the business context to motivate employees through the usage of clear goals, frequent feedback provision, gaming features, and personal choice (Baxter, Kip, & Wood, 2016).
Gamification highly helps companies increase their employees' engagement level by utilizing several elements of game designing (Kanat, Siloju, Raghu, & Vinze, 2013). According to some previously conducted research studies, it has suggested that the use of goals, storytelling, rewards, and appreciation are the main aspects of gamification for increasing the curiosity, interest, engagement level and experiences of challenges of users to boost the engagement level and interest of participants in the offered training sessions and workshops (Seaborn & Fels, 2015).
The use of the gamification technique is one of the most preferred training methodologies which helps the companies to increase innovation, productivity, knowledge, skills, experiences, and learning procedures of their employees and participants (Alomari, Al-Samarraie, & Yousef, 2019). This technique is mainly based on the use of innovative thoughts and gaming techniques in a non-entertainment manner, such as improving education and work skills.
There are vast numbers of benefits offered by gamification to its users like it enables employees to increase their productivity, provides motivation for improving their engagement and involvement, encourages employees to become more creative for solving the problems and innovatively addressing them, provides strength to the communication procedures (Pattabiraman, Srinivasan, Swaminathan, & Gupta, 2018).
The use of gamification highly helps employers and managers increase employee engagement by introducing several types of innovative dynamics (Mathoosoothenen, Sundaram, Palanichamy, & Brohi, 2017). It has assumed that the companies who utilize the technique of gamification in the training sessions offered to their employees can get more successful in improving the particular required skills of their employees through the increased interest and involvement of employees in the provided training sessions and workshops (Erenli, 2013). However, it is also considered a highly useful approach for transmitting a productive and positive corporate image (Alomari, Al-Samarraie, & Yousef, 2019).
For using gamification more effectively, all the things should be kept simple, engaging, and entertaining to increase the interest and engagement level of employees. The success of gamification relies mainly on employees' increased involvement, usage of effective gaming techniques, and methods and motivation (Alotaibi, Furnell, Stengel, & Papadaki, 2016). The rewards offered are not considered only pure awards but provide means for inspiring employees to achieve their potential. There are vast numbers of organizations that have to utilize gamification techniques like Google, Starbucks, and Dominos, etc.
When companies use gamification, they work to make the existing tasks more innovative and fun, like the use of video games. The advancement in information technology has highly contributed to increasing cybercrimes and terrorism that can put strong negative impact not only on the reputation of the company but also on the data and information stored in the servers of the company of their employees, customers, and the organization itself (Baxter, Kip, & Wood, 2016). The increased numbers of attacks, threats, risks, and vulnerabilities demand the IT companies become more innovative, productive, and reliable (Gonzalez, Llamas, & Ordaz, 2017).
For this purpose, companies have needed to provide training sessions and workshops to improve the skills and knowledge of their employees. So, to identify and tackle the various attacks, threats, risks, and vulnerabilities, employees should know about IT security so that they can protect their privacy and data from intruders (Erenli, 2013). Employees should also be able to think from the perspective of intruders and act accordingly.
To identify and address the cyberattacks effectively, quickly, and without any significant loss in terms of finance, customers, and reputation, the employees should have updated knowledge as advancements in technology are taking place at a fast rate (Seaborn & Fels, 2015). Several types of cybercrimes can be occurred and can be proved highly harmful. In 2018, the UK, 79% of companies were posed with the threat of cyberattacks and had to face the consequences of problems that occurred (Alomari, Al-Samarraie, & Yousef, 2019).
Most people, including the employees of any organization, do not show interest in attending workshops related to any topic as the workshops play a significant role in enhancing the knowledge of its attendees to improve their existing experience and skills about the security of IT infrastructure (Luh, Temper, Tjoa, Schrittwieser, & Janicke, 2020). However, there is a significant problem faced by a lack of interest and involvement in the offered training and workshops, which can be solved using gamification techniques (Hart, Margheri, Paci, & Sassone, 2020).
Besides, the usage of gamification for increasing the involvement and engagement level of employees has considered to be very cost-friendly as it can provide a considerable amount of benefits to its users and can save them from major problems like in case of having lack of involvement and engagement level of employees in the offered sessions, all the resources which were utilized by the companies like cost, time, place, etc. would get wasted and of no use (Seaborn & Fels, 2015).
Gamification works on the desire of human beings to get the win, successful, and achieve something. It allows employers to offer several types of rewards like badges, points, leader boards, and the ability to do trading to get a particular kind of prize for deriving high quality of behavior from employees to get engaged in the training sessions (Thornton & Francia, 2014). However, it is also rooted in science, as wining always creates dopamine in human beings' minds. They want to get reached to the next level and be placed on the top of the leader board by doing whatever they can to feel good and have a feeling of pride (Alotaibi, Furnell, Stengel, & Papadaki, 2016).
Besides, there is also the considerable significance of the rules which are needed to follow for staying in line and to get guided in the decision making. The companies who get successful in implementing and establishing the right rules for the Information Technology Security awareness training sessions and programs can have more opportunities and chances of extending their programs for having long term benefits (Gonzalez, Llamas, & Ordaz, 2017). All the specified rules, regulations, objectives and goals of the training are needed to be clear and straightforward for getting modified and adjusted according to the changing circumstances and situations (Adams & Makramalla, 2015).
Organizations should not move towards the use of gamification because everyone is using it, and it sounds to be very trending and good. It should be implemented when needed and with a particular purpose (Seaborn & Fels, 2015). All the programs which contain gamification should have some unique value, and all the participants should be felt to be very special and interested in learning about cybersecurity for securing the IT departments of the companies by having a feeling of winning something (Alomari, Al-Samarraie, & Yousef, 2019).
All the contents of gamification in the training sessions are needed to be incorporated in a very transparent manner for obtaining a high level of benefits as it can be proved to be very useful and practical for improving the quality of training sessions and achieving a high level of results (Alotaibi, Furnell, Stengel, & Papadaki, 2016). The success of the training based on gamification relies on the program's accomplishment without being noticed of using gamification (Gonzalez, Llamas, & Ordaz, 2017).
Besides, it has also noticed that the things which work well for one organization are not compulsory and would be sufficient for the other companies (Seaborn & Fels, 2015). Each company seems to have its particular unique organizational culture and training programs designing methods because of having unique traits and knowledge (Alomari, Al-Samarraie, & Yousef, 2019). In each training session, human factors are considered to be the most weakest element for IT security as they can make mistakes and they are also the ones who can make extra ordinary efforts to secure the system to a high extent from vulnerabilities, risks, and attacks (Chen, 2015).
There is one thing which is needed to be same in all the companies who have been working on the usage of gamification in the training that it should be possible for the trainer to turn on or off the gamification features, to do selection between the point scales that would be used for the variety of right answers and wrong options and to make a decision about the go backing of participants for retaking the program for earning some extra or better points and score (Armstrong & Landers, 2017).
There is a vast significance of the theory of flow in the explanation of gamification and its contribution to improving learning procedures. It occurs because the main focus of game designing is on maintaining a balance among the learners' skills and the challenges offered to the participants (Seaborn & Fels, 2015). Hence, playing video games can be the most natural and most effective method for reaching the state of flow. The following figure indicates the flow of theory more effectively (Ruiz-Alba, L., Soares, Rodríguez-Molina, & Banoun., 2019).
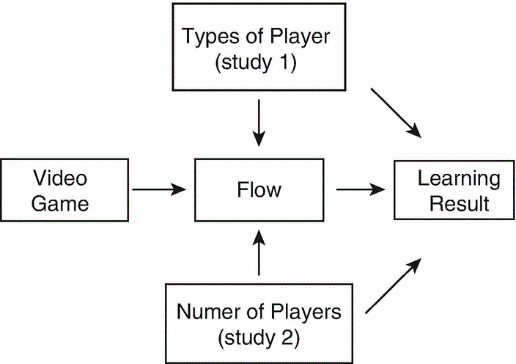
There is a considerable contribution to compliance theory in the successful implementation of gamification. It allows the companies to do structuring of their games by integrating several types of innovative, classic, and useful ideas to get more productive results (Seaborn & Fels, 2015). The compliance theory recommends that the companies be categorized into subforms by the type of power they use for direction (Buckley & Doyle, 2017). When organizations ensure compliance theory, it helps the organizations to do prevention of problems through direct detection of violations of rules and regulations (Wolfenden, 2019). It is considered an on-going procedure followed by the companies while working on the implementation of gamification.
References
Adams, M., & Makramalla, M. (2015). Cybersecurity skills training: an attacker-centric gamified approach. Technology Innovation Management Review.
Alomari, I., Al-Samarraie, H., & Yousef, R. (2019). The role of gamification techniques in promoting student learning: A review and synthesis. Journal of Information Technology Education: Research, 395-417.
Alotaibi, F., Furnell, S., Stengel, I., & Papadaki, M. (2016). A Review of Using Gaming Technology for Cyber-Security Awareness. International Journal for Information Security Research, 660-666.
Armstrong, M. B., & Landers, R. N. (2017). An evaluation of gamified training: Using narrative to improve reactions and learning. Simulation & Gaming, 513-538.
Baxter, R. J., Kip, H. J., & Wood, D. A. (2016). Applying Basic Gamification Techniques to IT Compliance Training: Evidence from the Lab and Field. Journal of Information Systems, 119-133.
Chen, E. T. (2015). Gamification as a resourceful tool to improve work performance. In Gamification in education and business, 473-488.
Erenli. (2013). The impact of gamification-recommending education scenario. International Journal of Emerging Technologies in Learning.
Gonzalez, H., Llamas, R., & Ordaz, F. (2017). Cybersecurity Teaching through Gamification: Aligning Training Resources to our Syllabus. Research in Computing Science, 35-43.
Hart, S., Margheri, A., Paci, F., & Sassone, V. (2020). Riskio: A Serious Game for Cyber Security Awareness and Education. Computers & Security.
Kanat, I. E., Siloju, S., Raghu, T. S., & Vinze, A. S. (2013). Gamification of emergency response training: A public health example. IEEE, (pp. 134-136).
Luh, R., Temper, M., Tjoa, S., Schrittwieser, S., & Janicke, H. (2020). PenQuest: a gamified attacker/defender meta-model for cybersecurity assessment and education. Journal of Computer Virology and Hacking Techniques, 19-61.
Mathoosoothenen, V. N., Sundaram, J. S., Palanichamy, R. A., & Brohi, S. N. (2017). An Integrated Real-Time Simulated Ethical Hacking Toolkit with Interactive Gamification Capabilities and Cyber Security Educational Platform. In Proceedings of the 2017 International Conference on Computer Science, (pp. 199-202).
Pattabiraman, A., Srinivasan, S., Swaminathan, K., & Gupta, M. (2018). Fortifying corporate human wall: A Literature review of security awareness and training. In Information Technology Risk Management and Compliance in Modern Organizations, 142-175.
Redhead, A., & Saunders, J. (2019). Gamification and Simulation. In Serious Games for Enhancing Law Enforcement Agencies, 83-98.
Ruiz-Alba, L., J., Soares, A., Rodríguez-Molina, M. A., & Banoun., A. (2019). Gamification and entrepreneurial intentions. Journal of Small Business and Enterprise Development.
Seaborn, K., & Fels, D. I. (2015). Gamification in theory and action. International Journal for Information Security Research.
Seaborn, K., & Fels, D. I. (2015). Gamification in theory and action: A survey. International Journal of human-computer studies, 14-31.
Thornton, D., & Francia, G. (2014). Gamification of information systems and security training: Issues and case studies. Information Security Education Journal, 15-24.
Wolfenden, B. (2019). Gamification as a winning cybersecurity strategy. Computer Fraud & Security, 9-12.



