Possible to get it done within 2 day?
FEEDBACK FROM MY LECTURER FOR MY PREVIOUS WORK
IG (ICA)
In general, the risk assessment written unfortunately missed the point with regards to advising Fresh Air on how they can improve their IT services and data security during a IT disaster.
Specifically:
| Part | Feedback and areas to improve | |
| Item 1 Risk Assessment |
| |
| Item 2 Controls | The assessment for this section did not address the question. The question required a summary of ethical, social, legal, regulatory compliance issues in relation to the case study.
Your assessment only provided definitions for legal terms but no attempt to relate to the case study. You should relate to the case study instead of providing a list of definitions for the different types of legal terms.
Totally missed the point on this question. | |
| Item 3 Disaster Recovery Poster | Due to Item 1 and Item 2 that missed the point, this has affected Item 3. The poster or diagram spells out the steps to prepare a Disaster Recovery Plan.
The question for Item 3 requires a poster for the steps or process to be taken when an IT disaster occur.
The poster should have included steps for IT staff to take when an IT disaster occur to Fresh Air. Additionally a swimlane diagram would have help to determine the roles and responsibilities. | |
| Item 4 Reflection | A very brief reflection. A total of 53 words compared to the guide of 600 words. Less than 10% of guide.
Although strengths and weaknesses were mentioned, it has a very weak and vague link to the case study.
The area of improvement is to provide a deeper reflection of this case study and to layout the actions from the learnings mentioned in the strength and weakness paragraphs. | |
| Professional Presentation | A poor attempt at the case study. Lacks commitment. The report layout is not properly done. Although it has a table of content, the rest of the report layout is not in order. |
FEEDBACK FORM
| Part | Criteria | Weightage | Marks | Comments |
| Item 1 Risk Assessment | 70% + Excellent work to an extremely high professional standard which covers all conceivable risks. Descriptions are highly detailed and include excellent appropriate information. May exceed expectations at this level. 60-69% Very good work to a professional standard which covers a wide range of risks. Descriptions are detailed and include very good appropriate information. 50-59% Good work to a reasonable professional standard which covers a range of conceivable risks. Descriptions are reasonable and include appropriate information. 40-49% An attempt has been made to identify appropriate risks but there are some missing and/or they are not appropriate. Descriptions are included but are not always appropriate or lack detail. <40% A poor attempt which does not meet the module learning outcomes. It may have missing information or has missed the point. | 25% | ||
| Item 2 Controls | 70% + Excellent summary to an extremely high professional standard. Includes excellent detail. It could be implemented in industry. May exceed expectations at this level. 60-69% Very good summary to a professional standard. Includes good detail. Could be implemented in industry with some minor adjustments. 50-59% Good summary to a reasonable professional standard. Includes reasonable detail. It could be implemented in industry with more work. 40-49% An attempt has been made to write a summary. Details have been included but are not clear or have no meaning in this context. The document is somewhat vague and needs quite a lot more work. <40% A poor attempt which does not meet the module learning outcomes. It may have missing information or has missed the point entirely. | 35% | ||
| Item 3 Disaster Recovery Poster | 70% + An excellent informative poster which includes an excellent process flow diagram with references. The steps are logical, realistic and accurate. 60-69% A very good poster which includes a very good process flow diagram and references. The steps are accurate and logical. 50-59% A good poster with a reasonable process flow diagram (may have missing points) and references. There may be some minor errors present but it’s mostly accurate and logical. 40-49% A poster has been submitted but it lacks detail and the process flow diagram may be too simple or incorrect, or missing. Referencing is present but could be improved. Steps could be more accurate and logical. <40% A poor attempt which does not meet the module learning outcomes. It may have missing information or has missed the point entirely. | 20% | ||
| Item 4 Reflection | 70% + An excellent reflection which identifies strengths and areas for improvement with detailed reasoning. Professional layout and could be published. It clearly links the current module learning to prior learning and experiences and considers future learning and/or career choices in detail. Incorporates references and/or best practice examples. 60-69% A very good reflection which identifies a number of strengths and areas for improvement with some reasoning. Layout is good enough to publish with minor amendments. It links learning experiences well and includes references. 50-59% A good reflection with a selection of points raised. It could be more reflective and make use of references. There is some linking of learning experiences. There may be some minor errors present. Reasonable layout but needs more work. 40-49% A reflection has been written but it lacks detail and does not provide justifications. No linking of learning experiences included. Layout could be improved, and it needs more work. <40% A poor attempt which does not meet the module learning outcomes. It may have missing information or has missed the point entirely. | 10% | ||
| Professional Presentation | 70% + Presentation is excellent all round and makes use of industry-appropriate language. All items could be implemented in industry. 60-69% Presentation is very good and could be implemented in industry with minor amendments. 50-59% Presentation is acceptable but may lack some of the requirements listed in the specification. 40-49% Presentation could be improved based on the requirements listed in the specification. <40% A poor attempt which does not meet the module learning outcomes. It may have missing information or has missed the point entirely. | 10% |
Marks:
| General Comments: | |
| Assessor’s Signature: | Date: |
| Name:
| |
INSTRUCTIONS TO CANDIDATE:
| General Instructions |
| Use the following format for the preparation of the assignment submission.
|
| WARNING |
|
| IN-COURSE ASSESSMENT (ICA) SPECIFICATION |
| Module Title: Information Governance | Module Leader: V Rushin-Chape |
| Module Code: CIS3005 | |
| Assignment Title: Information Governance Portfolio | Deadline Date: To be confirmed by MDIS |
| Deadline Time: 4:00pm | |
| Submission Method: Online (Blackboard) Middlesbrough Tower |
| Online Submission Notes:
|
| Central Assignments Office (Middlesbrough Tower M2.08) Notes:
|
| FULL DETAILS OF THE ASSIGNMENT ARE ATTACHED |
Task 1 – Risk Assessment 9
Task 2 – Summary of Ethical, Social, Legal and Regulatory Compliance Issues 13
Task 3 – Disaster Recovery Poster 18
Task 4 – Reflection 19
References 21
Appendix 22
Task 1 – Risk AssessmentOne of the risks that can be identified from the case study is the vulnerability of the sales-based system of Fresh Air to unauthorised access and manipulation. This system holds quite an important role to the company as it keeps track of billings, invoices, and payments made by customers. Unauthorised or malicious manipulation of these sensitive data can lead to customer complaints and may even have legal consequences. The risk stems from the system currently having no log-in requirement. This means that anyone, regardless of who they are or whether are they authorised, can access the system and make modifications to the data inside. Since there is no need for logging in, it also means that whoever uses the system do not need to provide their ID beforehand; thus, making it nearly impossible to keep track of who accesses the system at different times. This would become an obstacle to tracing the users should an error or issue arise. The likelihood of this happening is quite high and has a score of 4 out of 5 on the likelihood scale. The severity of the impact is also quite high and has a score of 4 out of 5 on the severity scale. This results in a risk score of 16 out of 25 on the Risk Scoring Matrix (attached in appendix). A clear solution to the problem is to implement a log-in requirement. Access to the system should be restricted to the key personnel, meaning that other employees of the company that is not involved will not be able to use it. By requiring employees to log in and provide their ID, this would make it easier and faster to track down the culprit in the event of unwanted modifications of the data in the system. By restricting access, the key personnel using the system can be held accountable if anything happens. This log-in requirement not only potentially prevents unauthorised access, but it also helps speed up the process of catching the culprit as well as restoration of the original data if it is unable to do so.
Furthermore, the fact that the system is installed on just 2 computers can be a problem. The company faces the risk of having the flow of their daily sales operation being interrupted due to sudden hardware failure on both computers. Computer hardware can fail due to many reasons such as overheating, power surge caused by lightning, accidental water damage etc. If 1 computer fails, then only 1 is left for the employees to use, which would interrupt any transactions that are still being processed and slow down the whole operation. Some important data may be lost in the process as well. If both computers were to fail at the same time, then the sales operation will be halted completely. The employees will need to wait for them to be fixed before they can resume their business. Not to mention, it would take some time to recover the lost data and transactions to continue with where the employees left off before the incident. The likelihood of this occurring is quite high and has a score of 4 out of 5 on the likelihood scale. The severity of the impact is at its highest with a score of 5 out of 5. This results in a risk score of 20 out of 25 on the Risk Scoring Matrix. An easy solution to this issue is to install the system on 2 or more extra computers. Even if the company needs only 2 computers with the system installed to operate, having backup computers can help ensure continuity of the sales operation in the event that both computers become unusable. Backups of the system data and transactions must be made on the servers as well. This would allow the employees to resume their work on the backup computers almost immediately after the interruption.
Moreover, the environment of Fresh Air’s main site poses a risk to the flow of its business operation. As the site is exposed to extreme weather such as lightning and wind, the company faces a high risk of being interrupted by sudden power outage. Lightning can cause a power surge which could result in short circuit for the hardware. It may even cause permanent damage to the electrical equipment and devices that are connected to the power source. This would probably cause the business operation to be halted indefinitely. Since the company generates their own electricity through wind turbines that will not operate at wind speeds under 6mph or over 50mph, they will experience sudden power cuts during times where there is extreme wind. Even though they have backup generators to ensure that they can continue with their business while waiting for the power to return, their current transactions and activities will still be interrupted, and some important business data may even be lost in the process. This is similar to the aforementioned situation of the computer hardware failure. The likelihood of this happening is at its highest with a score of 5 out of 5 on the likelihood scale. The severity of the impact is also at its highest with a score of 5 out of 5 on the severity scale. This results in a maximum risk score of 25 out of 25 on the Risk Scoring Matrix. To prevent sudden power cuts, the company can implement a procedure in which employees must fire up the backup generators immediately during extreme wind. This way the employees can prevent a possible interruption and carry on with their business. Once the extreme wind has passed, they can switch off the generators. The company must also remember to continuously make backups of the transactions and data that are currently being processed. In the event of a short circuit or hardware damage, employees can continue where they left off immediately with these backups. Once again, the solution is similar to the one in the computer hardware failure situation.
The location of Fresh Air’s backup servers is also a cause for concern. This is because even though it at a lower level site that is sheltered from wind, it faces a higher risk of flooding. Flooding can cause serious water damage to the many of the devices and hardware, perhaps even all of them. While it may not interrupt their daily business operation as they still have the main servers, it will be risky for them to operate without the safety net of backup servers. If those main servers were to fail at the same time, then all their important business data will be permanently lost. This would be devastating to the company as these data are essentially the lifeblood of the business. Not to mention, it will incur a high cost for them to replace all the equipment as well. They would need to find another location to set up the backup server again which is another cost to consider. The likelihood of this occurring is very high and has a score of 4 out of 5 on the likelihood scale. The severity of the impact is at its highest with a score of 5 out of 5 on the severity scale. This results in a risk score of 20 out of 25 on the Risk Scoring Matrix. Unless the company is willing to consider a new and safer location for the backup servers, the next best thing to do is to place these servers at a higher level in the building. This means that the ground and basement level should be void of any devices or hardware. The building should also be checked for spots for possible water leakage and the surrounding environment of the server room should be made waterproof. In the event of a flood, the servers would still be working and safe from damage.
Last but certainly not the least, Fresh Air faces a risk of having incompetent and inexperienced employees who may fail to learn and carry out the practises of information security and compliance. This is due to newly hired staff having a short period of training and probation, which is only 4 weeks. No matter how comprehensive the training is, 4 weeks is very little time for new employees to learn and follow best practises effectively. Learning new information is one thing, being able to apply them in daily routine is another. Research carried out by an Opinion Matters survey has shown that almost a fifth of new recruits fail probation (BrightHR, 2020). If these new recruits are not knowledgeable in information security and compliance after training but are somehow able to slip through cracks and succeed in making through the probation period, it could spell trouble for the company. The integrity and security of the company’s data may be threatened. Sensitive, private and confidential data may be vulnerable to accidental leakage or exposure, unauthorised access, as well as hackers and theft. The likelihood of this happening is quite high with a score of 4 out of 5 on the likelihood scale. The severity of the impact is also quite high and has a score of 4 out of 5 on the severity scale. This results in a risk score of 16 out of 25 on the Risk Scoring Matrix. The obvious solution is to increase the length of the probation period. It is more common for probation periods to last for at least 3 months; some may even last up to 1 whole year (BrightHR, 2020). 3 months’ time would be enough to determine whether an employee truly does understand the importance of information security and compliance and follow the proper company policies and procedure. If incompetent employees are somehow still able get through, it would be wise for the company to restrict the access to those important business data to senior employees who are more careful and experienced. The new employees should be put to the test by going through simulations where their actions and decisions are related to information security. This is to ensure that they can be trusted enough to handle data safely and securely.
Task 2 – Summary of Ethical, Social, Legal and Regulatory Compliance IssuesFirst and foremost, the no log-in requirement of Fresh Air’s sales-based system is a highly concerning regulatory compliance issue regarding access control. Since users do not have to go through any verification process to use the system, it would be easy for malicious individuals to gain access to it. This could become a headache for the company as the system contains private and sensitive data such as the customers’ payment and credit card details. Employees with ill intention can access the system and make unwanted modifications to the data as well as steal them for personal use. As stated in ‘Section 9.4 System and application access control’ of the ‘ISO/IEC 27002 code of practice for information security controls’, access to these important data should be restricted based on the company’s access control policy by using secured log-in procedures, password management, control over user privileges and etc. ‘Section 9.3 User responsibilities’ states that the company must ensure users of the system are aware that it is their responsibility to maintain effective access control through methods such as using complex passwords and keeping them confidential. (Iso27001security.com, 2020) Thus, it is sensible for the company to implement a secured log-in feature for their sales-based system to avoid any unauthorised access and use. Should the company fail to comply with this basic regulatory requirement, they must be prepared to face a host of legal consequences such as getting sued by customers for leaving their data in such an unsafe environment. Authorities may even take actions against them for not protecting the customers’ data privacy.
Besides that, Fresh Air must also take into consideration the legal compliance when it comes to purchasing and licensing of proprietary software for their workshop floor. As most companies use third party software, they must be aware of the rules and regulations pertaining to those products. They need to acknowledge and understand that even though they have paid for the license to use the software, they do not technically own it. ‘Section 14.2 Security in development and support processes’ of the ‘ISO/IEC 27002’ states that buyers of these software packages should not modify them and should follow the secure system engineering principles. (Iso27001security.com, 2020) This means that the company must not modify these software applications in any way, shape or form. If they wish to modify the software, then they can consider using open source software. Hence, it is important for Fresh Air to train the IT Services Manager in following information security practices. They must know the dos and don’ts of using proprietary software as they are the ones directly in charge of purchasing and licensing them. Training should also be extended to all the other employees to ensure that they do not conduct any illegal acts such as making and distributing copies of the software. Otherwise, if this legal requirement is not complied with, the company can get slapped with copyright infringement lawsuit by the software company.
Furthermore, working with or outsourcing to a third parties introduces the potential for a regulatory compliance issue regarding system acquisition, development and maintenance to arise. As can be gathered from the case study, Fresh Air has no qualms about employing services from third party sources. They team up with a third-party provider for its hardware and software provision. The IT Service Manager is also allowed to choose to outsource the implementation of the company’s email solution rather than managing it in-house. While outsourcing the development of a system saves time and effort for the company, they should also take into account the security aspect in terms of the system and information. Third party companies may require access to the company data in order to develop their software or system. As such, the aforementioned ‘Section 14.2’ of the ‘ISO/IEC 27002’ also states that the environment of the development process should be secured and any development that is outsourced should be regulated. The security of these system must be tested by the company to ensure it meets the acceptance criteria. ‘Section 15.1 Information security in supplier relationships’ states that there should be policies, procedures, and awareness in place – which are clearly defined and mutually agreed upon in contracts – to protect the companies’ information that is accessible to IT outsourcers and other external suppliers. (Iso27001security.com, 2020) Therefore, the obvious step for Fresh Air to take when outsourcing to third parties is to always enter into these legally binding contracts. This would ensure that the third parties will not illegally collect or use the company data; they would face legal penalties if they do as they will be violating the terms of the contract. In the event that this legal requirement is not met, the company can be easily taken advantage of by the outsourcers as they cannot be legally held responsible for any violations of information security since there is no contract.
Moreover, the Installation Manager using a work-supplied iPad device to conduct surveys could result in a regulatory compliance issue regarding organization of information security for Fresh Air. It can be assumed that the company will provide employees with electronic devices to carry out their work if it is deemed necessary. Sometimes, employees may not always use company-supplied devices for work alone, they may use these devices for personal purposes as well. For instance, they may use the devices to surf the web, log onto their social media, watch videos, and play games etc. ‘Section 6.1 Internal organization’ of the ‘ISO/IEC 27002’ states that all the roles and responsibilities pertaining to information security should be laid out by companies and allocated to all their employees. ‘Section 6.2 Mobile devices and teleworking’ states that companies should also implement security policies and controls for mobile devices and teleworking. (Iso27001security.com, 2020) As such, it would be wise for Fresh Air to make it mandatory for all company-supplied devices to be left on the work premises after employees return home for the day. The company should also monitor the online activity of the employees. All of these is to ensure that they won’t access insecure or questionable websites while using company devices as doing so can open the door for security threats and attacks. If this regulatory measure is not taken and employees are allowed to make personal use of company devices, the devices may be susceptible to infection with all kinds of malware. This would cause damage to whatever systems or applications that the company have installed on the devices and disrupt the business operation.
The locations and the surrounding environment of Fresh Air’s facilities are a cause for concern too. The company’s main site is exposed to extreme weather events and the site of the backup servers have a high risk of being flooded; both of these situations raise the issue of regulatory compliance when it comes to physical and environmental security. A company’s facilities should be located at safe and secure spots that can prevent the environment from causing damage to their equipment. These equipment enables the company to carry out its business operation; it is only logical to keep them in safe and good condition. This means that locations with volatile environment such as extreme weather and high-risk flooding are not the optimal choice for setting up a company’s facilities. As stated in ‘Section 11.1 Secure areas’ of the ‘ISO/IEC 27002’, the company should look a specialist for guidance regarding protection of the work premises and buildings against fires, floods, earthquakes, bombs etc. ‘Section 11.2 Equipment’ states that the company should ensure that their equipment and supporting utilities like power and air conditioning as well as cabling are secured and well-maintained. (Iso27001security.com, 2020) Thus, Fresh Air should either consider new locations for their facilities or sought advice from experts on how to protect their equipment from lightning, extreme wind, and flood. Once they have made the changes based on the advice, they should then have the expert survey the premises and test the new security measures to test their effectiveness. Should the company not comply with this requirement, they have a risk of exposing their equipment to damage and perhaps even total destruction, in which they would need to halt their business operation indefinitely (if not permanently) to replace the ruined equipment – a very costly thing to do. Not to mention, it is also an issue of ethical compliance as well. These extreme conditions of the facilities can pose a threat to the employees’ safety. Even if the company managed to jump through legal loopholes, they will not be able to justify putting their staff in danger. Putting their lives at risk is sure to violate certain regulations under the Occupational Safety and Health Act 1994.This would result in the company being charged with an offence and be liable to a fine of ten thousand ringgit maximum or to imprisonment for a term of one year maximum or to both. (Dosh.gov.my, 1994)
Lastly, the 4-week probation period which includes training for new recruits could become an issue of regulatory compliance regarding human resource security. 4 weeks is not enough time for new employees to fully absorb the knowledge of information security and effectively apply them in daily routine. As some studies suggested, a minimum of 3 months is a more common period of probation (BrightHR, 2020). The company must ensure that the new recruits understand the importance of information security and are able to follow best practices for it. According to ‘Section 7.1 Prior to employment’ of the ‘ISO/IEC 27002’, companies must consider information security responsibilities when recruiting new employees (both permanent and temporary) and list them in the contracts. ‘Section 7.2 During employment’ states that employees should be made aware of and be motivated to comply with their information security obligations. (Iso27001security.com, 2020) Incidents caused by workers regarding information security will need to be handled through a formal disciplinary process. Hence, it would be beneficial for Fresh Air to implement a longer probation period to train and test the new recruits. The company needs to explain and emphasize the importance of their information security duties to them. Any worker that is unwilling to carry out these duties needs to be formally disciplined. Failure to comply with this requirement would cause the company to be filled with incompetent employees who will ignore best practices and threaten the integrity as well as the information security of the company.
Task 3 – Disaster Recovery Poster
FINISH
START
Task 4 – Reflection
I feel that the content I have provided are enough to meet the basic requirements of this assignment. I have followed the guidelines and instructions properly. Since I have taken a Risk Management module before, I was more comfortable completing the task related to Risk Assessment compared to other tasks. Information Governance and Information Security are topics unfamiliar to me, so some research and reading had to be done in order to gather useful information about them. I feel that the amount of my content is more or less appropriate for each task.
The recommendations that I have given in my answers stem from a combination of my limited knowledge on Information Security and my own common sense. This could be the reason why they might not be completely practical as they should be. I feel that I could have given more detailed and solid input if I am more knowledgeable in this topic. This is an area I definitely need to improve on.
I have used very few references for this assignment. This is because I was not able to find many helpful resources. The ones that I did find helpful all comes from the same place. This is also another area for me to brush up on. All the references are also obtained online as printed material was unavailable. Perhaps books and journals would have more useful information on the topic.
I feel that I have been able to present of the whole report in an orderly and satisfactory manner. As such, I believe this visual presentation skill to be one of my strengths. I have always placed great importance on the formatting and organization of reports. Readers should be comfortable reading my report.
Finally, I think my greatest weakness is time management. I would often procrastinate and put off doing assignments rather than have an early head start on them. However, I still try to complete them on time or be prepared to face the consequence of late submission.
ReferencesBrightHR. 2020. Importance Of Probation Periods | Brighthr. [online] Available at: <https://www.brighthr.com/articles/hiring/probation-periods/the-importance-of-employee-probation-periods/> [Accessed 3 May 2020].
Dosh.gov.my. 1994. OCCUPATIONAL SAFETY AND HEALTH ACT 1994. [online] Available at: <https://www.dosh.gov.my/index.php/legislation/acts-legislation/23-02-occupational-safety-and-health-act-1994-act-514/file> [Accessed 3 May 2020].
Iso27001security.com. 2020. ISO/IEC 27002 Code Of Practice. [online] Available at: <https://www.iso27001security.com/html/27002.html> [Accessed 3 May 2020].
Palmen, N. and Verbist, K., 2015. Figure 1: Impact Analysis To Calculate The Risk Score. A Method To.... [online] ResearchGate. Available at: <https://www.researchgate.net/figure/Impact-analysis-to-calculate-the-risk-score-A-method-to-calculate-the-risks-of-potential_fig1_303685047> [Accessed 3 May 2020].
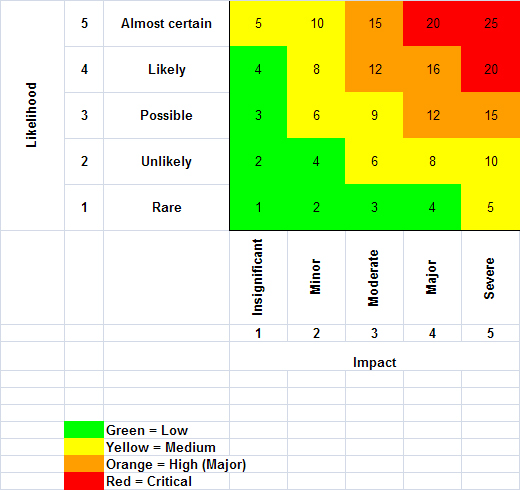
Figure 1 Risk Scoring Matrix
(Palmen and Verbist, 2015)



