Ask any IT manager about the challenges in conveying IT risks in terms of business risks, or about translating business goals into IT goals. It’s a common difficulty, as the worlds of business and IT
Note: This is a paper-based lab. To successfully complete the deliverables for this lab, you will need access to Microsoft® Word or another compatible word processor. For some labs, you may also need access to a graphics line drawing application, such as Visio or PowerPoint.
On your local computer, create a new document.
You will use this document as your Lab Report.
Review the seven domains of a typical IT infrastructure.
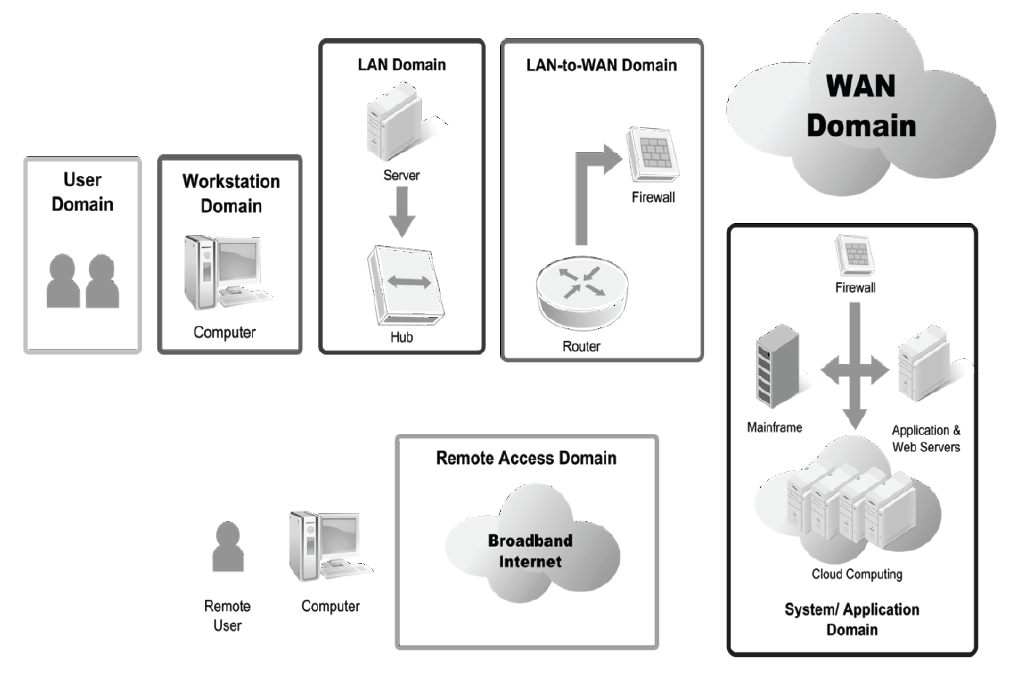
Seven Domains
Seven Domains
In your browser, navigate to https://web.archive.org/web/20181115194831/http://www.isaca.org/Knowledge-Center/cobit/Pages/FAQ.aspx.
Review the information on the COBIT FAQs page.
ISACA—45 Years Serving Auditors and Business:
ISACA is a global organization that defines the roles of information systems governance, security, auditing, and assurance professionals worldwide. ISACA standardizes a level of understanding of these areas through two well-known certifications, the Certified Information Systems Auditor (CISA) and Certified Information Security Manager (CISM). In recent years, ISACA has expanded its certification offerings to include two other certifications around risk and IT governance.
ISACA was previously an acronym expanding to Information Systems Audit and Control Association, but today is known by the name ISACA alone to better serve its wider audience.
Similarly, COBIT was originally an acronym for Control Objectives for Information and related Technology. Now, ISACA refers to the framework as just COBIT, in part because the concept of “control objectives” ends with COBIT version 4.1. COBIT 5 focuses on business-centric concepts and definitions, distinguishes between governance and management, and includes a product family of “enabler guides” and “practice guides.” The recent release of COBIT version 5, released in 2012, is a complete break from expanded the COBIT framework, but COBIT 2019 will add a new Design guide and implementation strategies that include cloud computing.
In your Lab Report file, describe the primary goal of the COBIT v4.1 Framework. Define COBIT.
On the left pane of the COBIT website, click the COBIT 4.1 Controls Collaboration link.
At the top of the page, read the Discuss-Share-Learn introductory text.
Scroll down the page to the COBIT Domains and Control Objectives section.
Click the Text View tab.
In your Lab Report file, list each of the six domains of control objectives and briefly describe them based on the descriptions on the website. Include the following:
Plan and Organize
Acquire and Implement
Monitor and Evaluate
Delivery and Support
Process Controls
Application Controls
On the left pane of the COBIT website, click the COBIT 4.1 Publications and Products link.
From the center of the page, click the complimentary PDF download link to open the Download Registration page.
Note: You can also use Google to search for COBIT 4.1, which should return copies of the COBIT 4.1 PDF in the top results. If you choose this approach, skip ahead to step 16.
On the Download Registration page, use the following information to register for a downloadable copy of the framework.
Use your own name and email and type student in the Job Title box and select your own country.
Click the acknowledgement checkbox and then click the SUBMIT TO ACCESS THE DOWNLOAD button to open the FileDownload page.
Click the DOWNLOAD YOUR FILE button and open the file.
The file may open in a new browser window or may appear in your Downloads folder. Locate the file and open it to continue.
In the file, read the Executive Overview beginning on page 5.
Refer to the page number in the footer of each page of the file.
In the file, read the How to Use This Book section beginning on page 27.
In the file, read the P09 Assess and Manage IT Risks process beginning on page 63.
Note: COBIT 5 is not an evolutionary but a revolutionary change. Naturally, risk management is covered, but it is done in a holistic, end-to-end business approach, rather than in an IT-centered approach.
In your Lab Report file, explain how you use the P09 Control Objectives to organize identified IT risks, threats, and vulnerabilities so you can then manage and remediate the risks, threats, and vulnerabilities in a typical IT infrastructure.
Note: This completes the lab. Close the web browser, if you have not already done so



