Please find doc attached.
Hands-On Steps
Note: This is a paper-based lab. To successfully complete the deliverables for this lab, you will need access to Microsoft® Word or another compatible word processor. For some labs, you may also need access to a graphics line drawing application, such as Visio or PowerPoint.
On your local computer, create a new document.
You will use this document as your Lab Report.
On your local computer, open a new web browser window.
Using your favorite search engine, search for information on the purpose of IT risk assessment.
In your Lab Report file, describe the purpose of IT risk assessment.
Review the following table for the risks, threats, and vulnerabilities found in a health care IT infrastructure servicing patients with life-threatening conditions:
| Risks, Threats, and Vulnerabilities | Primary Domain Impacted | Risk Impact/ Factor |
| Unauthorized access from public Internet |
|
|
| User destroys data in application and deletes all files |
|
|
| Hacker penetrates your IT infrastructure and gains access to your internal network |
|
|
| Intraoffice employee romance gone bad |
|
|
| Fire destroys primary data center |
|
|
| Service provider service level agreement (SLA) is not achieved |
|
|
| Workstation operating system (OS) has a known software vulnerability |
|
|
| Unauthorized access to organization-owned workstations |
|
|
| Loss of production data |
|
|
| Denial of service attack on organization Demilitarized Zone (DMZ) and e-mail server |
|
|
| Remote communications from home office |
|
|
| Local Area Network (LAN) server OS has a known software vulnerability |
|
|
| User downloads and clicks on an unknown e-mail attachment |
|
|
| Workstation browser has a software vulnerability |
|
|
| Mobile employee needs secure browser access to sales-order entry system |
|
|
| Service provider has a major network outage |
|
|
| Weak ingress/egress traffic-filtering degrades performance |
|
|
| User inserts CDs and USB hard drives with personal photos, music, and videos on organization-owned computers |
|
|
| Virtual Private Network (VPN) tunneling between remote computer and ingress/egress router is needed |
|
|
| Wireless Local Area Network (WLAN) access points are needed for LAN connectivity within a warehouse |
|
|
| Need to prevent eavesdropping on WLAN due to customer privacy data access |
|
|
| Denial of service (DoS)/distributed denial of service (DDoS) attack from the Wide Area Network (WAN)/Internet |
|
|
Review the seven domains of a typical IT infrastructure.
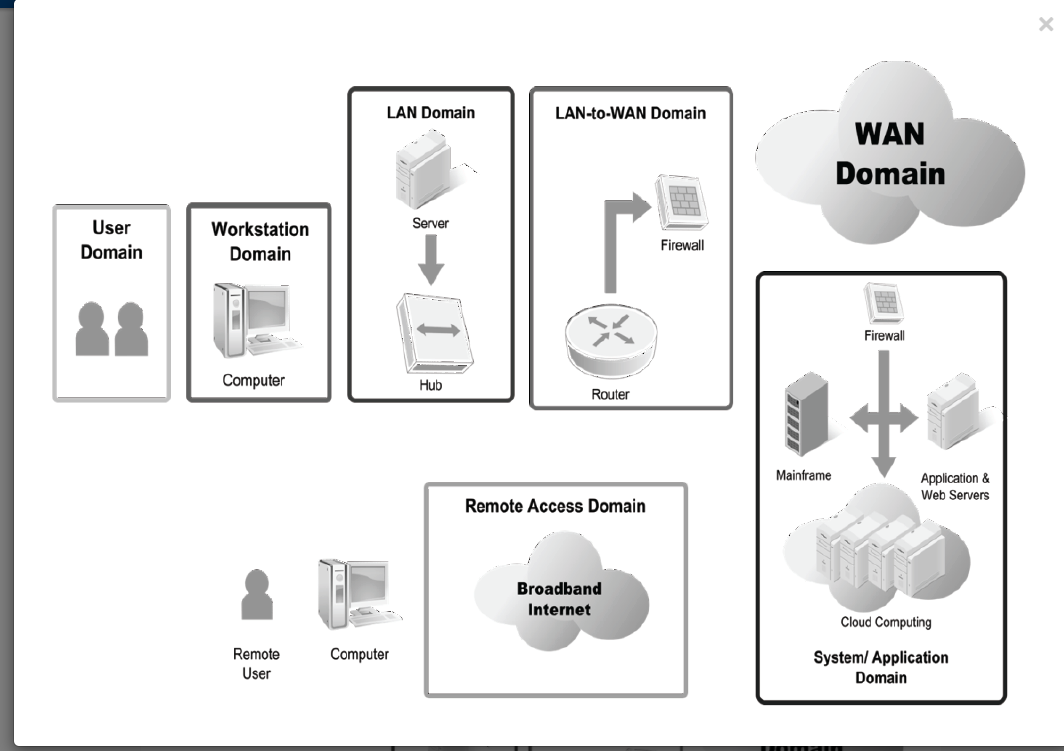
Seven Domains
In your Lab Report file, using the table from step 5, identify in the table’s Primary Domain Impacted column which of the seven domains of a typical IT infrastructure will be most impacted by each risk, threat, or vulnerability listed.
In your Lab Report file, using the table from step 6, perform a qualitative risk assessment by assigning a risk impact/risk factor to each of the identified risks, threats, and vulnerabilities throughout the seven domains of a typical IT infrastructure where the risk, threat, or vulnerability resides. Assign each risk, threat, and vulnerability a priority number in the table’s Risk Impact/Factor column, where:
“1” is Critical: A risk, threat, or vulnerability that impacts compliance (that is, privacy law requirement for securing privacy data and implementing proper security controls, and so on) and places the organization in a position of increased liability.
“2” is Major: A risk, threat, or vulnerability that impacts the confidentiality, integrity, and availability (C-I-A) of an organization’s intellectual property assets and IT infrastructure.
“3” is Minor: A risk, threat, or vulnerability that can impact user or employee productivity or availability of the IT infrastructure.
Note: Keep the following in mind when working on the next step: When suggesting next steps to executive management, consider your recommendations from their point of view. Be prepared to explain costs, both in implementing the controls and then in maintaining the controls.
Remember that costs come in many forms, not least of which is labor. Be sure accountability is thought out in terms of roles and responsibilities. Other potential costs outside the data center include goodwill or reputation, market share, and lost opportunity. Executive management might have these costs topmost in mind.
In your Lab Report file, write a four-paragraph executive summary according to the following outline:
Paragraph #1: Summary of findings (risks, threats, and vulnerabilities found throughout the seven domains of a typical IT infrastructure).
Paragraph #2: Approach and prioritization of critical, major, and minor risk assessment elements.
Paragraph #3: Risk assessment and risk impact summary of the seven domains of a typical IT infrastructure.
Paragraph #4: Recommendations and next steps for executive management.
Note: This completes the lab. Close the web browser, if you have not already done so.



