Write a 1 page summary on the attached file. Thanks.
6.1
Plan Risk Responses
Exam Objectives
3. Domain 3: Risk Process Facilitation
3.5. Task 5 Facilitate the formulation of project contingency reserve based on the risk exposure of the project in order to have the capability and resources to respond to realized risks.
3.6. Task 6 Provide risk data to cost and schedule analysts/estimators to ensure that project risk is properly reflected in cost and schedule estimates for the project.
3.7. Task 7 Use scenarios to validate potential risk responses and evaluate key dependencies and requirements in order to enhance the likelihood of project success.
The Plan Risk Responses process develops options, selects strategies, and agrees on actions to address overall project risk exposure and to treat individual project risks. It is a process of deciding what actions to take to reduce threats and take advantage of the opportunities discovered during the risk analysis processes. It allocates resources and inserts activities into project documents and the project management plan as required. This process is performed throughout the project.
The inputs, tools and techniques, and outputs of the process are shown in Figure 6-1.
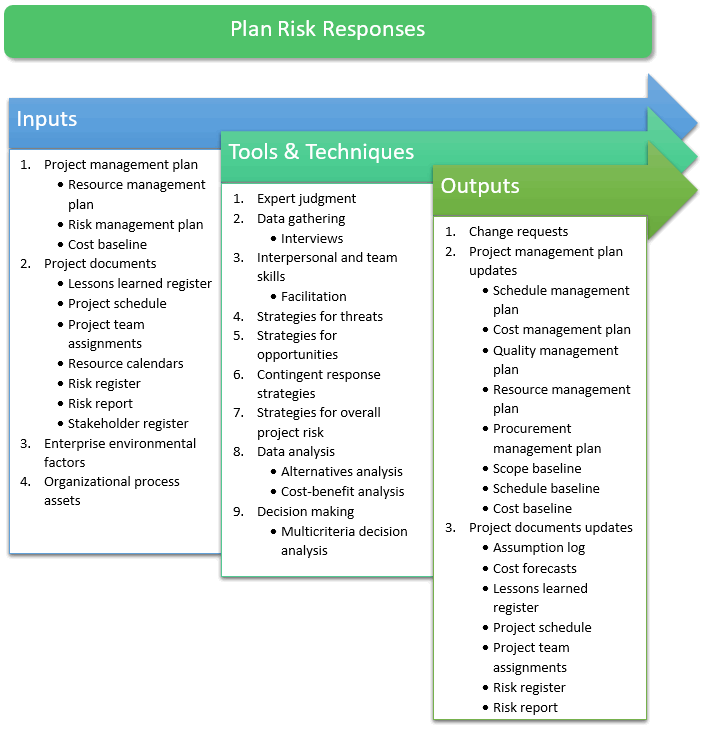
Figure 6-1: Plan Risk Responses: Inputs, Tools and Techniques, and Outputs
Figure 6-2 shows the data flow diagram for the process.
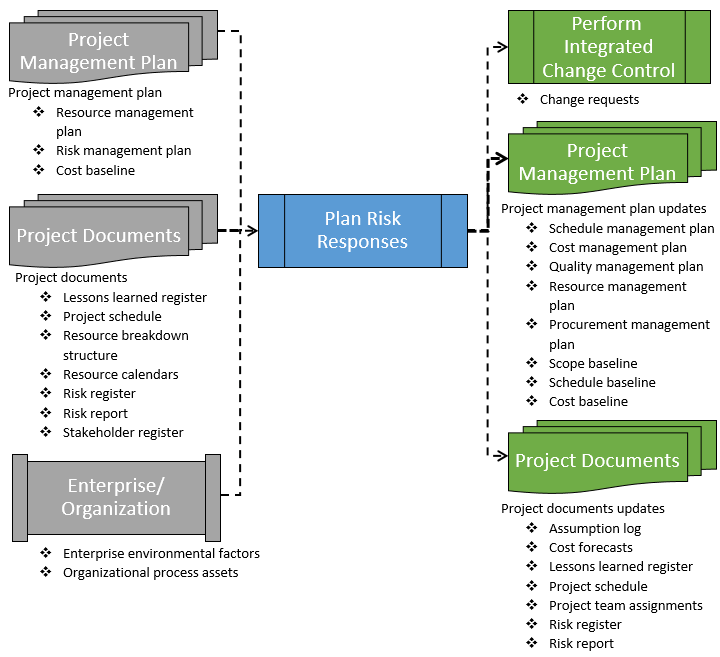
Figure 6-2: Plan Risk Responses: Data Flow Diagram
Effective and appropriate risk responses help in reducing individual threats, maximizing individual opportunities, and minimizing overall project risk exposure. A proper plan should be developed by the nominated risk owner once the risks have been identified, analyzed, and prioritized.
Risk responses should be cost effective and should also be timely, agreed to by all the parties involved. Structured decision-making techniques may be used to choose the most appropriate response.
Risk response selection depends on several parameters that are described below:
Cost of response: The cost of response is applied so as to reduce risk within tolerance levels is one of the most important parameter. For example, if the risk transfer response is applied by using insurance, then cost would be the cost of insurance.
Importance of risk: The importance of the risk is determined by the combination of likelihood and magnitude levels along with its position on the risk map.
Capability to implement response: The enterprise's capability to implement the response means that if the risk management process is mature then the risk response is more sophisticated, and if it is not, then risk response should be very basic.
Effectiveness of response: The extent to which the response will reduce the likelihood and/or the impact of the risk.
Efficiency of response: The relative benefits promised compared to quick win, business case to be made, and deferral.
Several strategies are used in this process to reduce or control risk. It's important to choose the right strategy for each risk so that the risk and its impacts are dealt with effectively. A contingency plan (or fallback plan) can be developed for implementation if the selected strategy turns out not to be fully effective or if an accepted risk occurs. Secondary risks should also be identified in this process. Secondary risks are risks that come about as a result of implementing a risk response.
Risk response plans are developed for risks with a combination of high probability of occurrence and significant impact to the project, those ranked high (or red) on the probability/impact matrix, or those ranked high as a result of Perform Quantitative Risk Analysis. Developing risk response plans for risks of low severity or insignificant impact is not an efficient or good use of the project team's time. Spend your time planning responses that are appropriate given the impact the risk itself poses (or the opportunity the risk presents), and don't spend more time, money, or energy to produce a response than the risk event itself would produce if it occurred.
Exam Spotlight
The rank of the risk will dictate the level at which Plan Risk Responses should be performed. For example, a risk with low severity wouldn't warrant the time it takes to develop a detailed risk response plan. Risk responses should be cost effective—if the cost of the response is more than the consequences of the risk, you might want to examine a different risk response. Risk responses should also be timely, agreed to by all the project stakeholders, and assigned to an individual (risk owner) who is responsible for monitoring and carrying out the risk response plan if needed.
Inputs of the Plan Risk Responses Process
Here are the inputs of the Plan Risk Responses process:
Project management plan: The components of the project management plan include:
Resource management plan: It provides information on how resources allocated to agreed-upon risk responses will be coordinated with other project resources.
Risk management plan: It documents the roles and responsibilities and risk thresholds used in this process.
Cost baseline: It provides information on the contingency fund that is allocated to respond to risks.
Project documents: For this process, project documents that can be considered as inputs include:
Lessons learned register: Lessons learned about effective risk responses used in earlier phases of the project are reviewed to determine if similar responses might be useful during the remainder of the project.
Project schedule: It determines how agreed-upon risk responses will be scheduled alongside other project activities.
Project team assignments: They show the resources that can be allocated to agreed-upon risk responses.
Resource calendars: They identify when potential resources are available to be allocated to agreed-upon risk responses.
Risk register: It provides information of individual project risks that have been identified and prioritized, and for which risk responses are required.
Risk report: It shows the current level of overall risk exposure of the project that will inform selection of the risk response strategy.
Stakeholder register: It identifies potential owners for risk responses.
Enterprise environmental factors: These can influence the Plan Risk Responses process and include risk appetite and thresholds of key stakeholders.
Organizational process assets: These can influence the Plan Risk Responses process and include templates for the risk management plan, risk register, and risk report; historical databases; and lessons learned repositories from similar projects.
Tools and Techniques of the Plan Risk Responses Process
Here are the tools and techniques of the Plan Risk Responses process:
Expert judgment: For the Plan Risk Responses process, expertise should have specialized knowledge in the topics such as threat response strategies, opportunity response strategies, contingent response strategies, and overall project risk response strategies.
Data gathering: The data gathering techniques that can be used for this process include interviews. Structured or semi-structured interviews with risk owners can help in the development of responses to individual project risks and overall project risk.
Interpersonal and team skills: The interpersonal and team skills that can be used for this process include facilitation. The facilitation technique enhances the effectiveness of developing responses to individual project risks and overall project risk.
Strategies for threats: Here are the five alternative strategies that are considered for dealing with threats:
Escalate: Risks that require escalation are generally outside the boundaries of the project, or the risk response plan is beyond the authority of the project manager to implement and resolve. However, the project manager is responsible for notifying the appropriate person or business unit that there is a threat or opportunity they need to address.
Escalated risks are not managed at a project level. They are generally managed at a program or portfolio level. When a risk is escalated, it involves alerting the risk owner and handing off the management of the risk to the risk owner. Once a risk is escalated, it is no longer the responsibility of the project manager or project team and should be monitored and managed by the risk owner.Avoid: To avoid a risk means evading it altogether by eliminating the cause of the risk event or by changing the project management plan to protect the project objectives from the risk event. With risk avoidance, you essentially eradicate the risk by eliminating its cause. Risks that occur early in the project might easily be avoided by improving communications, refining requirements, assigning additional resources to project activities, refining the project scope to avoid risk events, and so on. This technique is generally used for risks with high impact and high probability of occurring.
Transfer: The idea behind a risk transfer is to transfer the risk and the consequences of that risk to a third party. The risk hasn't gone away, but the responsibility for the management of that risk now rests with another party. Most companies aren't willing to take on someone else's risk without a little cash thrown in for good measure. This strategy will impact the project budget and should be included in the cost estimate exercises if you know you're going to use it.
Transfer of risk can occur in many forms but is most effective when dealing with financial risks. Insurance is one form of risk transfer. You are probably familiar with how insurance works. Car insurance is a good example.
Another method of risk transfer is contracting. Contracting transfers specific risks to the vendor, depending on the work required by the contract. The vendor accepts the responsibility for the cost of failure. Again, this doesn't come without a price. Contractors charge for their services, and depending on the type of contract you negotiate, the cost might be quite high. For example, in a fixed-price contract the vendor (or seller) increases the cost of the contract to compensate for the level of risk they're accepting. A cost-reimbursable contract, however, leaves the majority of the risk with you, the buyer. This type of contract might reduce costs if project changes occur midway through the project.
Keep in mind that contracting isn't a cure-all. You might just be swapping one risk for another. Other forms of transference include warranties, guarantees, and performance bonds.Mitigate: When you mitigate a risk, you attempt to reduce the probability of a risk event occurring or reduce its impacts to an acceptable level. This strategy is a lot like defensive driving. You see an obstacle in the road ahead, survey your options, and take the necessary steps to avoid the obstacle and proceed safely on your journey. Seeing the obstacle ahead (identifying risk) allows you to reduce the threat by planning ways around it or planning ways to reduce its impact if the risk does occur (mitigation strategies).
According to the PMBOK Guide, the purpose of mitigation is to reduce the probability that a risk will occur and/or reduce the impact of the risk to a level where you can accept the risk and its outcomes. It's easier to take actions early on that will reduce the probability of a risk event or its consequences than it is to fix the damage once it has occurred. Some examples of risk mitigation include performing more tests, using less complicated processes, creating prototypes, and choosing more reliable vendors.Accept: The acceptance strategy is used when you are not able to eliminate all the threats to the project. Acceptance of a risk event is a strategy that can be used for risks that pose either threats or opportunities to the project. There are two alternatives to the acceptance strategy. Passive acceptance means you won't make any plans to try to avoid or mitigate the risk. You are willing to accept the consequences of the risk should it occur. This strategy is often used when it's more cost-effective to accept the impacts of the risk than to spend time or resources developing plans to deal with the consequences. Passive acceptance might also be used because the project team was unable to come up with an adequate response strategy and must accept the risk and its consequences. Active acceptance is the second strategy and might include developing contingency plans and reserves to deal with risks should they occur.
Strategies for opportunities: Here are the five alternative strategies that are considered for dealing with opportunities:
Escalate: This strategy is appropriate when the project team or the project sponsor agrees that an opportunity is outside the project scope or that the proposed response would exceed the project manager's authority.
Exploit: The exploit strategy may be selected for risks with positive impacts where the organization wishes to ensure that the opportunity is realized. This strategy seeks to eliminate the uncertainty associated with a particular upside risk by ensuring the opportunity definitely happens. Examples of exploiting a risk include reducing the amount of time to complete the project by bringing on more qualified resources or by providing even better quality than originally planned.
Share: The share strategy is similar to transferring because you'll assign the risk to a third-party owner who is best able to bring about the opportunity the risk event presents. For example, perhaps what your organization does best is investing. However, it isn't so good at marketing. Forming a joint venture with a marketing firm to capitalize on a positive risk will make the most of the opportunities.
Enhance: The enhance strategy is used to increase the probability and/or the positive impacts of an opportunity. Identifying and maximizing key drivers of these positive-impact risks may increase the probability of their occurrence. Examples of enhancing opportunities include adding more resources to an activity to finish early.
Accept: Accepting an opportunity is being willing to take advantage of the opportunity if it arises, but not actively pursuing it.
Contingent risk strategies: Contingent response strategy, better known as contingency planning, involves planning alternatives to deal with certain risks (such as those with accept strategies) should they occur. This is different from mitigation planning in that mitigation looks to reduce the probability of the risk and its impact, whereas contingency planning doesn't necessarily attempt to reduce the probability of a risk event or its impacts.
Contingency comes into play when the risk event occurs. This implies that you need to plan for your contingencies well in advance of the threat or opportunity occurring. After the risks have been identified and quantified, contingency plans should be developed and kept at the ready.
Contingency reserves are a common contingency response. Contingency reserve strategies for risk events are similar to those for cost and activity durations. This may include setting aside funding or resources or adding contingency time to the project schedule.
Fallback plans should be developed for risks with high impact or for risks with identified strategies that might not be the most effective at dealing with the risk. Fallback plans are not contingency plans. For example, in the information technology field, we often have high-impact risks associated with upgrading operating systems or implementing new applications. A contingency plan may include calling the vendor to assist in the middle of the night (that's always when things fall apart) when we can't figure out a solution. A fallback plan in this case may describe how we are going to bring the old system back online so that users can still do their work while we figure out what went wrong with the implementation.
In practice, you'll find that identifying, prioritizing, quantifying, and developing responses for potential threats might happen simultaneously. In any case, you don't want to be taken by surprise, and that's the point of the risk processes. If you know about potential risks early, you can often mitigate them or prepare appropriate response plans or contingency plans to deal with them.Strategies for overall project risk: Risk responses should be planned and implemented not only for individual project risks but also for overall project risk. These in practice are typically dealt with on most projects at an individual level. It is also important to consider overall project risks and consider developing response plans for high-impact, high-probability risks. Here are the same risk response strategies that are used to deal with individual project risks and can also be applied to overall project risk:
Avoid
Exploit
Transfer/share
Mitigate/enhance
Accept
Data analysis: The data analysis techniques that can be used to select a preferred risk response strategy include:
Alternatives analysis: This analysis performs a simple comparison of the characteristics and requirements of alternative risk response options that can lead to a decision on which response is most appropriate.
Cost-benefit analysis: Using this analysis, the cost-effectiveness of alternative risk response strategies can be determined if the impact of an individual project risk can be quantified in monetary terms. The ratio of (change in impact level) divided by (implementation cost) gives the cost effectiveness of the response strategy, with a higher ratio indicates a more actual response.
Decision making: The decision making technique that can be used to select a risk response strategy include multicriteria decision analysis. This analysis uses a decision matrix to provide a systematic approach for establishing key decision criteria, evaluating and ranking alternatives, and selecting a preferred option. The selection of risk response is done on the basis of cost of response, likely effectiveness of response in changing probability and/or impact, resource availability, timing constraints (urgency, proximity, and dormancy), level of impact if the risk occurs, effect of response on related risks, introduction of secondary risks, etc. In the later phases of the project if the original choice proves to be ineffective, different strategies may be selected.
Outputs of the Plan Risk Responses Process
Here are the outputs of the Plan Risk Responses process:
Change requests: Planned risk responses may result in a change request to the cost and schedule baselines or other project management plan components. Change requests are processed for review and disposition through the Perform Integrated Change Control process.
Project management plan updates: Any change to the project management plan goes through the organization's change control process via a change request. The project management plan components that require a change request include:
Schedule management plan: It incorporates changes to resource loading and leveling, or updates to the schedule strategy.
Cost management plan: It incorporates changes to cost accounting, tracking, and reports, as well as updates to the budget strategy and how contingency reserves are consumed.
Quality management plan: It incorporates changes to approaches for meeting requirements, quality management approaches, or quality control processes.
Resource management plan: It incorporates changes to resource allocation, as well as updates to the resource strategy.
Procurement management plan: It incorporates changes to the procurement management plan, such as alterations in the make-or-buy decision or contract type(s).
Scope baseline: Changes in the scope baseline are incorporated in response to approved changes in scope that may arise from agreed-upon risk responses.
Schedule baseline: Changes in the schedule baseline are incorporated in response to approved changes in schedule estimates that may arise from agreed-upon risk responses.
Cost baseline: Changes in the cost baseline are incorporated in response to approved changes in cost estimates that may arise from agreed-upon risk responses.
Project documents updates: For the Plan Risk Responses process, project documents that may be updated include:
Assumption log: During the Plan Risk Responses process, new assumptions are made, new constraints are identified, and existing assumptions or constraints are revisited and changed. The assumption log ought to be updated with this new information.
Cost forecasts: It may update as a result of planned risk responses.
Lessons learned register: It is updated with information about risk responses that might be beneficial for future phases of the project or future projects.
Project schedule: It includes activities related to agreed-upon risk responses.
Project team assignments: Once the responses are confirmed, the required resources should be assigned to each action associated with a risk response plan. These resources include suitably qualified and experienced personnel for executing the agreed-upon action (usually within the project team) a specific budget and time allowance for the action, and any required technical resources to complete the action.
Risk register: When the appropriate risk responses are chosen and agreed upon, the risk register is updated. The risk register updates include: agreed-upon response strategies; specific actions to execute the chosen response strategy; trigger conditions, symptoms, and warning signs of a risk occurrence; budget and schedule activities required to execute the chosen responses; contingency plans and risk triggers that call for their execution; fallback plans for use when a risk that has occurred and the primary response proves to be insufficient; residual risks that are expected to stay after planned responses have been taken, as well as those that have been deliberately accepted; and secondary risks that arise as a direct outcome of implementing a risk response.
Risk report: It is updated to represent agreed-upon responses to the current overall project risk exposure and high priority risks, together with the expected changes that may be expected as a result of applying these responses.
6.2
Implement Risk Responses
Exam Objectives
2. Domain 2: Stakeholder Engagement
2.3. Task 3 Coach project team members in implementing risk processes in order to ensure the consistent application of risk processes.
The Implement Risk Responses process implements agreed-upon risk response plans. Its key benefit is that it helps in ensuring that agreed-upon risk responses are executed as planned to address overall project risk exposure, minimize individual project threats, and maximize individual project opportunities. This process is performed throughout the project.
The inputs, tools and techniques, and outputs of the process are shown in Figure 6-3.
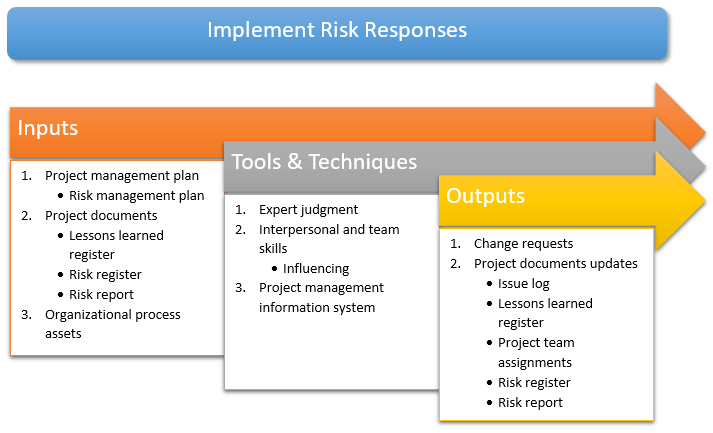
Figure 6-3: Implement Risk Responses: Inputs, Tools and Techniques, and Outputs
Figure 6-4 shows the data flow diagram for the process.
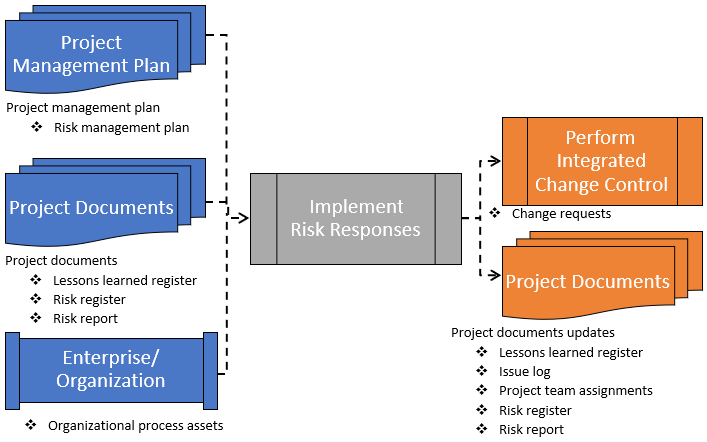
Figure 6-4: Implement Risk Responses: Data Flow Diagram
Proper attention to the Implement Risk Responses process will help in ensuring that agreed-upon risk responses are actually executed. An issue with Project Risk Management is that no action is taken to manage the risk even after the project teams identify and analyze risks and develop risk responses, which are agreed upon and documented in the risk register and risk report.
The overall risk exposure of the project and individual threats and opportunities will be managed proactively only if risk owners give the required level of effort to implement the agreed-upon responses.
Inputs of the Implement Risk Responses Process
Here are the inputs of the Implement Risk Responses process:
Project management plan: The components of the project management plan include the risk management plan, which lists the roles and responsibilities of project team members and other stakeholders for risk management. It also gives information about the level of detail for the risk management methodology for the project and specifies risk thresholds for the project based on the risk appetite of key stakeholders, which define the acceptable target that the implementation of risk responses is required to achieve.
Project documents: For this process, project documents that can be considered as inputs include:
Lessons learned register: It can be applied to later phases in the project for improving the effectiveness of this process.
Risk register: It records the agreed-upon risk responses for each individual risk and the nominated owners for each response plan.
Risk report: It includes an assessment of the current overall project risk exposure, the agreed-upon risk response strategy and describes the major individual project risks with their planned responses.
Organizational process assets: These can influence the Implement Risk Responses process and include the lessons learned repository from similar completed projects that indicate the effectiveness of particular risk responses.
Knowledge Check
Tools and Techniques of the Implement Risk Responses Process
Here are the tools and techniques of the Implement Risk Responses process:
Expert judgment: For the Implement Risk Responses process, expertise should have specialized knowledge to validate or update risk responses if required, and decide how to implement them in the most efficient and effective manner.
Interpersonal and team skills: The interpersonal and team skills that can be used in this process include influencing. The project manager or person responsible for facilitating the risk process need to exercise influencing for encouraging nominated risk owners to take necessary action where required. This skill comes into play in this process when risk owners are not part of the project team. Given that the project is probably not their top priority, the project manager may have to nudge them and remind them to monitor the risks they own and put their action plans into place.
PMIS (project management information system): It includes schedule, resource, and cost software for ensuring that agreed-upon risk response plans and their associated activities are integrated into the project in parallel to other project activities.
Knowledge Check
Outputs of the Implement Risk Responses Process
Here are the outputs of the Implement Risk Responses process:
Change requests: Implementation of risk responses result in a change request to the cost and schedule baselines or other project management plan components. The change requests are processed for review and disposition through the Perform Integrated Change Control process.
Project documents updates: For the Implement Risk Responses process, project documents that may be updated include:
Issue log: It records the issues that are identified as part of the Implement Risk Responses process.
Lessons learned register: It is updated with information on challenges that come across while implementing risk responses and how they could have been avoided, as well as approaches that worked well for implementing risk responses.
Project team assignments: The necessary resources should be allocated to each action associated with a risk response plan, once the risk responses are confirmed. These resources include appropriately qualified and experienced employees to execute the agreed-upon action, an specific budget and time granted for the action, and any required technical resources to complete the action.
Risk register: It is updated for reflecting any updates to the previously agreed-upon risk responses for individual project risks that are subsequently made as the output of the Implement Risk Responses process.
Risk report: It is updated for reflecting any modifications to the previously agreed-upon risk responses to overall project risk exposure that are subsequently made as a output of the Implement Risk Responses process.



