Information Security - Network Security applications and countermeasures
NT2580: Week 4 Hardening a Network
Analysis 4.2
Availability, Integrity, or Confidentiality (A-I-C)
Instructions:
Given the network security applications and countermeasures in the first column of the table below, explore answers to the following questions:
Where does the countermeasure belong in the seven domains of a typical IT infrastructure?
What CIA functions does the countermeasure provide?
Provide your answers in the table below.
| Network Security Applications and Countermeasures | Domains | CIA Function |
| Ethical hacker | ||
| Intrusion detection system/intrusion prevention system (IDS/IPS) | ||
| Access controls | ||
| Failover server | ||
| Automatic updates | ||
| Cryptography | ||
| Data backups | ||
| Logon rights | ||
| Computer cluster | ||
| Firewalls | ||
| Proxies | ||
| Antivirus scanners |
As a reminder, the seven domains of a typical IT infrastructure include the following domains:
User Domain: Actual users
Workstation Domain: Workstations, laptops, and end-point devices, such as smartphones and printers
LAN Domain: Physical and logical LAN technologies—100 Mbps/1000 Mbps switched Ethernet, 802.11-family of wireless LAN technologies—used to support workstation connectivity to the organization’s network infrastructure
LAN-to-WAN Domain: Routers, firewalls, demilitarized zones (DMZs), and IDS/IPS
WAN Domain: Routers, circuits, switches, firewalls, gateways, and equivalent gear at remote locations, sometimes under a managed service offering by the service provider
Remote access Domain: Virtual private networks (VPNs), laptops with VPN software, and secured socket layer/VPN (SSL/VPN) tunnels
System/Application Domain: Hardware, operating system software, database software, client/server applications, and data that are typically housed in the organization’s data center and computer rooms
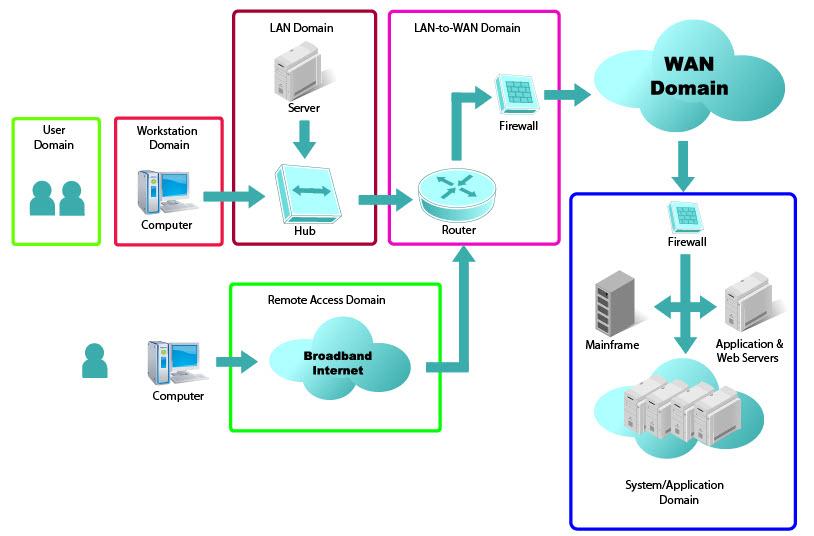
Representation of the Seven Domains of a Typical IT Infrastructure
| 2 |



