IFSM Revised
Jesse Holmes
IFSM 461: Systems Analysis & Design
February 4th 2017
Stage 2: Requirements Specifications
Professor Roxanne Liebermann
Introduction
The requirements of the consumers have driven significant organizational decisions, towards the right direction. Furthermore, there have been a constant evolution of the expectations by the customers, and has even surpassed technology with time, and have acted in a way to help in driving forward most of the transformation of business. Most significantly, if an organization can improve its process of billing then, the team put itself in the right position of strengthening the relationships it has with the customers.
Functional Requirements
As the free Business ad IT Systems Analyst, with a specialization in developments of solution for IT for the small needs of an organization. This deliverable is aimed at proposing the best option of finding a replacement for the system associated with carrying out operations, administrative duties, and finance. Further, with an increased consumer backlog in the processes of billing and processes of payments, the principal focus has been given to finding an idealist replacement for the system and methods currently being used for billing and payments for the consumers. The most important factor is the ability of the currently being used billing and payment system to be with other modern IT system and the renewed business processes. Although the organization has no budgetary ability to ensure that this project comes to pass, the following are some of the key ways in which it can ensure that it realize its objective of managing sufficiently and more efficiently the billing and payments processes for the consumers.
Output Requirements
The customers always want flexibility when it comes to options relating to billing and payments. Some of these include cases like providing an allowance for them to engage in the consolidation of the policies into a single bill that is easily understandable, enabling them to carry out proper online management of accounts, and making a choice of the schedule of payment that fits well within their needs. Moreover, there has been evolution about the preference that the consumers show when it comes to payment of the bill. This has been boosted by increased use of electronic methods of payments, one that has taken the traditional methods by storm. In the absence of flexibility by PEP to its consumers, there are high possibilities of the very consumers becoming dissatisfied and may result in the resort to considering other options. Finally, PEP needs to understand that retention of customers have a direct relationship with how they are satisfied.
Input Requirements
The primary requirement is to suit the demands of the organization. This is about efficiency and effectiveness.
Processing requirements
For PEP to have a constant growth and retention of its consumers the system, it is using for billing and payments by its consumers should be able to provide:
flexible billing
Easier payments
Clear guidelines indicating what should be paid
Clear indication of the best time to make payments
Finally, the consumers should be able to access information relating to their billing and payments quickly.
Technical Requirements
Security requirements
The computing resources within PEP are very useful for administrative activities and to help the members of the PEP’s community. As one of the individuals using these valuable organizational resources, sensitive data, and both internal and external data, there is a necessity in ensuring that you handle them with great care (Teems, American Medical Association., & Coker Group. 2000). Consequently, each or the organizational employees are required to behave in a manner that is responsible, legal, and very ethical.
System Control Requirements
The system control that will be used is Bring Your Device (BYOD). It is one of the most interesting trends being witnessed in the business world today. It implies the presence of having employee-owned devices being brought into an organization. In most cases, it will require bringing in smartphones into the business enterprise. However, the organizational employees are allowed to bring in even tablets, laptops, and even USD devices into the corporate workplace. BYOD will be very useful for the organization in its bids of facilitating IT consumerization, one that will not only allow bringing of consumer software into the organization but also hardware
Performance Requirements
The system will help with sanitization. In ensuring that there are adequate records kept on the requirements of sanitization, there is a necessity in ensuring that an HIGH-security level is taken into account. The organization should then try to consider the impact levels referred to as being either MODERATE or LOW (Digital Media Sanitization. 2008). The organization should also be taking part in testing of the equipment of sanitizations to ensure that their performances are at the recommended levels. Finally, the team should keenly consider the roles and responsibilities of media sanitization. These include the owners of the information systems and the personnel in charge of media sanitization.
Business Continuity Requirements
Ensuring that the company continues with its normal operations even after a disaster, there should be a will outlined continuity plan. For this case, PEP has a duty of ensuring that its storage devices are protected adequately as possible. To achieve this feat, have the data storage rooms fitted with fireproof walls, and sprinklers. The sprinklers should be automatic, allowing for automatic use in the case of fire. Besides, the organization should ensure it has all of its data backed up at a secure location off-site. Finally, there should be a clear policy to guide in the protocols to be used in the recovery of data in case of an emergency.
System Scope Diagrams
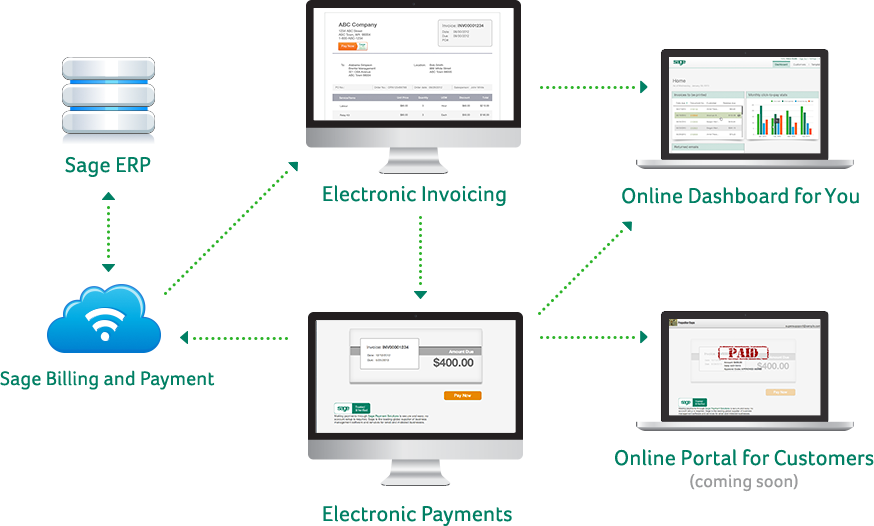
Data Flow Diagram
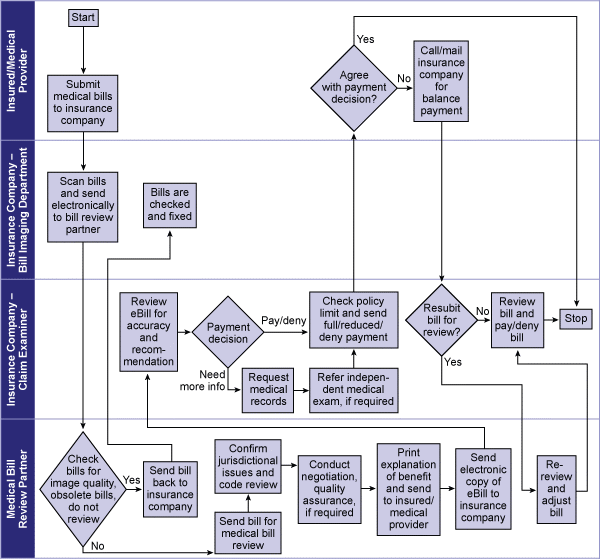
Conclusion
In conclusion, PEP’s top management should approve the draft. In ensuring that the organization has a maintenance of consistencies, a standardized policies format has been proposed. Therefore, due to the identification of the need for revision to the current Employee Handbook, the following draft has been submitted to help in propelling the organization forward. The computing resources within PEP are very useful for administrative activities and to help the members of the PEP community. As one of the individuals using these valuable organizational resources, sensitive data, and both internal and external data, there is a necessity in ensuring that you handle them with great care. Consequently, each or the organizational employees are required to behave in a manner that is responsible, legal, and very ethical.
The employees should realize that when the organization outlines the necessity of engaging in an acceptable use then, they should be at the position of respecting the rights that other computer users have, the integrity that the physical facilities have, and all factors about both contractual agreements and pertinent license. When one violates the Acceptable Use Policy, then the organization will take adequate disciplinary actions, with the inclusion of the affected individuals being restricted or even losing the privileges associated with access to the network (Acceptable Use Policy | Computing & Information Services. 2017). If the violation is considered to be far-reaching then, the affected employee can either be terminated or even suspended. Finally, all of the organizational workforces should be aware of the reality of being subjected to the local, federal and even stat laws that tend to put a governance of the interactions that occur within the internet. Further, the outlined policies are subject to being changed in the course of the development of the federal or the state laws.
References
Acceptable Use Policy | Computing & Information Services. (2017). It.brown.edu. Retrieved 1 2017, from https://it.brown.edu/computing-policies/acceptable-use-policy
Digital Media Sanitization. (2008) (1st ed.). Standard Operating Procedure. Retrieved from https://www.nasa.gov/pdf/419924main_ITS-HB_0035-%20_.pdf
Teems, C. M. C., American Medical Association., & Coker Group. (2000). Assessing and improving billing and collections. Chicago: AMA Press.
What is BYOD policy? - Definition from WhatIs.com. (2017). SearchMobileComputing. Retrieved 13 January 2017, from http://searchmobilecomputing.techtarget.com/definition/BYOD-policy



