Methodology
Running head: INTRODUCTION AND METHODOLOGY 1
Introduction and Methodology
Information Assurance Framework for Web Services
Introduction
Internet based solutions, and web based services that are offered to the customers has become a common practice in the businesses. Right from B2B segment, to B2c and C2C, there are many web services and web based applications that are predominantly used in the business environment (Kahonge, 2013).
Adaptation and implementation of web based application systems has certainly supported the stakeholders of business in improving the ease of business communication, transaction processing and other such key business functions. However, one of the critical challenges that are envisaged in the business process are about issues pertaining to the information assurance issues in the web based application systems and processes that are adapted by the organizations (Al-hamami & et.al, 2012).
An organization’s weakness can open the door to security vulnerabilities. IT professionals may be put in a compromising position to prioritize system administrative tasks that are beneficial to a company’s bottom line over evaluating and proactively defending against security risks.
For instance, in the case of some of the web application systems, the data and transaction management is highly secured and there are potential solutions that are managed by the organizations. In the case of some web application systems, despite the robust solutions that are managed by the companies, still the impact in terms of information security breach, data availability issues, identity and access control issues and many other such factors has been more prevalent (DAN J KIM & et.al, 2004).
In the case of information assurance problems, both the technical and non-technical issues to impact the efficacy of the system and could lead to more complexities of information assurance.
The key elements of information assurance problems that are encountered by the companies in the web application solutions are depicted in the following figure, and it is very important that the organizations focus on addressing such issues in an effective manner (DAN J KIM & et.al, 2004).
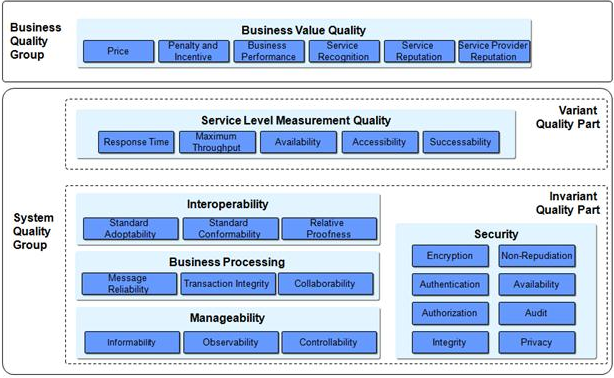
Source: http://docs.oasis-open.org/wsqm/WS-Quality-Factors/v1.0/WS-Quality-Factors-v1.0.html
Figure 1 Information Assurance Model
In the case of any of the web services irrespective of the category, and the system, if the factors that are depicted in the figure are addressed, the outcome from the solutions could be more effective for the organizations. The scope of interoperability has become a significant factor and with the emerging practices of collaborated information management issues, it is very important that the companies focus on having robust systems and practices in place (DAN J KIM & et.al, 2004).
Despite the fact that there are certain frameworks that are developed for information assurance management, still in terms of impacts that are envisaged in the process, it can be stated that there is need for more effective frameworks that could be adapted, and some kind of common parameters of CSFs that could be considered by the companies in terms of handling the information assurance in the web systems (Al-hamami & et.al, 2012).
Considering such factors and the scope for the study, the objective for the study is about evaluating the CSFs that are important for the services and the kind of fundamental framework that is essential in the development of a good web information system (Al-hamami & et.al, 2012).
For the chosen project study, the focus is upon practicing the action research method of research process that shall support in gaining quality insights, practical experience in the process and towards developing solutions that shall support in implementation.
Methodology
Research methodologies play a vital role in the successful outcome of a project study. Considering the objectives of the study and the scope for the study, the method of action research process has been chosen for the proposed study (Brydon-Miller, 2003).
The Action Research process which is also called as Participatory Research is the process of conducting the research in which the emphasis is more about understanding the subject of the study by being part of the subject environment. This kind of research methodology is more commonly used in the on-job training and towards educational programs with intensive structure of practical learning and development (Young & et.al).
The process of conducting the action research method could be attributed to the process of four key steps which are very important in the process of conducting the action research.
Plan
Action
Observation
Reflection
Action research method involves no structured practices or timelines, and is more about the iterations way of conducting the scope of research. For instance, depending on the subject of the study, and the scope for research a specific iteration shall be planned in the study.
Using the four key steps discussed above, for iteration, the plan, action, observation and reflection is carried out, and the process of iteration planning and learning is continued till the desired outcome and the objective of the study is achieved (Brydon-Miller, 2003).
The following figure represents the kind of cyclic approach followed in the process of conducting the iterations as a part of action research process.
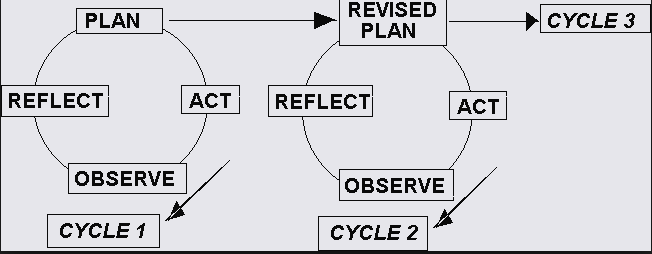
Figure 2 Action Research Process
Taking in to account the scope of work, the feasibility for being part of the work environment and gaining insights about the information assurance issues and towards developing the framework, the method of action research process is adapted in the study to focus on the developments that could support in achieving successful outcome for the study (Schruijer, 2006).
The process of iterations shall be followed with the requisite framework that can support in gathering as many insights possible about the organizational practices in terms of information assurance management, and the iterations shall be adapted till the right kind of outcome for the proposed objective is achieved from the system (Brydon-Miller, 2003).
References:
Al-hamami, A. H., & et.al. (2012). Web Application Security of Money Transfer Systems.
Journal of Emerging Trends in Computing and Information Sciences VOL. 3, NO. 3 , 365-372.
Brydon-Miller, M. (2003). Why action research? Action Research Volume 1(1) , 9-28.
DAN J KIM, D., & et.al. (2004). Information Assurance in B2C Websites for Information
Goods/Services. Electronic Markets Vol. 14 No 4 .
Kahonge, A. M. (2013). Web Security and Log Management: An Application Centric
Perspective. Scientific Research Vol.4 No.3, .
Schruijer, S. G. (2006). Research on Collaboration in Action . International Journal of Action
Research Vol.2 Issue: 2 , 222-242.
Young, M. R., & et.al. (n.d.). Action research: enhancing classroom practice and fulfilling
educational responsibilities. Journal of Instructional Pedagogies , 1-19.



