Complete the following task below.
15
ONLINE Ordering
System Analysis
James Williams
Brian Bertrand
Systems Analysis, Design and Integration
IT425-1701B-03
Mar 15, 2017
Table of Contents
Week 1: System or Application Overview
Description of System or Application’s Capabilities
I am going to be creating a Relational Database for an online clothing company called Don Ameche (DA) Couture. Here at DA Couture we will need a database to keep track of customer information, sales, number of pieces ordered, total number of items in stock and so forth. This is the reason I chose a Relational Database to manage my company information as well as my customer information. DA Couture will pride itself on customer satisfaction to insure that our customers will ensure timely deliveries as well as up to date pricing on every piece of clothing in our inventory. I want my database to ensure that every item is accounted for in real time to ensure accuracy on our garments. This database will ensure that our company runs smoothly, efficiently, as well as productively. The ideal key of a Database management system is to have a structured work system rather than an unstructured work system.
Week 1: Requirements and Specification
Methods Used to Gather Requirements
There are 7 steps to the SDLC/DBDLC which outlines the process of designing a database. First we have the planning stage of the database. In the planning stage of the SDLC/DBDLC is where a solid plan for creating your database. Primarily there are there steps in this phase that should mainly be taken. First we define the system by identifying what system will be required to support the goals of the company. Next we will set a scope which is a written definition of the project scope. The project scope just defines the high-level system requirements in other words a basic definition of the system. Lastly we will define the project plan which is basically the what, when, and who questions. The definition of the project is also dates that are set to which certain activities should be performed and completed. The second stage of the SDLC/DBLC is the Analysis phase of the database. In the analysis stage is where the end users and IT specialist work on gathering, understanding and documenting the requirements of the proposed system which is called a joint application development (JAD) session. Then all of the end-users sign off on the project.
There third stage of the SDLC/DBDLC is the design phase. The overall goal of the design phase is to a blueprint of how the system should work. This is also the phase where a graphical representation of the system is created which is basically the modeling stage. The fourth stage of the SDLC/DBDLC is the development phase. The development stage is where take all the detailed design documents and tan form them into an actual system. This is where the technical architecture is bought also where the databases are created and software programs are written. Next we have the testing stage of the SDLC/DBDLC. This is the phase where you verify that the system works and meet all the requirements defined in the analysis phase. First the test conditions are made then the testing is done to ensure accuracy. Then we have the phase six of the SDLC/DBDLC the implementation stage. This is the stage where the new system is distributed to all employees to begin using to perform their everyday job. Basically you provide a user guide for employees on how to use the system then you train them on how to use the system correctly. There also a few methods of implementation parallel, plunge, pilot, and phased. Each stage gives you different options on how to implement you system throughout the company. Lastly we have the maintenance phase of the SDLC/DBDLC. In the maintenance phase you monitor and support the system to make sure it meets company’s goals. First you setup a help desk to answer questions then you update the system as the company changes.
Week 2: System or Application Design
The Entity Relationship Diagram
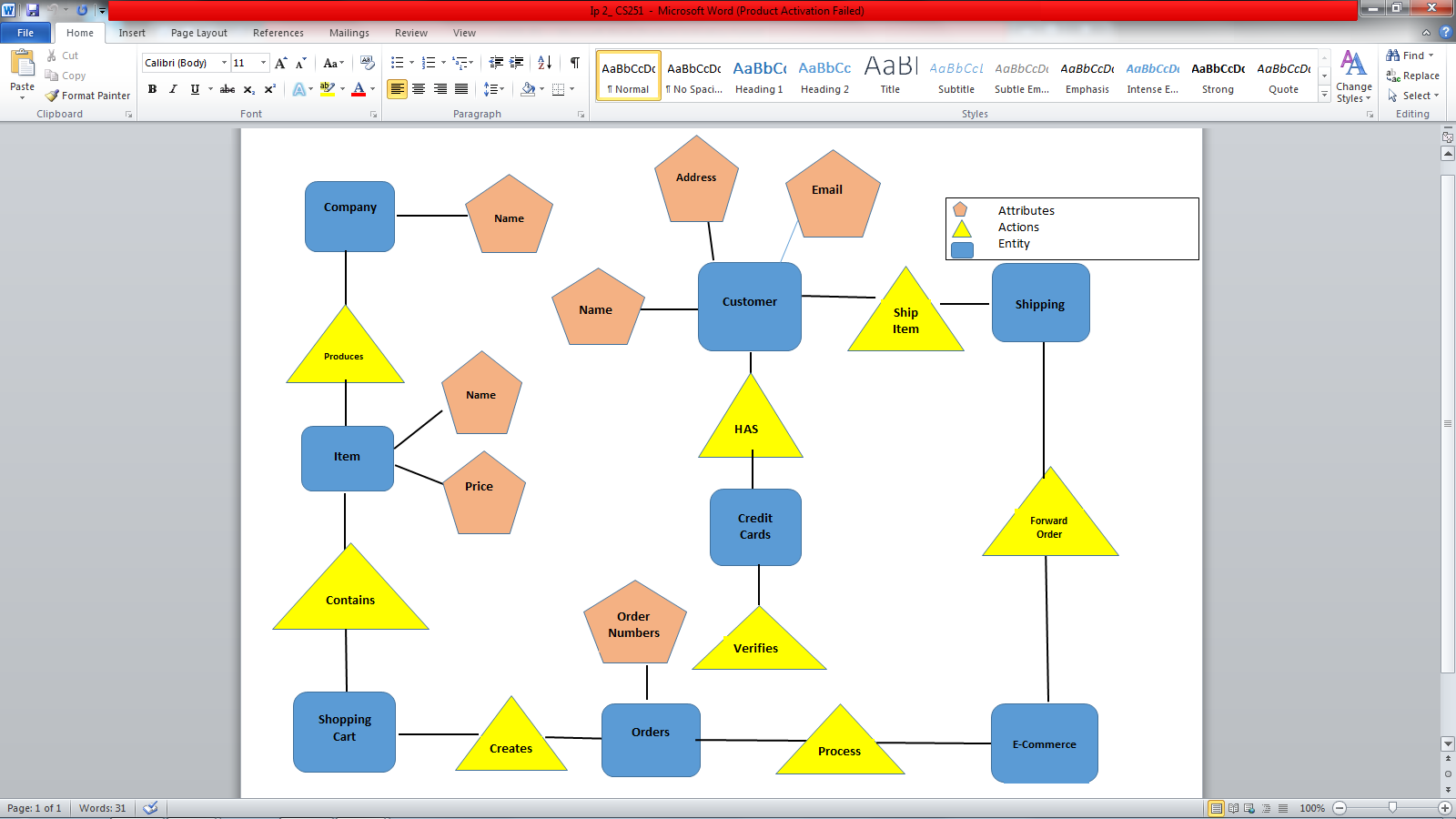
The Entity Relationship Diagram (ERD) above illustrates the logical structure of the database that I am going to create. ERD’s are very useful when it comes to creating a relational database because it shows how the data is connected in a general way. To create an ERD you have to identify the relationship, describe the relationship, and add attributes. This gives the viewer a chance to know what he or she is looking at and also gives a clear understanding. Data modeling is a technique that can be used to define business processes around the world which is described as an ERD. I hope I have given enough insight as to what a ERD is, how it is created and what its used for.
The Logical Model and Normalization
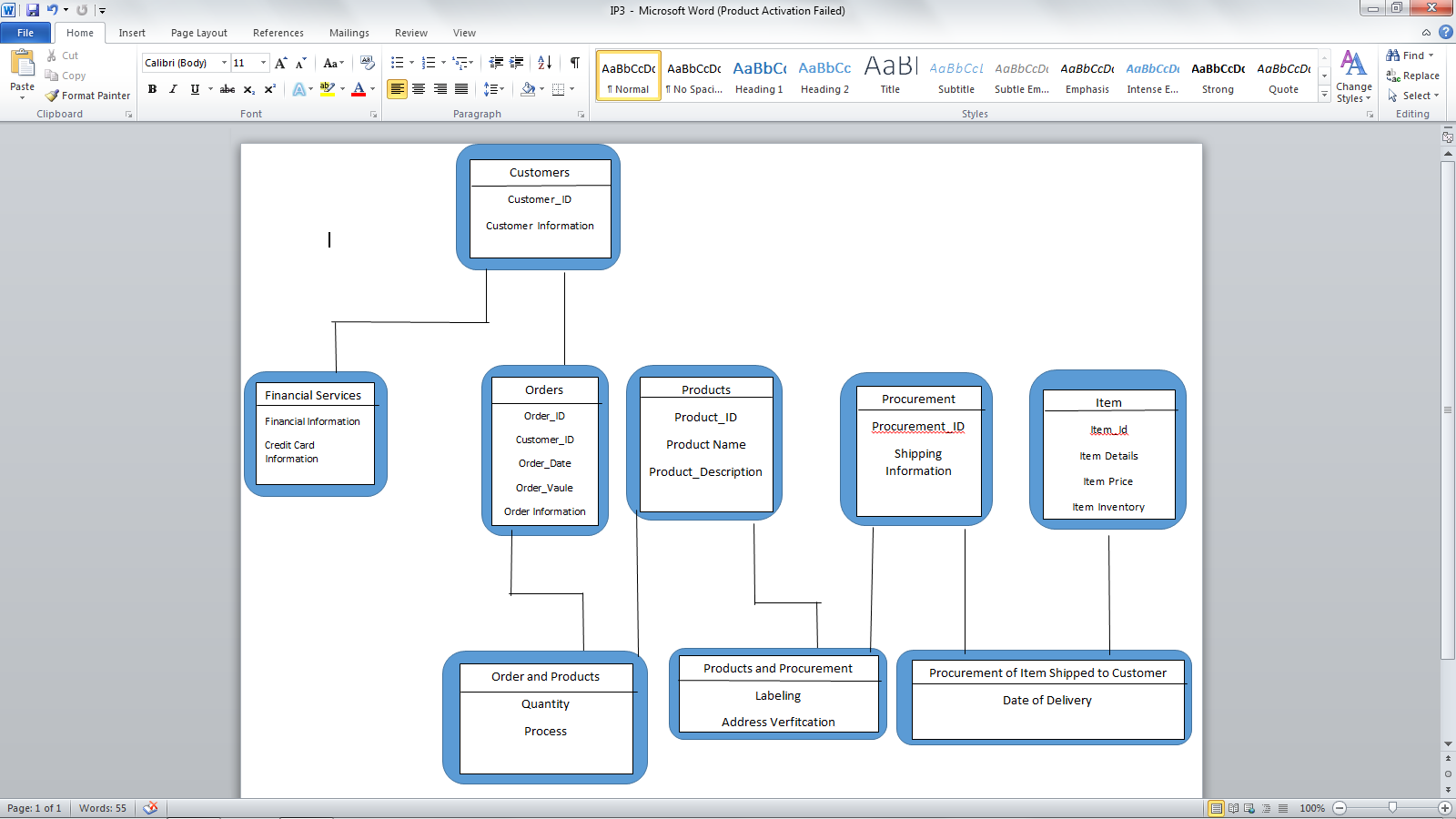
Normalization of a database is a process of organizing the data to avoid data redundancy, insertion anomaly, update anomaly and delete anomaly. The three anomalies that I have just stated occur when a database is not normalized. First normal forum (1NF) is an attribute column of a table and cannot hold multiple values only atomic values. As I have shown in the logical model above each table only have a single value and not multiple values. A table is considered to be second normal forum (2NF) when it is in 1NF, and non-prime attribute is dependent on the on the proper subset of any candidate key table. This also explained in the model above. A table design is considered to be in third normal forum (3NF) when the table meets 2NF transitive functional dependency of non-prime attribute on any super key should be removed.
Week 3: Test and Quality Assurance Plan
Unit Testing
Unit testing is a kind of software testing method which individual source code uses to identify and locate some other computer program which are connected to a control information. Some of the other aspects that the unit testing locates includes operating methods, and usage techniques. The above aspects are majorly tested to ensure that their functionality is okay and fit. At a glance, analysis of units and attest that they are the smallest elements of an application. In technical programing setting, one part can be used to complete a module other than the use of individual function and also method.
Extreme programing on the other hand needs a Unit testing frameworks and also Language-lebel unit texting that could support some unique applications in terms of functionality. Any test that could be conducted in this case are always conducted within the unit testing and it is often automated. At times the unit testing can be manual. This form of testing technique is included as a part of the extreme programming (XP) and the Unit testing structure. Language level unit testing is the most unique and relevant and realistic method of software development and growth and it takes a special way to come up with its creation as well as testing and revision.
The agile group that conduct the Unit testing tend to understand the way the short-term programs can be written by the programmer on the development team. The above exercises a narrow part of creation of the code and thus enhancing the issue of comparing the results with the set objective of the program.
Software Testing
Software testing and system testing is mainly done on both hardware and software. The testing is mainly done in order to ensure that the system fulfils its specified objective. There are a number of system testing. Some lies within a range of black-box-testing while others tend to demand more knowledge of the inner plan of the parent source code (Arbyn, Anttila, Jordan, Ronco, G., Schenck, Segnan, & Von Karsa, 2010). Areas of testing in both software and system testing is mainly done within functional requirement specification. System testing is never aimed at design alone. It also looks at the buyer’s needs and prospects. The system should be testing to ensure that it is well beyond any imaginable doubt. Any errors should be tracked and be reported during the execution runtime (Thijssen, Weijers, & de Korte, 2010). The application implementation should be analysed and any bug be reported incise there exist any. Some exposure testes can identified and be reported as:
Crashes
File In file Out (I/O)
Functional errors
Exceptions
Database errors
Testing for user acceptance denoted as UAT is the last in the software testing. The UAT enables the final users to test the system and ensure that it adheres to the roles it is meant to handle. UAT should approve the system before being implemented into the other existing systems.
Product possessor is defined as an individual who performs testing and records some critical issues by the UAT before the software in question comes into the market. The possessor becomes the closed obsession to the actual world of software use (Lewis, 2016). It is ensures that the users gets the options of acting together with the software in question and by so doing identifies any aspect that was overlooked by the developer. The possessor can also can identify some miscommunication that was done during the development process.
Quality Assurance Plan
Quality assurance plan is one of the critical aspects in the software development life cycle. It ensures that all that the software buyers get quality software at the market. It ensures checking and controls all stages of quality assurance and ensures that right quality is provided in the market. The main reason for quality assurance is provide an easy establishment of assurance deeds that is driven in delivering right goods and services to the customers at their point of needs. Detection techniques are involved in aggregate data and administrative information that indicates whether the set target is achieved. Assessment methods: this involves the analysis of what the product does and its relevance in the market. It ensures that the set product offers what it was meant to. Finally, the QA, ensures that the stakeholders respects the procedures, standards and control of the system.
In conclusion, all practices that are linked to the QC should have a Quality manual. The manual helps in simplifying the target of the software/application in question. A pilot phase is mainly used to ensure that ambulatory office related issues are addressed effectively. It also contributes to ensuring that the management of the organization is effective.
Week 4: Development Strategy
Software Obtaining Options
In the process of software development process, a company in questions needs to look at some three important options. The impact of internet, in house software development and software outsourcing option. All of the above mentioned optioned below and later the cost and benefits of each given underneath.
The impact internet Option
SaaS according to statistics as per the 2011 the statistics indicated that about 25% of new business software were implemented in 2011. And the SaaS gain a $40 million when it comes to the aspect of traditional and web- based system development. The system is mainly affected by the issues of compatibility. They are mainly designed to run in local and wide area network companies. The system most often makes use of internet links and other related resources (Pedrazzi, Zini, & Tartarini, 2010). The web-based features in this case are considered to be enhancements not core. The resources here are delivered as internet resources and bares an extension of .NET or sometimes as web sphere. Majority of the companies tend to depend on traditional systems. Web 2.0 tend and cloud computing tend to promote the aspect of interactivity. It is mainly applied in the blogs, social networks and many more. Cloud computing is relevant and commonly used in a business setting and personal internet users.
Outsourcing option
The above is another software development option that can be recommended. A firm that provides the outsourcing services is mainly referred to as application service provider (ASP). The business managed services are also managed by the hosts. The outsourcing model is often sometimes referred to as fees model. It has a fixed fee set depending on the specified level of service provided. The fee model has varied fees subscriptions that varies with the number of workstations that the application can be accessed from. Usage model under thus option charges variable fee depending on the volume of use of the application within a given set of time.
An issue with the outsourcing issue arises from the critical IT mission. The mission states that an IT service can be outsource on if the cost of caring out the transaction is attractive, reliable and the meets the organizations’ needs. Outsourcing has a tendency of affecting organizations’ day to day operations and thus can bring some serious concerns within the organization.
In house development option
This option calls for the organization in question to make its own applications. The organization makes sure that all aspects and application that are used within a given organization are developed within the organization (Vrugt, 2016). Such form of option makes the operations within the organization to be cost effective. Security is also enhanced
Cost analysis
Purchasing of application requires less cost as compare to the aspect of in house design. The buying of the software makes the organization to save time of development since the only thing that the bought software needs is the installation which does not cost the organization in question any time. Buying of software saves the organization’s payroll since the organization doesn’t need any reliable technical stuff. Future upgrades calls for the vender to be involved in the upgrade process.
Recommendation and Conclusion
To recommend, of the three option, I prefer the outsourcing option. The outsourcing option requires less cost to implement and thus saving the organization in question in terms of cost and time. For a company to grow using the least amount it has within its premises. It is better for such a company to outsource its software since it will help in cost minimization and profit maximization.
Week 5: Integration and Development Plan
TBD
System Analysis



