read the discripo and follow the gauid and please change everyword
ATM TRANSACTIONS USECASES 10
Abstract
Use cases are one of the UML diagram used to illustrate systems for its design. The purpose of a use case diagram is for information gathering for a system, identifying the system boundaries and showing the interaction of different users of the system. In this report, the case of an ATM withdrawal, deposit and money transfer use cases are explained and illustrated. These diagrams were designed using Visual Paradigm software for UML diagram design
Keywords: withdrawal, deposit, transfer, use case
ATM Withdrawal, Deposit and Transfer Use-cases
An ATM is a machine that allows one to withdraw deposit and transfer money through self-service procedures. These activities are in turn branched into subsystems and subroutines that described the system in details. The main actors of the ATM system include the user, the bank consortium and the ATM. The main actions performed are deposit, withdrawal and money transfer.
Withdrawal
The withdrawal procedures require that the customer first inserts the ATM card. Then the ATM requests for the password after validating that the ATM card is not damaged, and it’s valid. Then it verifies the pin inputted with the database at the consortium. If the password matches with the customer’s account details, then the menu option is provided.
After the customer has the menu provided, the required selection to withdraw is the withdrawal option. The customer selects the withdrawal option, and the ATM retrieves the information of the customer. If there is a zero balance in the account, then the request is aborted, and the customer informed on the insufficient account balance (Shelly, G. 2012). If the funds in the bank account of the customer are enough, then the transaction is committed where the customer enters the amount he or she would like to withdraw this involves retrieving the consortium database and subtracting the amount requested for withdrawal. Then the money is output for the customer to withdraw.
An illustration of the withdrawal use-case showed in Figure 1.
Deposit
The deposit procedures require that the customer first inserts the ATM card. Then the ATM requests for the password after validating that the ATM card is not damaged, and it’s valid. Then it verifies the pin inputted with the database at the consortium. If the password matches with the customer’s account details, then the menu option is provided.
Deposit transactions request customers to select the account type in to deposit to, usually through viewing possible accounts from a menu of accounts, and then entering the amount through the keyboard of which one would like to deposit. Firstly, the bank consortium receives a message from the ATM on the transaction to verify on possibilities that the ATM would accept deposits from the particular customer to that account (Shelly, G. 2012).
If approved, the transaction is received by the machine and the envelope containing the cash from the customer or checks then a receipt is produced or customer to get a statement of the transaction. After the envelope is received, another message is then sent to the bank, which is aimed to confirm that this bank would credit the pertinent customer's account - liable to manual verifications of a deposit envelope’s contents by a given operator later. This receipt of the envelope then gets recorded in an ATM's log.
When a transaction committed, a receipt is produced by the ATM depending on the user selection. If a user selects printed to the screen, then a receipt is produced in softcopy that displayed on the screen. If the printed form is selected, then a printed receipt is produced
The deposit transaction may cancel when the Cancel button is pressing any time previous to inserting an envelope holding the deposit (Shelly, G. 2012). This transaction is usually automatically cancelled if a customer does not insert the envelope with the deposit inside within the reasonable set period after the customer is requested to do so.
Figure 2 is an illustration of the Use Case diagram of the deposit transaction.
Account Transfer transaction
The transfer transaction requires that the customer first inserts the ATM card. Then the ATM requests for the transfer transaction after validating that the ATM card is not damaged, and it’s valid. Then it verifies the pin inputted with the database at the consortium. If the password matches with the customer’s account details, then the menu option is provided.
The first step in transfer transaction is to select the fund transfer from the menu of options. Then the customer selects the transferee bank and then enters the account number for the account of which the customer transfers funds to then the customer selects which type of account valid for the transaction such as a current or savings account (Smullen, J).
After feeding all these information, the customer enters the amount to pay or transfer to the specified account. This requires a message to the bank consortium to validate the possibilities of transferring the amount to the specific bank account. A return message is produced to inform the customer of a committed transaction or an aborted one.
The final procedure is the production of a printed receipt by the ATM on the transferred funds.
Figure 3 illustrates the account transfer use case
Ethical issue
The development and use of an ATM outlay various ethical issues that make the customers money account vulnerable to fraud.
The development of an ATM, as described in the above UML development using the use case diagrams, possess a lot of threats by black hackers. This is because the designs show how the ATM system works. When detail designs of the system expose to malicious persons, then these people can learn how the system works and then creatively come up with tricks to identify the weaknesses in the security of the ATM system (Smullen, J). Thus, they utilize these weaknesses to gain authorized accessing the system by bypassing the security measures. They would then do malicious activities such as transferring accounts to the Wong recipient other than the intended account
One form of this fraud is card swapping. This involves the criminal setting an additional card reader by placing it over the card reader of the ATM. When a customer enters PIN information while the ATM card is in the fake card reader, then the criminal can access this information which is recorded unwarily to the ATM user. The information is then used to conduct fraud and authorized access the person account (ATM fraud, web)
These ethical issues would be catered for when greater effort spent in ensuring a safe development and deployment of the ATM is set up. Also regular and monitored maintenance of the ATM and its closet should then taken into consideration.
Figures

Figure 1

Figure 2
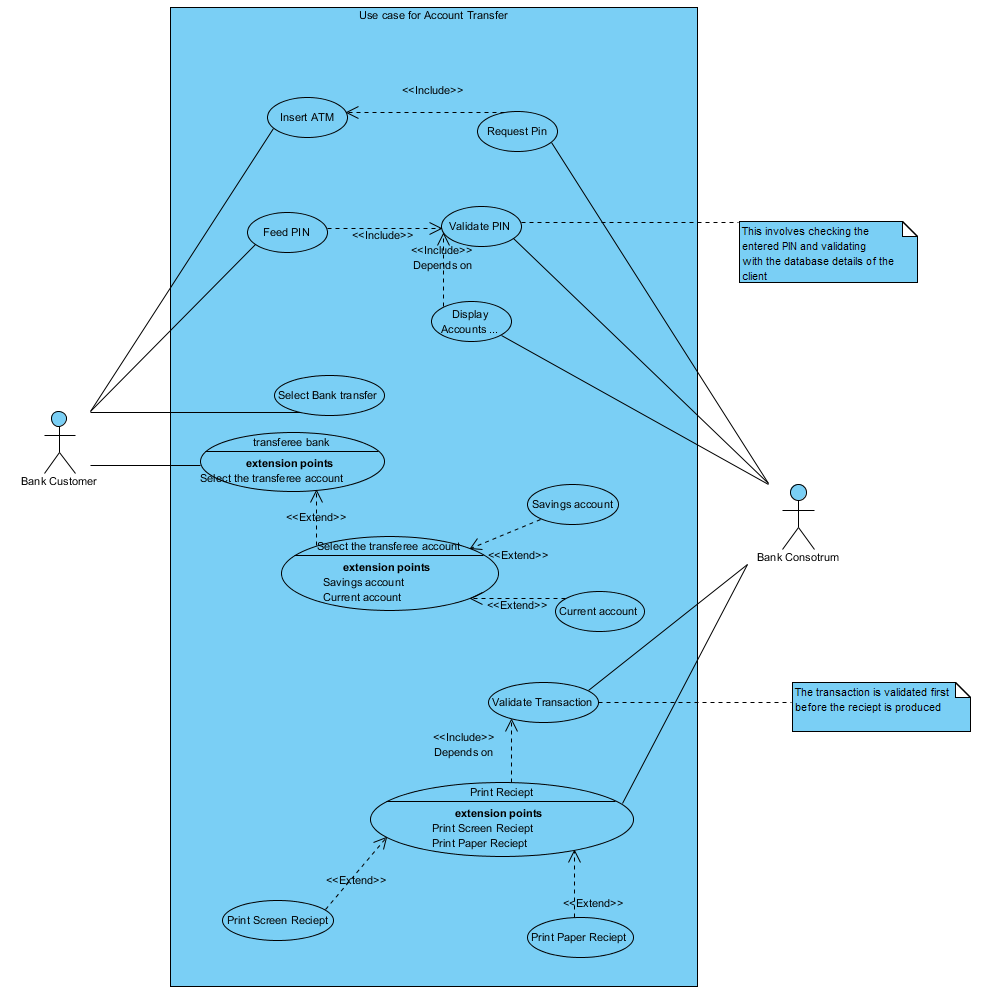
Figure 3
References
ATM fraud. (n.d.). Retrieved from http://www.ecobank.com/sc_atm.aspx
Shelly, G. (2012). System analysis and design. (9 ed., p. 16). Boston, MA: Course Technology, Cengage Learning.
Smullen, J.. (Eds.), The Dictionary of Finance and Banking. : Oxford University Press. Retrieved on 22th Nov. 2015 from http://www.oxfordreference.com.libdatab.strayer.edu/view/10.1093/acref/978019922974 1.001.0001/acref-9780199229741-e-211



