CIS Final Project
Running head: NETWORK INFRASTRUTCTURE AND SECURITY
Project Deliverable 4: Infrastructure and Security
CIS498
June 4, 2017
Introduction
Knight Inc will be growing in the next few years and it will require robust and reliable network infrastructure. The company will need to be sure that it data can be accessed and handled in an environment that is safe and technically sound. The solutions will need to be up to date and be updated regularly. Security is very important and it will be paid the utmost attention to ensure that no bad elements are allowed into the network to cause damage and endanger the company’s data and infrastructure.
Logical and Physical Topographical Layout
Star topology will be used for the physical network. This is where all devices in a network are connected to a central hub. All resources are drawn from this hub including bandwidth that allows access to cloud resources. Star topology simplifies the matter of network management as everything can be deployed from the central hub (Shinde, 2014).
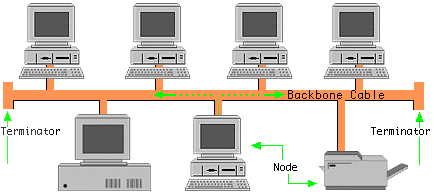
Bus topology will be used for the logical network. It is a topology where a backbone is the anchor on which computers connect to and request data and other resources. The logical network exists on a different subnet and as such can have different topology than the physical network. Computers are identified by IP addresses. Bus topology is good as it provides the computers with capabilities to access data as they need it by simply requesting (Shinde, 2014).
Figure 1 - Physical Layout
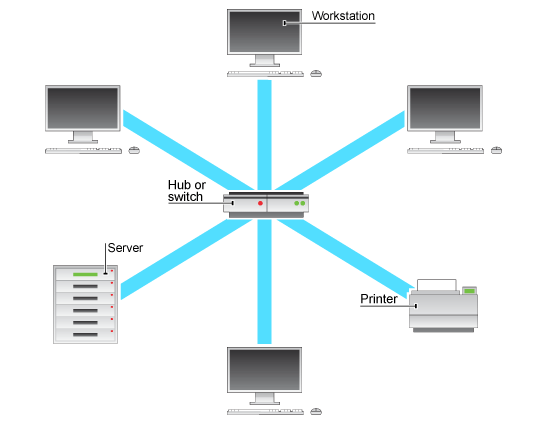
Figure 2 - Logical Layout
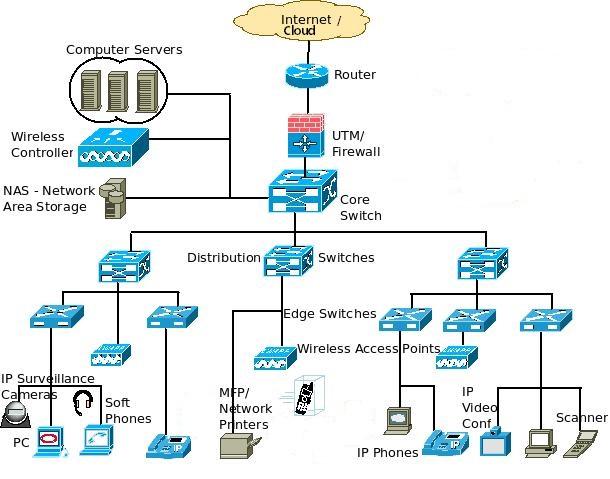
Network Components
Incorrectly deployed and configured firewalls and intrusion detection systems can be vulnerabilities to their networks. Given that they are meant to monitor traffic coming to and from the network and determine the harmful ones, this will not be accomplished. This makes it easy for malware to access the system. Fixing this requires that the firewall and the intrusion detection system be regularly checked for any signs of vulnerabilities and be fixed accordingly. (Peltier, 2013).
New devices like smartphones and tablets can also cause problems for the network. These are usually used when the company has its operations hosted on a cloud. This then allows for access to data from a variety of devices, which is every device that can access the internet. For companies that allow its employees to use personal devices to access work data, they are especially vulnerable. Viruses could easily be uploaded to the cloud without even the device owner realizing. The fix is to ensure that all mobile devices used to access the cloud are company issued so that they can be assessed and equipped with the necessary security measures (Peltier, 2013).
Old credentials could be used to access the network discreetly without raising suspicions, these could be the credentials of employees that have left the company or even default credentials yet to be changed. Any user that gets to know this can use them to access the company’s cloud facilities and could either launch malware there or steal valuable data. To prevent this, all default accounts and credentials should be disabled with immediate effect. As for the old accounts, the administration should deactivate accounts once an employee leaves the company (Peltier, 2013).
Weak Wi-Fi security protocols can make it easy for a user to gain access into the company own private network. With Wi-Fi, they only need to be adjacent to the company’s building and from there they can attack the network. The company should use Wi-Fi Protected Access 2 (WPA2) to secure its network (Peltier, 2013).
Since a single server is able to house multiple virtual environments, this can make the network vulnerable. Having to depend on a single server like that can mean that any physical damage to the server can really jeopardize the entire system. This is especially if the virtual environments included critical data and applications. This can be remedied by keeping the server in a safe place away from possible danger either man made or natural (Peltier, 2013).
Figure 3 - Network Components
Security Policy
The CIA Triad is a security standard that was developed to encompass the most important aspects of security for a system. It consists of confidentiality, integrity and availability. Confidentiality ensures that access to data in the system will be restricted to only the users authorized to do so. Integrity is meant to guarantee that information is changed in any manner or form during transmission. Availability ensures that information can be accessed by authorized users at any time they may need to do so.
Users interacting with a given system are constantly accessing data. The confidentiality of this data gets to differ across the system according to the security principles being used. Access control is as it is the most effective method of maintaining confidentiality. The system administrator by limiting the users that have access to certain data can ensure to some degree that the data cannot be compromised. The administrator will create a profile for every user in the system. However, not all users will have the same access privileges to data within the system. The data will be classified according to their sensitivity and the more sensitive the data is, the less number of users authorized to access it. Controlling access can also be done by applying the principle of least privilege. With the organization having different kinds of data, it would not be prudent to provide blanket access. Instead, users will be granted access in accordance to their responsibilities. What this means is that an employee of the company will only have access to the data they need to fulfill their responsibilities and only that. Employees that work in sales will not need human resources data to fulfill their responsibilities and will therefore not be granted access to human resources data. By putting in place measures to ensure confidentiality, the company will be protecting its data from incidences of internal breaches. This is where employees will inadvertently or otherwise be the cause of a data breach. Given that screening and background check will be done before allocating a higher security profile to an employee, then the most sensitive should end being handled by only the most well regarded users (Axelrod, Bayuk, & Schutzer, 2012).
The integrity of information is maintained when it remains unchanged from the time it was sent through its transmission to the recipient. Information is exchanged every day in any organization. Whatever the purpose of the exchange, it is imperative that the communication is not intercepted and most importantly that the data being exchanged is not modified in any way. In a lot of cases, the information being exchanged will be used to make important decisions and this will make it very important to ensure that there is no tampering with the information. The company would really suffer if executives were making important strategic decisions using faulty data. In transit interception happens a lot and involves a malicious user taking over a transmission and using that opportunity to modify or even delete the data. Once the communication has been retuned, it will go straight to the recipient who will be receiving a faulty message. Any decisions made as a result of the data will be tainted and therefore unreliable. With data integrity, the recipient needs to believe in the information they receive and actually believe the contents of the message as they are delivered. Data integrity is not just threatened by human interventions but can also be as a result of problems with the system. System failure could to transmissions being received as incomplete or not received at all. Encryption can be used to guarantee the integrity of information. With encryption, data is protected throughout transmission. The sender will transmit the information as encrypted data. The recipient will have a decryption key that they will use to decrypt the message they receive. With encrypted data, even it is intercepted; the hacker will still have the capability of accessing the contents of the message as they will be lacking the encryption key. (Axelrod, Bayuk, & Schutzer, 2012).
Data availability is when data can be accessed by authorized users at any time they need to do so. Every member of the company and any other stakeholders that need to have to access the data should be able to do so. Availability is important for ensuring that businesses are able to continue with their operations as smoothly as possible. Access to all of its data and its information technology assets is the goal of this aspect of the Triad. For an organization like Knight, access to its system is two pronged. First, is the access that is granted to its employees to access company’s data when doing their jobs, secondly, is the access granted to its customers who must have round the clock access to the company’s website so that they can shop. Both of these two accesses need to be maintained at all times if the company wishes to be successful. Threats to availability can also be viewed two-fold, first are external factors originating from outside the company. These include everything from hackers to natural disasters. From virus attacks meant to shut down the system to distributed denial of service attacks which overwhelm the system with illegitimate requests which failing to be processed lead to the system shutting down. From inside the company, unavailability can be as a result of poor bandwidth that affects access to cloud resources to power failure that lack backups. Ensuring availability is done by among other things having backup options of power, installing antivirus software, installing and configuring a strong firewall. These solutions should be tested every once on a while to ensure they up to the task and can be relied upon. This will make that the company will have access to its resources at all times and therefore able to keep business going. (Axelrod, Bayuk, & Schutzer, 2012).
Figure 4 - Network Components

Ethics in the Network
Employee ethics are usually a contentious for any organization. Simply requiring employees to adhere to high ethical standard will not be enough, hence the need for enforcing them. A tried and tested way for doing this has been the use of employee confidentiality agreements. These are legally binding documents that require the signatories to abide by the terms set out in them. Any breach of the terms will be reasonable grounds to institute legal proceedings against the breaching party. The ethics requirements of a company can then be incorporated into such agreements (Patrignani, & Whitehouse, 2015).
Password usage is mandatory in most computer systems for security purposes. This is meant to ensure that all access to the system is done under a secure infrastructure so as to keep out any unauthorized parties. This can however be jeopardized by those that fail to implement strong passwords, leaving the system vulnerable by the simple passwords. Employees should be taught on how to select strong passwords that don’t allude to familiar everyday objects or names that could be tied to the employee. They should be long and include alphanumeric characters as well as special characters (Patrignani, & Whitehouse, 2015).
References
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Axelrod, C. W., Bayuk, J. L., & Schutzer, D. (2012). Enterprise information security and privacy. Boston: Artech House.
Shinde, S. S. (2014). Computer network. New Delhi: New Age International Ltd.
Patrignani, N., & Whitehouse, D. (2015). Slow tech: bridging computer ethics and business ethics. Information Technology & People, 28(4), 775-789.



