Recommended Action to Address a Recent E-Commerce Threat
DDoS Attacks to E-Commerce Domain
1. An e-commerce threat identification 2
2. Diagram depicting mechanism of DDoS attacks on e-commerce system 4
3. Actual or Potential Consequences of DDoS Attacks to E-Commerce 7
4. Risk Assessment to the E-Commerce DDoS Attacks 8
5. References 10
As known to many, in today’s world, market of e-commerce has been growing rapidly in the global market and the pace of growth is expected to increase in the future, (Tamimi, R.; Mohammad Pour Zarandi 2013). On this tracked platform of business, companies have been facing security threats continuously due to this growing phase of e-commerce where many e-commerce organizations or companies have been growing their business throughout the world. In my discussion in this paper one of the e-commerce threat that was recognized of late in an Indian e-commerce company Flipkart, where we are told the website of the Indians largest e-commerce company Flipkart was attacked severally by an organized hacker groups who their aim was to use any helpless any vulnerability within the Flipkart system but unlikely every attack was effectively secured, (Shilpa Phadnis 2014).
It was established that the attack was DDoS, i.e. distributed denial of services threats that intended to include several number of damaged computer systems which were available within the company premises which were located in ‘Bengaluru’, a high-tech city in south India or we can say IT(i.e. Information Technology) hub in India. What was been used in the attack was a single target with the purpose of denying services to end users of the targeted system, for instance server would get hang instead of respond even virtually it would show that users’ data like; card information had been transferred but actual they would have gone through the systems of attackers.
The hackers group with their attacking threat was also aiming at company’s e-commerce portals, users credit card detailed data, banks and payment gateways that could be easily achieved by DDoS attacks even other ways of hacker attacks, especially to give services unavailable to their customers or to withdraw important data from the company all of them ultimately goal to gain money and huge financial losses to these type of companies or customers.
In addition, The International Council of E-Commerce Consultants (i.e. EC Council), one of the biggest confirmation bodies for the data security experts, said that, it was the inclusion of SQL injection attacks with DDoS, where SQL injection attacks were utilized to either increase unapproved access to the database or to recover the data specifically from databases. Where with the assistance of SQL injection, it could give aggressors the entrance to their databases, whereby they could erase, include or change client/item records or could take the touchy client data like card data if client officially spared with web based business account.
2. Diagram depicting mechanism of DDoS attacks on e-commerce systemWith the use of Denial of Service (DoS) attacks, the principle intention of attackers, was to deny the customers services provided on the E-Commerce servers by the e-commerce companies i.e. genuine rejection to the customers' services. There was no genuine intent to cause damage to files or to the file system of the organization like as through SQL injection, however the objective was to literally close the E-Commerce server or down the servers for a time being. This happened just when a massive measure of invalid information was sent to these servers or server, because servers had their own strength to handle the requests as servers handle and processes, such a large number of requests had there much data at any settled time, where server was unable to keep with the data and causes the information overflow. It resulted as server became 'confused', and subsequently closed down and attackers could gain up that data of the customers' Denial of Service Attacks and Mitigation Techniques (2011).
Moreover, Distributed Denial of Service (DDoS) which also refers to Denial of Service Attack implies that systems or several computers are used to launch an attack on a particular E-Commerce server as attackers tried with Flipkart’s server. As know computers that are used to launch these attacks are referred to as zombies. A master host computer controls these zombie computers where master host computer which instructs the zombie computers to launch the attack on the respective E-Commerce Server and resulted as, the server shuts down because of the massive bombardment of the bad information and data being sent from those “zombie” computers to hackers database or file system and DDoS is diagrammed as follows, (Lee Garber 2000).
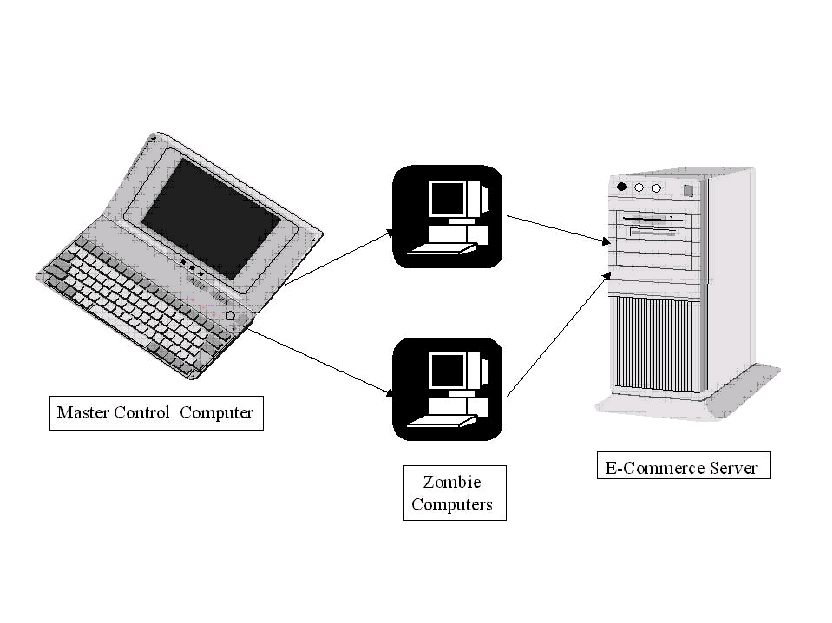
In India's, e-commerce sales market are in blast and generating the revenue to the nation and also for worldwide clients where these Flipkart type of enormous e-commerce organization keeping numerous clients belong from the worldwide market to India where these assaults are likely to increase commensurately and may have huge effect on money related market and ultimately may effect to a major misfortune to the economy to the nation and worldwide clients. Moreover, Customers may likewise lose their confidential data which they keep with these e-commerce account.
In the event that we think on technical prospective, where there might be chances to break software or hardware like; DDoS assaults may crash the information of E-Commerce servers even the vast majority of the companies have back or recovery terminology however these assaults could be possible chance to break the software and hardware systems even with the blend of SQL injection, it may be possible to hack whole the database of the E-Commerce server of those companies where companies need a special attention to control and screen all through the business and keep the track of each and every movement of any outside users. Therefore, there is a critical requirement to mitigate the dangers before these type of system vulnerable threats.
4. Risk Assessment to the E-Commerce DDoS AttacksRisk identification is the first step in the proactive risk management process according to risk management guide for information technology systems (2002). It normally give chances/opportunities, indicators, and information that can allow us to organize the mitigation techniques against possible threats. Therefore, this process ensures that each risk requiring a response has an owner monitoring the responses, although we may delegate implementation of a response to Flipkart DDoS Attacks to E-Commerce Server as below:
Conduct a company-wide DDoS risk assessment, i.e. first identify the risks then impact analysis for the risk and then go ahead with risk mitigation.
Create an action plans to prepare for and respond to DDoS attacks to E-Commerce Server i.e. if any fraud trying to put many requests simultaneously then there should be mechanism to monitor and handle all.
Know the infrastructure components inside and outside i.e. it’s important to know all resources and equipment on the network, along with the strengths and weaknesses of each component should be monitor.
Understand ISP options for DDoS mitigation and implement the rules of DDoS attacks on E-Commerce Webs.
There should be post attack analysis and leverage to monitor and managed the e- commerce services.
Risk management guide for information technology systems (2002), National Institute of Standards and Technology, Special Publication 800-30, pp. 34-47. Retrieved From:
http://csrc.nist.gov/publications/nistpubs/800-30/sp800-30.pdf
Lee Garber (2000), Denial-of-Service Attacks, Rip the Internet, Retrieved From:
http://www.computer.org/csdl/mags/co/2000/04/r4012.pdf
Tamimi, R.; Mohammad Pour Zarandi (2013), "The application of web usage mining in E-commerce security", e-Commerce in Developing Countries: With Focus on e-Security (ECDC), 7th International Conference on, On page(s): 1 - 8
Denial of Service Attacks and Mitigation Techniques (2011), Real-time implementation with detailed analysis, Retrieved From:
http://www.sans.org/reading room/whitepapers/detection/denial-service-attacks-mitigation-techniques-real-time-implementation-detailed-analysi-33764
Shilpa Phadnis (2014), How Flipkart fighting off cyberattacks? Retrieved From:
http://retail.economictimes.indiatimes.com/news/e-commerce/e-tailing/how-flipkart-fighting-off-cyberattacks/31144157



